IAM Roles grant temporary permissions to entities like users, applications, or services, enabling secure access to cloud resources without sharing long-term credentials. IAM Policies define specific permissions and are attached to users, groups, or roles to control what actions are allowed or denied on resources. The combination of IAM Roles and Policies provides flexible, fine-grained access management essential for maintaining security and operational efficiency in cloud environments.
Table of Comparison
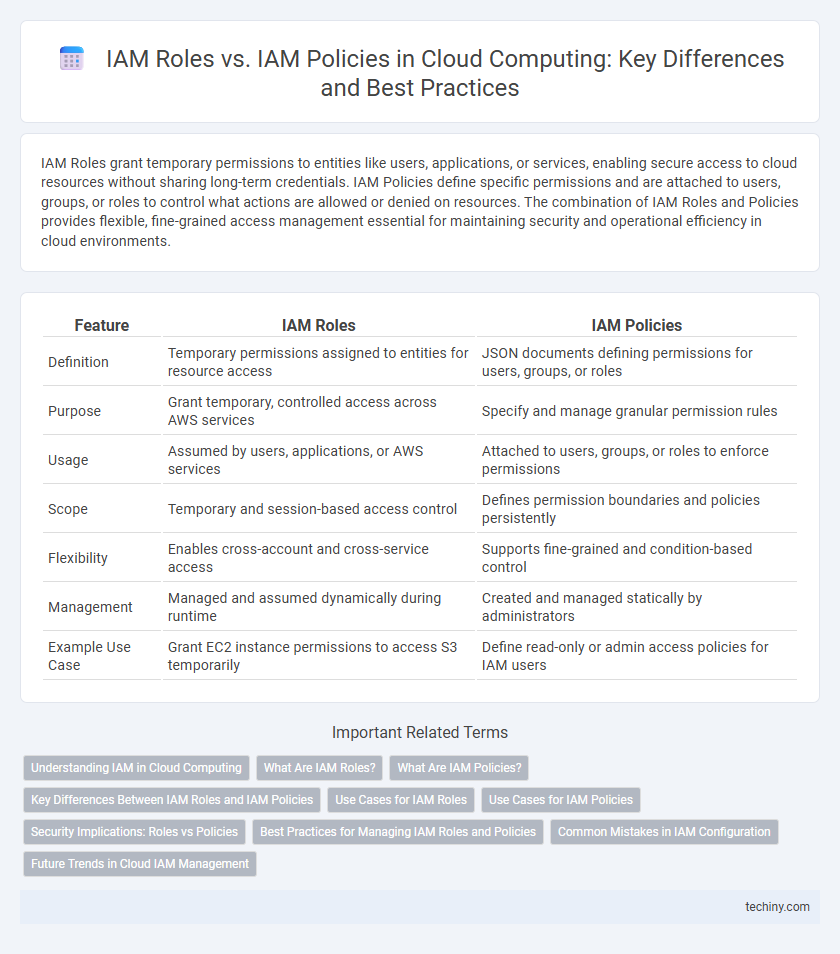
| Feature | IAM Roles | IAM Policies |
|---|---|---|
| Definition | Temporary permissions assigned to entities for resource access | JSON documents defining permissions for users, groups, or roles |
| Purpose | Grant temporary, controlled access across AWS services | Specify and manage granular permission rules |
| Usage | Assumed by users, applications, or AWS services | Attached to users, groups, or roles to enforce permissions |
| Scope | Temporary and session-based access control | Defines permission boundaries and policies persistently |
| Flexibility | Enables cross-account and cross-service access | Supports fine-grained and condition-based control |
| Management | Managed and assumed dynamically during runtime | Created and managed statically by administrators |
| Example Use Case | Grant EC2 instance permissions to access S3 temporarily | Define read-only or admin access policies for IAM users |
Understanding IAM in Cloud Computing
IAM roles define a set of permissions granted to entities such as users, applications, or services, enabling controlled access to cloud resources without sharing long-term credentials. IAM policies specify detailed permissions in JSON format, attached to roles or users to enforce access controls and fine-grained security management. Understanding the distinction between roles and policies is essential for implementing effective identity and access management strategies in cloud computing environments.
