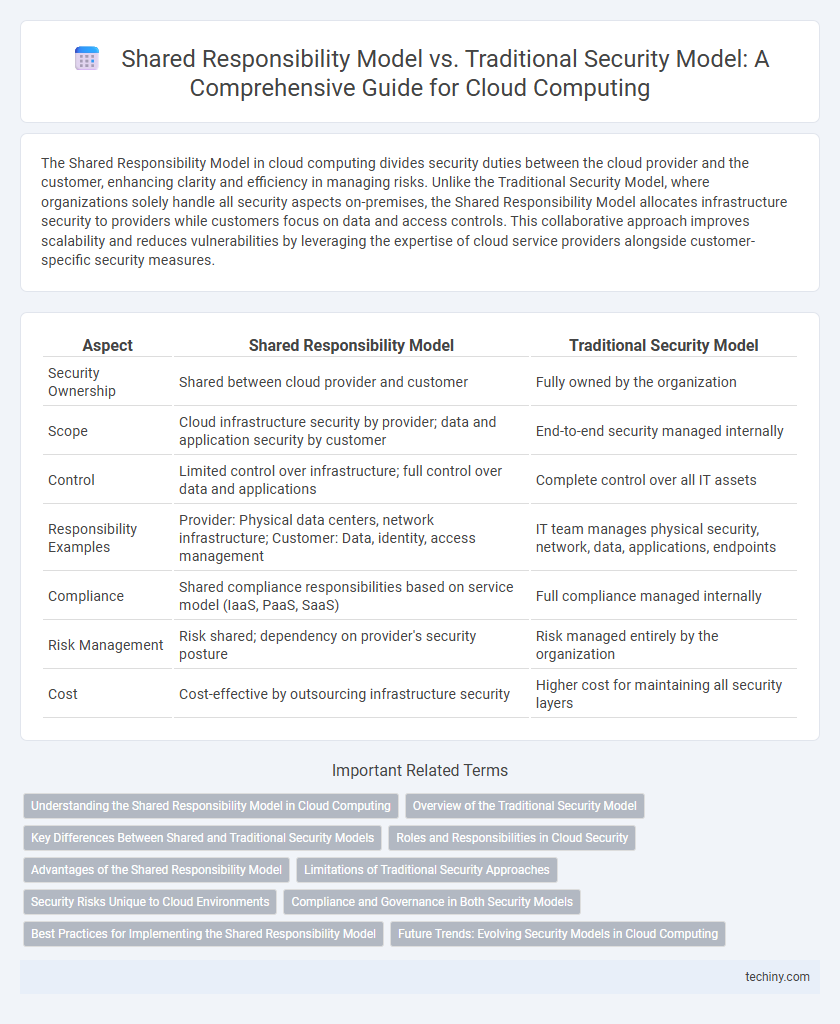
The Shared Responsibility Model in cloud computing divides security duties between the cloud provider and the customer, enhancing clarity and efficiency in managing risks. Unlike the Traditional Security Model, where organizations solely handle all security aspects on-premises, the Shared Responsibility Model allocates infrastructure security to providers while customers focus on data and access controls. This collaborative approach improves scalability and reduces vulnerabilities by leveraging the expertise of cloud service providers alongside customer-specific security measures.
Table of Comparison
| Aspect | Shared Responsibility Model | Traditional Security Model |
|---|---|---|
| Security Ownership | Shared between cloud provider and customer | Fully owned by the organization |
| Scope | Cloud infrastructure security by provider; data and application security by customer | End-to-end security managed internally |
| Control | Limited control over infrastructure; full control over data and applications | Complete control over all IT assets |
| Responsibility Examples | Provider: Physical data centers, network infrastructure; Customer: Data, identity, access management | IT team manages physical security, network, data, applications, endpoints |
| Compliance | Shared compliance responsibilities based on service model (IaaS, PaaS, SaaS) | Full compliance managed internally |
| Risk Management | Risk shared; dependency on provider's security posture | Risk managed entirely by the organization |
| Cost | Cost-effective by outsourcing infrastructure security | Higher cost for maintaining all security layers |
Understanding the Shared Responsibility Model in Cloud Computing
The Shared Responsibility Model in cloud computing allocates security duties between the cloud service provider and the customer, ensuring clear demarcation of responsibilities for infrastructure, platform, and application layers. Unlike the Traditional Security Model where organizations manage end-to-end security, cloud customers focus primarily on securing data, access management, and application configuration while providers handle physical infrastructure and foundational services. This model enhances security posture by leveraging provider expertise and scalable controls, reducing organizational complexity and risk exposure in cloud environments.
