Cloud Security Posture Management (CSPM) continuously monitors cloud environments to identify misconfigurations and compliance risks, enhancing overall security posture. Cloud Access Security Broker (CASB) acts as a gateway between users and cloud services, enforcing security policies and protecting data from unauthorized access. Both solutions complement each other by addressing distinct aspects of cloud security, with CSPM focusing on configuration and compliance, and CASB managing access and data protection.
Table of Comparison
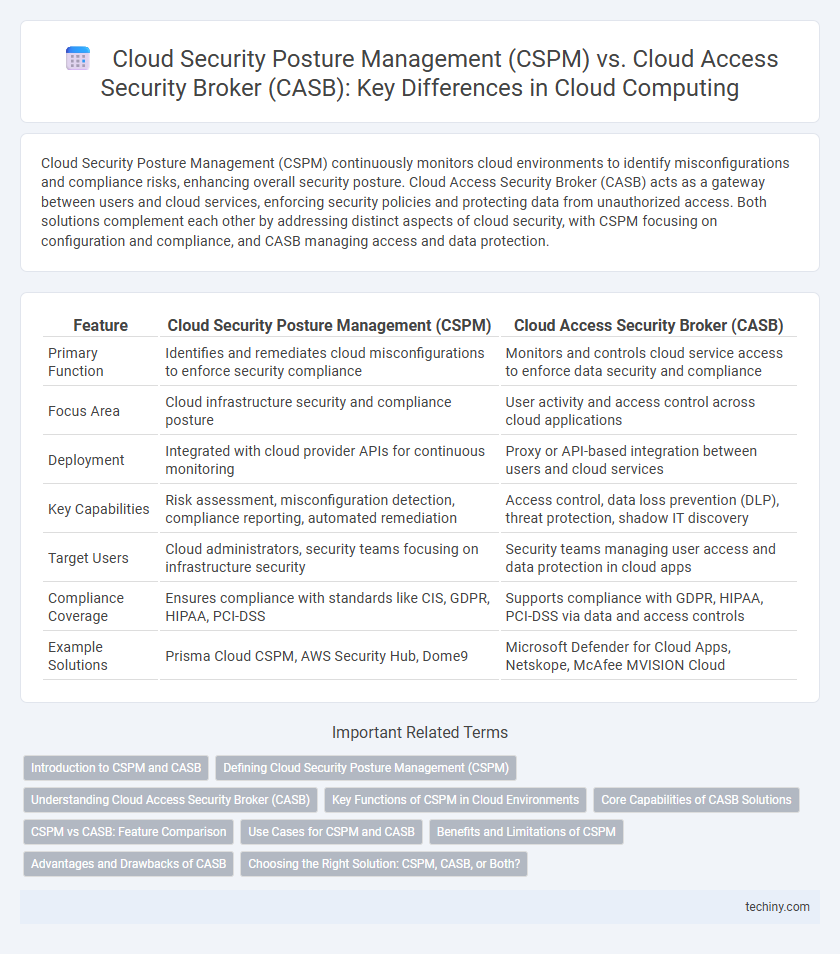
| Feature | Cloud Security Posture Management (CSPM) | Cloud Access Security Broker (CASB) |
|---|---|---|
| Primary Function | Identifies and remediates cloud misconfigurations to enforce security compliance | Monitors and controls cloud service access to enforce data security and compliance |
| Focus Area | Cloud infrastructure security and compliance posture | User activity and access control across cloud applications |
| Deployment | Integrated with cloud provider APIs for continuous monitoring | Proxy or API-based integration between users and cloud services |
| Key Capabilities | Risk assessment, misconfiguration detection, compliance reporting, automated remediation | Access control, data loss prevention (DLP), threat protection, shadow IT discovery |
| Target Users | Cloud administrators, security teams focusing on infrastructure security | Security teams managing user access and data protection in cloud apps |
| Compliance Coverage | Ensures compliance with standards like CIS, GDPR, HIPAA, PCI-DSS | Supports compliance with GDPR, HIPAA, PCI-DSS via data and access controls |
| Example Solutions | Prisma Cloud CSPM, AWS Security Hub, Dome9 | Microsoft Defender for Cloud Apps, Netskope, McAfee MVISION Cloud |
Introduction to CSPM and CASB
Cloud Security Posture Management (CSPM) automates the identification and remediation of risks across cloud infrastructures by continuously monitoring configurations and compliance with security policies. Cloud Access Security Broker (CASB) acts as an intermediary between cloud service users and providers, enforcing security policies including access control, data protection, and threat detection for cloud applications. Both CSPM and CASB play crucial roles in enhancing cloud security, with CSPM focusing on infrastructure posture and CASB securing user access and cloud data interactions.
