A private key is a confidential code that grants access to blockchain assets and must be securely stored to prevent unauthorized use. The public key, derived from the private key, functions as an address for receiving transactions and can be openly shared without compromising security. Together, they enable secure, encrypted transactions on the blockchain, ensuring data integrity and user authentication.
Table of Comparison
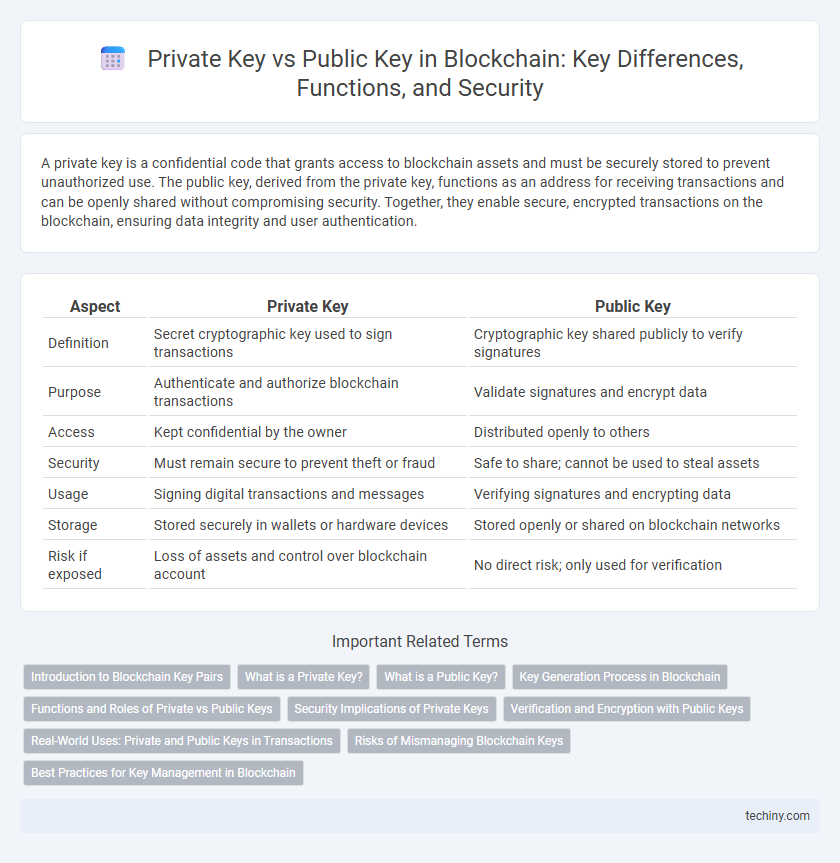
| Aspect | Private Key | Public Key |
|---|---|---|
| Definition | Secret cryptographic key used to sign transactions | Cryptographic key shared publicly to verify signatures |
| Purpose | Authenticate and authorize blockchain transactions | Validate signatures and encrypt data |
| Access | Kept confidential by the owner | Distributed openly to others |
| Security | Must remain secure to prevent theft or fraud | Safe to share; cannot be used to steal assets |
| Usage | Signing digital transactions and messages | Verifying signatures and encrypting data |
| Storage | Stored securely in wallets or hardware devices | Stored openly or shared on blockchain networks |
| Risk if exposed | Loss of assets and control over blockchain account | No direct risk; only used for verification |
Introduction to Blockchain Key Pairs
Blockchain key pairs consist of a private key and a public key that work together to secure digital transactions and identities. The private key is a secret alphanumeric code used to sign transactions, ensuring authenticity and ownership, while the public key is shared openly to verify these signatures without exposing sensitive information. This cryptographic pair is fundamental to decentralized systems, enabling secure, transparent, and tamper-proof data exchanges across blockchain networks.
What is a Private Key?
A private key is a secret alphanumeric code used in blockchain technology to authorize transactions and access digital assets within a cryptocurrency wallet. It acts as a cryptographic signature, enabling users to securely sign and verify transactions, ensuring ownership and control over their funds. Maintaining the confidentiality of the private key is crucial, as its exposure can lead to unauthorized access and loss of cryptocurrency.
What is a Public Key?
A public key is a cryptographic code used in blockchain to allow users to receive transactions securely without revealing their private key. It functions as an address on the blockchain, enabling others to send digital assets or data to the owner of the corresponding private key. Public keys are generated through complex mathematical algorithms from private keys, ensuring secure and transparent digital interactions.
Key Generation Process in Blockchain
The key generation process in blockchain involves creating a cryptographic pair consisting of a private key and a public key. The private key is a randomly generated number that must remain secret, serving as the foundation for transaction signing and identity verification. The public key is derived from the private key using elliptic curve cryptography (ECC), enabling others to verify signatures without exposing the private key.
Functions and Roles of Private vs Public Keys
Private keys enable users to sign transactions securely, proving ownership and granting authorization within the blockchain network. Public keys function as cryptographic identifiers that allow others to verify digital signatures and encrypt data sent to the private key holder. Together, private and public keys ensure transaction integrity, confidentiality, and authentication in decentralized blockchain ecosystems.
Security Implications of Private Keys
Private keys serve as the critical security credentials in blockchain systems, enabling authorized access to digital assets and transaction signing. Exposure or loss of a private key can lead to irreversible asset theft, as blockchain transactions are immutable and cannot be reversed. In contrast, public keys act as addresses for receiving funds, with no risk posed by their exposure due to their cryptographic design.
Verification and Encryption with Public Keys
Public keys facilitate encryption by allowing anyone to encrypt data that only the corresponding private key can decrypt, ensuring secure communication in blockchain networks. Verification relies on the private key to sign transactions, while the public key confirms the authenticity by validating these digital signatures without exposing the private key. This asymmetric cryptography framework underpins trust and security in blockchain by enabling secure identity verification and tamper-proof transaction validation.
Real-World Uses: Private and Public Keys in Transactions
Private keys enable secure authorization of blockchain transactions by allowing users to digitally sign and access their assets, ensuring exclusive control over funds. Public keys serve as unique identifiers that others use to verify the signature and send transactions securely without exposing the private key, enhancing transparency and trust. In real-world applications, private keys protect ownership and transaction validity, while public keys facilitate secure communication and asset transfer across distributed networks.
Risks of Mismanaging Blockchain Keys
Mismanaging blockchain private keys risks irreversible loss of assets since private keys grant exclusive access to cryptocurrency wallets and transactions. Public keys, while used to receive funds and verify signatures, pose fewer risks if exposed, but improper handling can lead to security vulnerabilities like phishing. Ensuring secure storage and backup of private keys is critical to prevent unauthorized access, theft, or permanent loss of blockchain assets.
Best Practices for Key Management in Blockchain
Secure key management in blockchain emphasizes safeguarding private keys with hardware wallets or cold storage to prevent unauthorized access, while public keys are openly shared to enable transparent transaction verification. Regularly updating backup methods and implementing multi-signature schemes enhance protection against loss or theft of private keys. Employing encryption and secure key generation protocols ensures integrity and confidentiality, maintaining trust and resilience in blockchain networks.
Private key vs Public key Infographic
 techiny.com
techiny.com