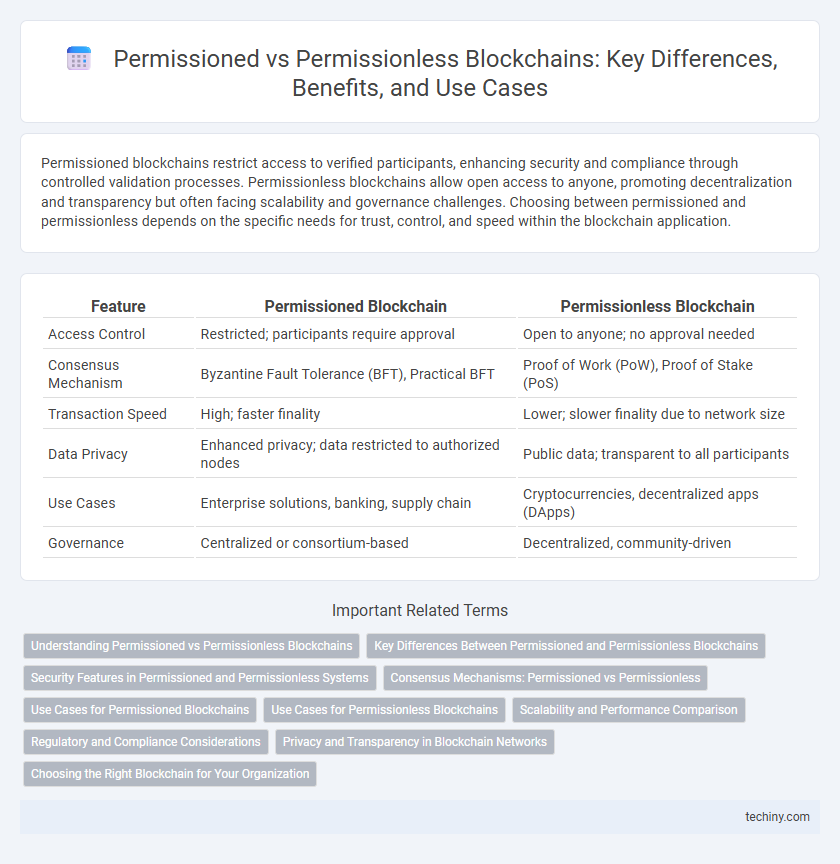
Permissioned blockchains restrict access to verified participants, enhancing security and compliance through controlled validation processes. Permissionless blockchains allow open access to anyone, promoting decentralization and transparency but often facing scalability and governance challenges. Choosing between permissioned and permissionless depends on the specific needs for trust, control, and speed within the blockchain application.
Table of Comparison
| Feature | Permissioned Blockchain | Permissionless Blockchain |
|---|---|---|
| Access Control | Restricted; participants require approval | Open to anyone; no approval needed |
| Consensus Mechanism | Byzantine Fault Tolerance (BFT), Practical BFT | Proof of Work (PoW), Proof of Stake (PoS) |
| Transaction Speed | High; faster finality | Lower; slower finality due to network size |
| Data Privacy | Enhanced privacy; data restricted to authorized nodes | Public data; transparent to all participants |
| Use Cases | Enterprise solutions, banking, supply chain | Cryptocurrencies, decentralized apps (DApps) |
| Governance | Centralized or consortium-based | Decentralized, community-driven |
Understanding Permissioned vs Permissionless Blockchains
Permissioned blockchains restrict network access to authorized participants, enhancing privacy and control for enterprises handling sensitive data. Permissionless blockchains allow anyone to join and validate transactions, promoting decentralization and transparency but often facing scalability challenges. Understanding the trade-offs between permissioned and permissionless blockchains is crucial for selecting the appropriate platform based on security, governance, and use case requirements.
Key Differences Between Permissioned and Permissionless Blockchains
Permissioned blockchains restrict network access to authorized participants, enhancing privacy and control, whereas permissionless blockchains allow anyone to join and validate transactions, promoting decentralization and transparency. Permissioned networks offer faster transaction speeds and scalable governance models due to controlled consensus mechanisms, while permissionless systems rely on resource-intensive consensus protocols like Proof of Work or Proof of Stake. Security in permissioned blockchains depends on trust between known entities, while permissionless blockchains use cryptographic algorithms and economic incentives to ensure network integrity without central authority.
