Permissioned blockchains restrict access to authorized participants, enhancing security and compliance for enterprise use cases by controlling who can validate transactions and view data. In contrast, permissionless blockchains allow anyone to participate in the network, promoting decentralization and transparency but requiring consensus mechanisms like proof of work or proof of stake to secure the network. The choice between permissioned and permissionless blockchains depends on the desired balance between control, security, scalability, and openness.
Table of Comparison
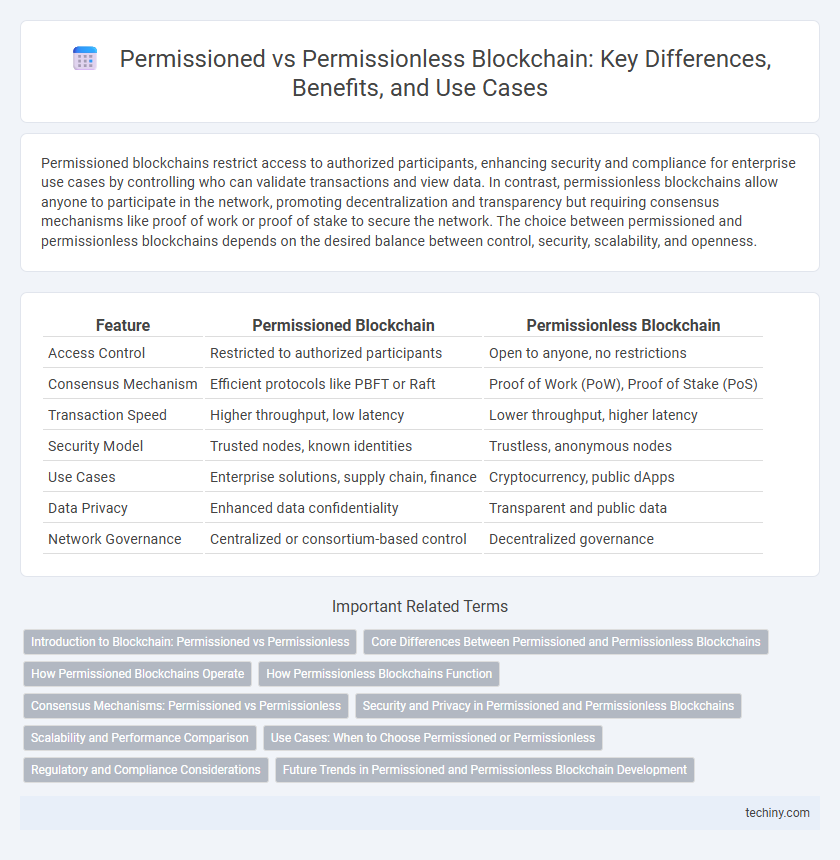
| Feature | Permissioned Blockchain | Permissionless Blockchain |
|---|---|---|
| Access Control | Restricted to authorized participants | Open to anyone, no restrictions |
| Consensus Mechanism | Efficient protocols like PBFT or Raft | Proof of Work (PoW), Proof of Stake (PoS) |
| Transaction Speed | Higher throughput, low latency | Lower throughput, higher latency |
| Security Model | Trusted nodes, known identities | Trustless, anonymous nodes |
| Use Cases | Enterprise solutions, supply chain, finance | Cryptocurrency, public dApps |
| Data Privacy | Enhanced data confidentiality | Transparent and public data |
| Network Governance | Centralized or consortium-based control | Decentralized governance |
Introduction to Blockchain: Permissioned vs Permissionless
Permissioned blockchains restrict participation to authorized users, enhancing security and control for enterprise applications, while permissionless blockchains allow anyone to join and validate transactions, promoting decentralization and transparency. Permissioned systems often utilize consensus mechanisms like Practical Byzantine Fault Tolerance (PBFT) for faster transaction processing, contrasting with permissionless blockchains that rely on Proof of Work (PoW) or Proof of Stake (PoS) for trustless participation. The choice between permissioned and permissionless blockchains depends on specific use cases, balancing scalability, governance, privacy, and decentralization.
Core Differences Between Permissioned and Permissionless Blockchains
Permissioned blockchains restrict network access to approved participants, enabling controlled governance and enhanced privacy, while permissionless blockchains allow anyone to join and validate transactions, promoting decentralization and transparency. Permissioned blockchains typically use consensus mechanisms like Practical Byzantine Fault Tolerance (PBFT) for efficiency, whereas permissionless blockchains rely on Proof of Work (PoW) or Proof of Stake (PoS) to secure trust trustless environments. Scalability and transaction speed often favor permissioned blockchains due to limited validators, contrasting with the broader but slower networks of permissionless systems.
