Identity and Access Management (IAM) provides a comprehensive framework for defining and managing user identities and their access across cloud resources. Role-Based Access Control (RBAC) simplifies permission management by assigning access rights based on user roles, enhancing security through predefined role policies. Combining IAM with RBAC ensures granular access control and efficient management of cloud environments, minimizing risks of unauthorized access.
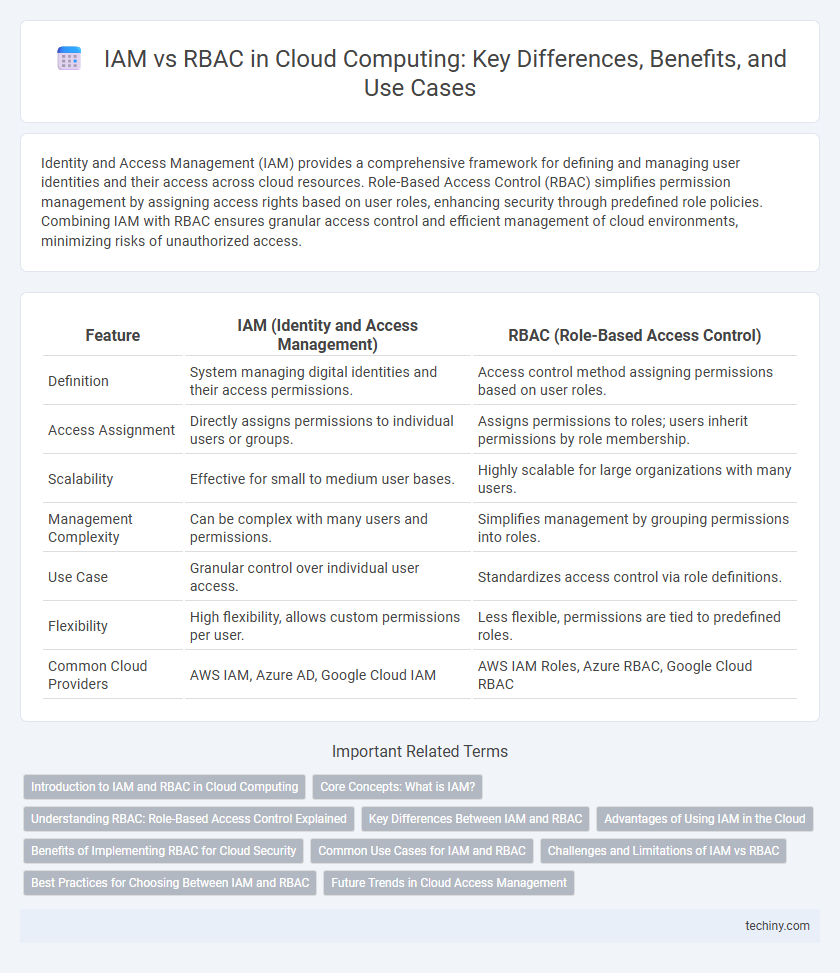
Table of Comparison
| Feature | IAM (Identity and Access Management) | RBAC (Role-Based Access Control) |
|---|---|---|
| Definition | System managing digital identities and their access permissions. | Access control method assigning permissions based on user roles. |
| Access Assignment | Directly assigns permissions to individual users or groups. | Assigns permissions to roles; users inherit permissions by role membership. |
| Scalability | Effective for small to medium user bases. | Highly scalable for large organizations with many users. |
| Management Complexity | Can be complex with many users and permissions. | Simplifies management by grouping permissions into roles. |
| Use Case | Granular control over individual user access. | Standardizes access control via role definitions. |
| Flexibility | High flexibility, allows custom permissions per user. | Less flexible, permissions are tied to predefined roles. |
| Common Cloud Providers | AWS IAM, Azure AD, Google Cloud IAM | AWS IAM Roles, Azure RBAC, Google Cloud RBAC |
Introduction to IAM and RBAC in Cloud Computing
Identity and Access Management (IAM) in cloud computing controls user authentication and resource access based on verified identities, ensuring secure and efficient permission handling. Role-Based Access Control (RBAC) simplifies access management by assigning permissions to roles instead of individual users, enhancing scalability and reducing administrative overhead. Both IAM and RBAC enable organizations to enforce security policies while managing cloud resource access effectively.
