Bring Your Own Key (BYOK) empowers organizations to maintain control over encryption keys by generating and managing them independently, enhancing data security and compliance in cloud environments. Hardware Security Modules (HSMs) provide a dedicated, tamper-resistant hardware device designed to securely generate, store, and manage cryptographic keys, offering high assurance for key protection. Comparing BYOK with HSM highlights a trade-off between flexibility in key management and the physical security guarantees delivered by specialized hardware.
Table of Comparison
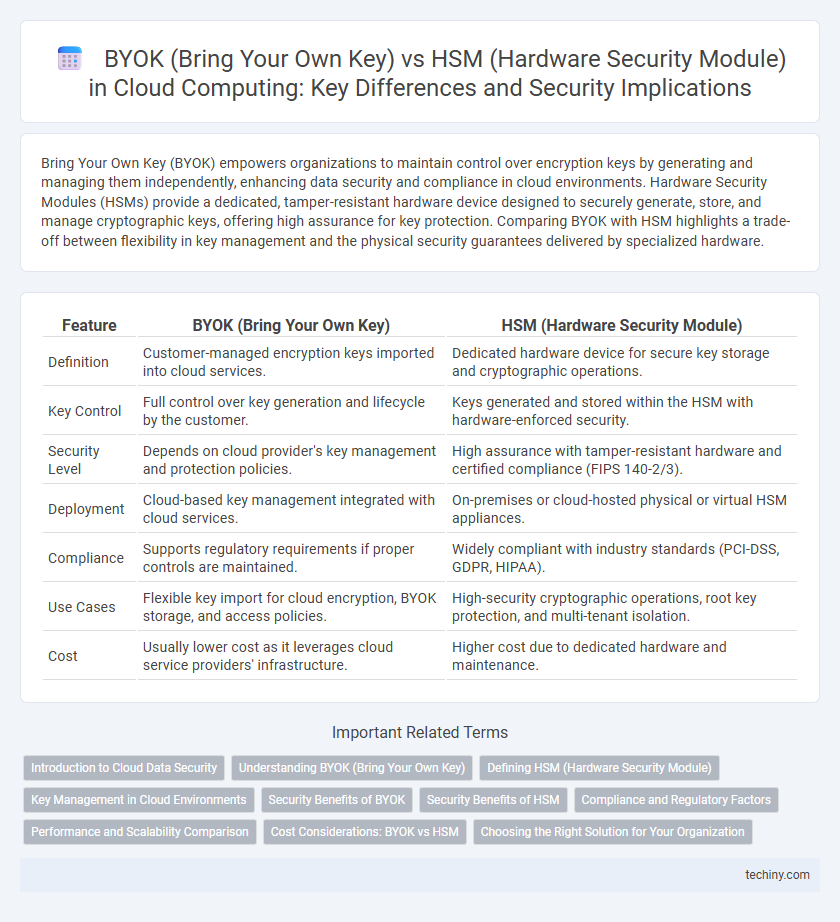
| Feature | BYOK (Bring Your Own Key) | HSM (Hardware Security Module) |
|---|---|---|
| Definition | Customer-managed encryption keys imported into cloud services. | Dedicated hardware device for secure key storage and cryptographic operations. |
| Key Control | Full control over key generation and lifecycle by the customer. | Keys generated and stored within the HSM with hardware-enforced security. |
| Security Level | Depends on cloud provider's key management and protection policies. | High assurance with tamper-resistant hardware and certified compliance (FIPS 140-2/3). |
| Deployment | Cloud-based key management integrated with cloud services. | On-premises or cloud-hosted physical or virtual HSM appliances. |
| Compliance | Supports regulatory requirements if proper controls are maintained. | Widely compliant with industry standards (PCI-DSS, GDPR, HIPAA). |
| Use Cases | Flexible key import for cloud encryption, BYOK storage, and access policies. | High-security cryptographic operations, root key protection, and multi-tenant isolation. |
| Cost | Usually lower cost as it leverages cloud service providers' infrastructure. | Higher cost due to dedicated hardware and maintenance. |
Introduction to Cloud Data Security
BYOK (Bring Your Own Key) empowers organizations to maintain control over their encryption keys when using cloud services by allowing them to generate and manage keys independently, enhancing data privacy and regulatory compliance. In contrast, Hardware Security Modules (HSMs) provide dedicated physical devices for secure key storage and cryptographic operations, offering tamper-resistant protection and high-assurance security in cloud environments. Combining BYOK with HSM technology ensures robust cloud data security by leveraging both customer-controlled key management and hardened hardware-based cryptographic safeguards.