How Permissioned Blockchains Operate
Permissioned blockchains operate using a controlled network where access is restricted to verified participants, enhancing security and compliance with regulatory requirements. Nodes in permissioned blockchains are pre-approved, allowing for faster consensus mechanisms such as Practical Byzantine Fault Tolerance (PBFT) or Raft, which improve transaction speed and reduce energy consumption compared to permissionless systems. This controlled environment enables enterprises to maintain data privacy and enforce governance policies while still benefiting from decentralization and immutability inherent to blockchain technology.
How Permissionless Blockchains Function
Permissionless blockchains operate on a decentralized network where anyone can join, validate transactions, and participate without needing approval or permission from a central authority. These blockchains rely on consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS) to secure the network and ensure transaction integrity. Their open accessibility enhances transparency and resilience but requires robust cryptographic protocols to prevent malicious activities.
Consensus Mechanisms: Permissioned vs Permissionless
Permissioned blockchains utilize consensus mechanisms like Practical Byzantine Fault Tolerance (PBFT) and Raft, which offer faster transaction finality and higher throughput by restricting validators to known, trusted entities. Permissionless blockchains rely on consensus algorithms such as Proof of Work (PoW) and Proof of Stake (PoS), enabling decentralized validation but often resulting in slower confirmation times and higher energy consumption. The trade-off between these consensus approaches impacts scalability, security, and network trust models within blockchain ecosystems.
Security and Privacy in Permissioned and Permissionless Blockchains
Permissioned blockchains enhance security and privacy by restricting network access to verified participants, enabling controlled data sharing and governance mechanisms that prevent unauthorized transactions. Permissionless blockchains offer transparency and decentralization but face increased risks from malicious actors due to open network access and reliance on cryptographic consensus methods like proof-of-work or proof-of-stake for security. Privacy in permissionless systems is limited, often requiring additional protocols such as zero-knowledge proofs or mixing services to protect user identities and transaction details.
Scalability and Performance Comparison
Permissioned blockchains typically offer higher scalability and improved performance due to controlled access and faster consensus algorithms such as Practical Byzantine Fault Tolerance (PBFT), enabling them to handle thousands of transactions per second with low latency. In contrast, permissionless blockchains like Bitcoin and Ethereum rely on resource-intensive proof-of-work mechanisms, limiting throughput to around 7 to 30 transactions per second and resulting in higher confirmation times. The centralized validator structure in permissioned blockchains reduces computational overhead and network congestion, making them suitable for enterprise applications requiring efficient scalability and real-time data processing.
Use Cases: When to Choose Permissioned or Permissionless
Permissioned blockchains are ideal for enterprise use cases requiring enhanced privacy, regulatory compliance, and controlled access, such as supply chain management, banking, and healthcare data sharing. Permissionless blockchains excel in decentralized applications, cryptocurrencies, and public finance scenarios where transparency, censorship resistance, and open participation are critical. Selecting between permissioned and permissionless depends on the need for scalability, trust model, and governance structure aligned with specific business objectives.
Regulatory and Compliance Considerations
Permissioned blockchains offer enhanced regulatory compliance by restricting access to verified participants, facilitating identity verification, and enabling more straightforward implementation of governance policies. Permissionless blockchains, while promoting decentralization and transparency, present challenges for regulators due to anonymous participation and difficulty in enforcing anti-money laundering (AML) and know-your-customer (KYC) requirements. Enterprises operating in heavily regulated industries often prefer permissioned blockchains to ensure data privacy, auditability, and adherence to jurisdiction-specific legal frameworks.
Future Trends in Permissioned and Permissionless Blockchain Development
Permissioned blockchains are increasingly integrating advanced privacy-preserving technologies like zero-knowledge proofs to enhance enterprise data security, while permissionless blockchains prioritize scalability improvements through layer-2 solutions and sharding to support mass adoption. Hybrid models combining features of both permissioned and permissionless systems are emerging to balance decentralization with regulatory compliance, addressing diverse industry needs. Interoperability protocols and cross-chain communication advancements are set to accelerate the seamless transfer of digital assets and information across heterogeneous blockchain networks, driving future growth in blockchain ecosystems.
Permissioned blockchain vs Permissionless blockchain Infographic
 techiny.com
techiny.com