What Are IAM Roles?
IAM Roles in cloud computing define a set of permissions that grant entities temporary access to resources without sharing long-term credentials. These roles enable secure delegation and policy-based management by assigning specific privileges to services, users, or applications. Unlike IAM Policies, which are permission documents, IAM Roles are trusted identities that assume these policies to perform actions within cloud environments.
What Are IAM Policies?
IAM Policies are JSON documents that define permissions and specify what actions are allowed or denied on AWS resources. These policies can be attached to users, groups, or roles to control access and enforce security best practices. By using IAM Policies, organizations manage granular access controls, ensuring only authorized entities perform specific operations within cloud environments.
Key Differences Between IAM Roles and IAM Policies
IAM Roles are AWS identities with specific permissions assigned to them, allowing trusted entities like users, applications, or services to assume these roles temporarily for accessing resources securely. IAM Policies are JSON documents attached to users, groups, or roles that define fine-grained permissions specifying allowed or denied actions on AWS resources. The key difference lies in roles being assumed by trusted entities dynamically, while policies are static permission sets that govern what actions an identity can perform in the cloud environment.
Use Cases for IAM Roles
IAM Roles enable secure, temporary access to AWS resources without sharing long-term credentials, making them ideal for cross-account access, federated user access, and application permissions. Roles facilitate assigning permissions to AWS services like EC2 instances or Lambda functions to interact with other services securely. Use cases include enabling third-party service integrations, automating workflows, and managing permissions for users authenticating via external identity providers.
Use Cases for IAM Policies
IAM Policies in cloud computing define granular permissions assigned to users, groups, or roles to control access to specific resources such as S3 buckets, EC2 instances, or Lambda functions. These policies enable organizations to enforce least privilege security principles, allowing users to perform only the actions necessary for their job functions, thereby reducing the risk of unauthorized access. Common use cases include granting read-only access to storage resources, allowing specific API actions, or restricting access based on conditions like IP address or multi-factor authentication status.
Security Implications: Roles vs Policies
IAM roles provide temporary security credentials, minimizing the risk of long-term credential exposure, while IAM policies define granular permissions that control access but rely on proper attachment to users, groups, or roles to be effective. Misconfigured IAM roles can lead to privilege escalation through overly permissive trust relationships, whereas overly broad policies increase the attack surface by granting unnecessary permissions. Secure cloud environments enforce the principle of least privilege by combining narrowly scoped IAM policies with tightly controlled IAM roles to reduce potential security vulnerabilities.
Best Practices for Managing IAM Roles and Policies
Effective management of IAM roles and policies involves applying the principle of least privilege, ensuring users and services have only the permissions necessary to perform their tasks. Regularly auditing roles and policies helps identify and remove excessive or unused permissions, enhancing security posture. Implementing role-based access control (RBAC) streamlines permission assignment and reduces complexity in cloud environments.
Common Mistakes in IAM Configuration
Misconfiguring IAM Roles and IAM Policies often leads to excessive permissions or unintended access, increasing security risks in cloud environments. A frequent mistake is attaching overly permissive policies directly to users instead of using roles to enforce the principle of least privilege. Neglecting to regularly audit IAM policies and roles can result in privilege creep, making it critical to implement granular access controls and continuous monitoring.
Future Trends in Cloud IAM Management
Emerging trends in Cloud IAM management emphasize increased automation and AI-driven role assignment to enhance security and efficiency in IAM roles and IAM policies. Future IAM frameworks are expected to leverage machine learning algorithms for dynamic policy generation and real-time risk assessment, minimizing manual intervention. Integration of decentralized identity standards and context-aware access controls will redefine how IAM roles and policies adapt to evolving cloud infrastructures and regulatory requirements.
IAM Roles vs IAM Policies Infographic
 techiny.com
techiny.com