Understanding BYOK (Bring Your Own Key)
BYOK (Bring Your Own Key) enables organizations to maintain full control over encryption keys by generating and managing them externally before uploading to a cloud provider, enhancing data security and compliance. Unlike HSMs (Hardware Security Modules) that provide physical devices for key management within a secured environment, BYOK allows flexible key lifecycle management through software-based processes integrated with cloud services. This approach ensures organizations meet regulatory requirements while leveraging cloud scalability and security features.
Defining HSM (Hardware Security Module)
Hardware Security Module (HSM) is a physical cryptographic appliance designed to securely generate, store, and manage digital keys used for encrypting data in cloud environments. HSMs provide tamper-resistant protection and high-assurance key lifecycle management, ensuring compliance with stringent security standards such as FIPS 140-2 or Common Criteria. These modules enable organizations to maintain control over cryptographic operations while offloading sensitive key handling from cloud service providers, differentiating from Bring Your Own Key (BYOK) strategies.
Key Management in Cloud Environments
BYOK (Bring Your Own Key) enables organizations to maintain control over encryption keys by allowing them to generate, manage, and revoke keys externally while leveraging cloud services, enhancing data sovereignty and compliance. HSM (Hardware Security Module) offers a dedicated, tamper-resistant hardware device for secure key storage and cryptographic operations within cloud environments, delivering high assurance of key protection and operational integrity. Effective key management in cloud environments often involves combining BYOK with HSM technologies to balance flexibility, security, and regulatory requirements.
Security Benefits of BYOK
BYOK (Bring Your Own Key) enhances cloud security by allowing organizations to maintain exclusive control over their encryption keys, reducing reliance on cloud provider key management and minimizing risks of unauthorized access. Unlike HSM-based solutions, BYOK enables seamless integration with existing internal key management policies, improving compliance and auditability. This approach ensures that encryption keys are not stored or generated within the cloud environment, significantly strengthening data confidentiality and regulatory adherence.
Security Benefits of HSM
Hardware Security Modules (HSMs) provide robust physical and logical protection for cryptographic keys, ensuring tamper-resistant key generation, storage, and management within a dedicated hardware appliance. Unlike Bring Your Own Key (BYOK) models where keys are customer-controlled but often stored in cloud environments, HSMs enforce strict access controls and hardware-based encryption, significantly reducing risks of key compromise and unauthorized access. This hardware-centric security approach aligns with compliance standards such as FIPS 140-2 and Common Criteria, making HSMs a preferred choice for enterprises demanding high-assurance key protection in cloud computing.
Compliance and Regulatory Factors
BYOK (Bring Your Own Key) empowers organizations to retain control over encryption keys, enhancing compliance with data privacy regulations such as GDPR and HIPAA by ensuring key sovereignty. HSM (Hardware Security Module) provides tamper-resistant physical devices that meet stringent FIPS 140-2/3 standards, offering robust security certifications required for compliance in highly regulated industries like finance and healthcare. Selecting between BYOK and HSM hinges on regulatory demands for key management transparency, auditability, and the level of certified protection mandated by governing bodies.
Performance and Scalability Comparison
BYOK (Bring Your Own Key) enables organizations to maintain control over encryption keys by integrating their own key management with cloud services, offering flexibility but potentially introducing performance latency due to key retrieval processes. In contrast, HSM (Hardware Security Module) provides dedicated cryptographic hardware that accelerates encryption and decryption operations, resulting in higher throughput and lower latency, which enhances overall performance. Scalability in BYOK depends heavily on cloud infrastructure and key management architecture, while HSM scalability often requires additional physical modules, making BYOK more adaptable for dynamic, large-scale cloud environments.
Cost Considerations: BYOK vs HSM
BYOK reduces upfront hardware expenses by enabling organizations to manage their encryption keys within existing cloud provider infrastructure, while HSM requires significant investment in physical devices and ongoing maintenance. BYOK offers scalable key management with minimal capital expenditure, making it cost-effective for dynamic cloud environments. In contrast, HSM delivers higher security assurances but entails higher total cost of ownership due to hardware procurement, deployment, and dedicated personnel costs.
Choosing the Right Solution for Your Organization
Choosing between BYOK (Bring Your Own Key) and HSM (Hardware Security Module) depends on your organization's security requirements and compliance needs. BYOK offers greater control by allowing businesses to manage their own encryption keys within cloud environments, enhancing data sovereignty and reducing reliance on cloud providers. In contrast, HSM provides robust, tamper-resistant hardware designed specifically for secure key storage and cryptographic operations, ideal for organizations requiring higher levels of physical security and regulatory compliance.
BYOK (Bring Your Own Key) vs HSM (Hardware Security Module) Infographic
 techiny.com
techiny.com