Security Features in Permissioned and Permissionless Systems
Permissioned blockchain systems enhance security through controlled access, ensuring that only verified participants can validate transactions, reducing risks of malicious attacks or fraudulent activities. Permissionless blockchains rely on decentralized consensus mechanisms like Proof of Work or Proof of Stake to secure the network, enabling trustless interactions but often facing scalability and energy consumption challenges. The distinct security models reflect trade-offs between transparency, control, and resilience against unauthorized actions in both permissioned and permissionless environments.
Consensus Mechanisms: Permissioned vs Permissionless
Permissioned blockchains utilize consensus mechanisms such as Practical Byzantine Fault Tolerance (PBFT) and Tendermint, designed for environments where participants are known and trusted, enabling faster transaction finality and improved scalability. Permissionless blockchains rely on consensus algorithms like Proof of Work (PoW) and Proof of Stake (PoS), which enable decentralized validation by anonymous participants, enhancing network security through economic incentives and cryptographic puzzles. The choice between permissioned and permissionless consensus mechanisms largely depends on the desired balance between trust, censorship resistance, and transaction throughput within the blockchain network.
Use Cases for Permissioned Blockchains
Permissioned blockchains are ideal for enterprises requiring controlled access, such as supply chain management, where participants need verified identities to ensure data integrity and traceability. Financial institutions leverage permissioned blockchains for secure interbank settlements and regulatory compliance due to their ability to restrict network participation. Healthcare systems utilize permissioned blockchains to protect patient data privacy while enabling secure information sharing among authorized parties.
Use Cases for Permissionless Blockchains
Permissionless blockchains enable decentralized applications like cryptocurrency platforms, decentralized finance (DeFi), and supply chain transparency by allowing anyone to join and participate without restrictions. They support trustless environments where users transact directly, making them ideal for open financial systems and global digital asset exchanges. The open access and security features of permissionless networks drive innovation in sectors requiring censorship resistance and transparency.
Scalability and Performance Comparison
Permissioned blockchains offer enhanced scalability and higher transaction throughput by limiting network participation to verified entities, reducing consensus overhead and enabling faster processing. Permissionless blockchains, like Bitcoin and Ethereum, face scalability challenges due to decentralized node validation and energy-intensive consensus mechanisms such as Proof of Work. Layer 2 solutions and sharding technologies are being developed to improve the performance of permissionless networks without compromising decentralization.
Regulatory and Compliance Considerations
Permissioned blockchains offer enhanced regulatory compliance by restricting network access to verified participants, facilitating identity verification and adherence to data privacy laws such as GDPR. Permissionless blockchains, while promoting decentralization and transparency, pose challenges for compliance due to pseudonymous user activity and the difficulty of enforcing KYC/AML regulations across global, open networks. Enterprises and regulators prioritize permissioned models for applications requiring stringent governance, auditability, and controlled data sharing within legal frameworks.
Privacy and Transparency in Blockchain Networks
Permissioned blockchain networks enhance privacy by restricting access to verified participants, ensuring sensitive transaction data is only visible to authorized entities, while maintaining transparency through controlled data sharing. In contrast, permissionless blockchains promote full transparency by allowing anyone to join and verify transactions, but this openness can compromise privacy due to the public availability of transaction histories. Balancing privacy and transparency in blockchain networks depends on the use case, with permissioned systems favoring confidentiality for enterprise applications and permissionless systems supporting decentralized trust for public ecosystems.
Choosing the Right Blockchain for Your Organization
Choosing between permissioned and permissionless blockchains depends on the organization's security, scalability, and control requirements. Permissioned blockchains offer enhanced privacy and faster transaction speeds, making them suitable for enterprises needing regulatory compliance and restricted access. Permissionless blockchains provide decentralization and transparency ideal for open network participation and trustless environments.
Permissioned vs Permissionless Infographic
 techiny.com
techiny.com