Defining Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) is a critical technology designed to continuously monitor cloud environments for misconfigurations, ensuring compliance with industry standards and reducing security risks. CSPM automates the detection of vulnerabilities across cloud infrastructure, applications, and data, helping organizations enforce security policies and remediate issues before they lead to breaches. Unlike Cloud Access Security Broker (CASB), which focuses on securing cloud service usage and access controls, CSPM primarily targets the structural security posture of cloud environments.
Understanding Cloud Access Security Broker (CASB)
Cloud Access Security Broker (CASB) acts as a security policy enforcement point between cloud service users and cloud applications, providing visibility and control over data and threats across multiple cloud environments. CASB solutions enforce access controls, data loss prevention (DLP), and threat protection to ensure compliance with organizational security policies while enabling secure cloud adoption. By integrating with cloud platforms, CASBs offer real-time monitoring and analytics to detect anomalous behavior, prevent unauthorized access, and secure sensitive information in SaaS, PaaS, and IaaS environments.
Key Functions of CSPM in Cloud Environments
Cloud Security Posture Management (CSPM) continuously monitors cloud configurations to detect misconfigurations, compliance violations, and security risks across multi-cloud environments. It automates risk assessment by analyzing cloud resources, enforcing security policies, and providing remediation guidance. CSPM ensures real-time visibility and governance for cloud infrastructure, reducing attack surfaces and enhancing regulatory compliance in complex cloud ecosystems.
Core Capabilities of CASB Solutions
Cloud Access Security Broker (CASB) solutions provide core capabilities such as real-time visibility into cloud application usage, enforcement of granular access controls, and robust threat protection across multiple cloud services. CASBs enable data loss prevention (DLP), encryption, and compliance monitoring to secure sensitive information and ensure regulatory adherence within cloud environments. Integration with identity and access management (IAM) allows CASBs to detect and remediate risky user behavior, enhancing overall cloud security posture.
CSPM vs CASB: Feature Comparison
Cloud Security Posture Management (CSPM) focuses on identifying and remediating misconfigurations and compliance risks within cloud infrastructure, providing continuous monitoring of cloud environments for security policy adherence. In contrast, Cloud Access Security Broker (CASB) primarily controls and monitors user access to cloud applications, enforcing security policies such as data loss prevention, encryption, and threat protection at the access layer. CSPM excels in infrastructure-level security automation, while CASB offers granular visibility and control over cloud service usage and data access.
Use Cases for CSPM and CASB
CSPM primarily focuses on continuous risk assessment and compliance monitoring across cloud infrastructure, detecting misconfigurations and enforcing security policies to prevent data breaches. CASB is designed to provide visibility and control over cloud application usage, enforcing access policies, preventing data exfiltration, and protecting sensitive information within SaaS environments. Enterprises leverage CSPM to strengthen cloud infrastructure security posture, while CASB is applied to manage user access and secure cloud services against insider threats and shadow IT risks.
Benefits and Limitations of CSPM
Cloud Security Posture Management (CSPM) continuously monitors cloud environments to identify misconfigurations and compliance risks, enhancing overall security posture through automated remediation and comprehensive visibility. Its benefits include improved regulatory compliance and reduced risk of data breaches by detecting vulnerabilities before exploitation. Limitations of CSPM involve its focus primarily on configuration issues rather than real-time data access or user activity monitoring, which limits its effectiveness in preventing insider threats and advanced attacks without integration with other security tools.
Advantages and Drawbacks of CASB
Cloud Access Security Brokers (CASB) provide enhanced visibility and control over cloud service usage, enforcing security policies across multiple cloud environments and preventing data breaches by monitoring user activity in real-time. However, CASB solutions may introduce complexity in deployment and management, requiring integration with diverse cloud platforms and can sometimes result in performance bottlenecks. While CASBs excel at access control and compliance enforcement, they may lack comprehensive vulnerability assessments offered by Cloud Security Posture Management (CSPM).
Choosing the Right Solution: CSPM, CASB, or Both?
Choosing between Cloud Security Posture Management (CSPM) and Cloud Access Security Broker (CASB) depends on organizational security needs; CSPM excels at continuous risk assessment and compliance monitoring across cloud infrastructure, while CASB focuses on enforcing security policies and managing access to cloud applications. Enterprises with complex cloud environments and strict compliance requirements benefit from implementing both solutions to ensure comprehensive visibility, threat detection, and data protection. Integrating CSPM and CASB creates a layered defense strategy that enhances cloud security posture and access governance effectively.
Cloud Security Posture Management (CSPM) vs Cloud Access Security Broker (CASB) Infographic
 techiny.com
techiny.com