Core Concepts: What is IAM?
Identity and Access Management (IAM) is a framework of policies and technologies ensuring that the right individuals access specific cloud resources securely. IAM governs user identities, authentication, and permissions, enabling precise control over who can perform actions within a cloud environment. It differs from Role-Based Access Control (RBAC) by offering a broader scope, including identity lifecycle management and multi-factor authentication, beyond just role assignments.
Understanding RBAC: Role-Based Access Control Explained
Role-Based Access Control (RBAC) streamlines cloud security by assigning permissions based on user roles rather than individual identities, reducing administrative overhead and minimizing the risk of excessive access. RBAC frameworks categorize access rights according to organizational roles, ensuring that users only have the privileges necessary to perform their specific tasks within cloud environments. This method enhances compliance with security policies and supports efficient management of access controls in complex cloud infrastructures.
Key Differences Between IAM and RBAC
IAM (Identity and Access Management) provides a comprehensive framework for managing digital identities and controlling access across cloud environments, including authentication and authorization. RBAC (Role-Based Access Control) is a specific access control model within IAM that assigns permissions to users based on their roles, simplifying permission management. Key differences include IAM's broader scope encompassing identity lifecycle and policy enforcement, while RBAC focuses strictly on permission assignment through role hierarchies.
Advantages of Using IAM in the Cloud
IAM in cloud computing offers granular access control, enabling organizations to manage user identities and permissions securely across multiple services. It enhances security with multi-factor authentication and centralized identity management, reducing the risk of unauthorized access. IAM also supports scalability and compliance by automating permission assignments and ensuring policy enforcement across cloud environments.
Benefits of Implementing RBAC for Cloud Security
Implementing Role-Based Access Control (RBAC) in cloud computing enhances security by assigning permissions based on user roles, reducing the risk of unauthorized access and minimizing human error. RBAC simplifies management of user privileges in complex cloud environments, ensuring consistent enforcement of access policies across multiple cloud services. This approach improves compliance with regulatory requirements by providing clear audit trails and reducing privilege creep inherent in traditional Identity and Access Management (IAM) models.
Common Use Cases for IAM and RBAC
IAM enables centralized user authentication and access management across cloud environments, facilitating secure identity verification and policy enforcement. RBAC restricts system access based on assigned roles, streamlining permissions management for groups like administrators, developers, and auditors. Common use cases include IAM for managing multi-cloud identities and RBAC for enforcing least privilege access within cloud applications.
Challenges and Limitations of IAM vs RBAC
IAM systems often face challenges in managing complex, dynamic access requirements across large cloud environments, leading to potential over-permissioning or administrative overhead. RBAC, while simplifying access control through predefined roles, can struggle with flexibility in environments requiring fine-grained or context-aware access management, resulting in role explosion or excessive role maintenance. Both IAM and RBAC present limitations in scalability and adaptability, necessitating hybrid or advanced models like Attribute-Based Access Control (ABAC) to better address evolving cloud security needs.
Best Practices for Choosing Between IAM and RBAC
Choosing between IAM and RBAC depends on an organization's security requirements and operational complexity, with IAM offering granular, identity-focused access control and RBAC providing role-centric, scalable permissions management. Best practices recommend implementing RBAC for environments with stable roles and predictable access patterns, while leveraging IAM in dynamic scenarios demanding fine-grained, user-specific policies. Evaluating cloud platform capabilities, compliance needs, and administrative overhead ensures optimal alignment of access control strategy with organizational goals.
Future Trends in Cloud Access Management
Future trends in cloud access management emphasize the integration of Identity and Access Management (IAM) with Role-Based Access Control (RBAC) to enhance security and operational efficiency. Advances in AI-driven analytics enable dynamic role assignments and adaptive access policies, reducing risks of privilege escalation and insider threats. The rise of zero-trust architectures further accelerates the adoption of fine-grained, context-aware access controls combining IAM's identity verification with RBAC's permission structuring.
IAM vs RBAC Infographic
 techiny.com
techiny.com