Overview of the Traditional Security Model
The Traditional Security Model places full responsibility for securing infrastructure, applications, and data on the organization managing the on-premises environment. Security measures include physical access controls, network firewalls, endpoint protection, and internal policies enforced directly by in-house IT teams. This model demands comprehensive resource allocation for hardware, software, and continuous monitoring to ensure compliance and threat mitigation.
Key Differences Between Shared and Traditional Security Models
The Shared Responsibility Model in cloud computing distributes security tasks between the cloud provider and the customer, where providers secure the infrastructure and customers manage data and access controls. In contrast, the Traditional Security Model places full responsibility on the organization for all security aspects, including hardware, software, network, and data protection. This key difference enables cloud users to leverage provider expertise for infrastructure security while focusing internal resources on application and data security.
Roles and Responsibilities in Cloud Security
The Shared Responsibility Model in cloud computing delineates security roles between cloud service providers and customers, where providers secure the infrastructure while customers manage data protection and access controls. In contrast, the Traditional Security Model places the entire security burden on the organization, encompassing infrastructure, applications, and data. Understanding these distinctions is critical for effective cloud security management and compliance.
Advantages of the Shared Responsibility Model
The Shared Responsibility Model in cloud computing enhances security by clearly defining the division of security tasks between cloud providers and customers, reducing ambiguity and gaps in protection. Unlike the Traditional Security Model, which places the entire security burden on the organization, the shared model leverages the provider's expertise in infrastructure security while allowing customers to focus on securing their data and applications. This collaboration improves overall resilience, accelerates compliance adherence, and optimizes resource utilization for more robust cloud security.
Limitations of Traditional Security Approaches
Traditional security models primarily rely on perimeter-based defenses, which struggle to address the dynamic and distributed nature of cloud environments. These approaches often lack granular control and visibility over user activities, data access, and infrastructure changes, leading to increased vulnerabilities. The rigid security boundaries in traditional models inhibit scalability and adaptability, failing to meet the complex security demands of modern cloud computing.
Security Risks Unique to Cloud Environments
Cloud computing introduces distinctive security risks that differ significantly from traditional security models due to its shared responsibility framework, where cloud providers manage infrastructure security while customers secure data and applications. Risks such as misconfigured cloud storage, insecure APIs, and insider threats become more prevalent because control is distributed across multiple parties in diverse environments. Understanding this division of duties is crucial to mitigating vulnerabilities inherent to cloud ecosystems, including data breaches and compliance failures.
Compliance and Governance in Both Security Models
In cloud computing, the Shared Responsibility Model delineates compliance and governance duties between cloud providers and customers, enhancing regulatory adherence through clearly defined roles. Traditional security models place full accountability on the enterprise, often complicating governance due to siloed infrastructure control. Cloud models improve transparency and auditability, leveraging provider certifications such as ISO 27001, SOC 2, and GDPR compliance to streamline security governance.
Best Practices for Implementing the Shared Responsibility Model
Implementing the Shared Responsibility Model in cloud computing requires clearly defining security roles between providers and customers, ensuring compliance with cloud-specific regulations such as GDPR and HIPAA. Best practices include leveraging automated security tools for continuous monitoring, enforcing strong identity and access management (IAM) policies, and applying encryption both in transit and at rest to protect data. Regular security audits and employee training further enhance defense against threats by addressing gaps unique to the hybrid environment of cloud and on-premises infrastructure.
Future Trends: Evolving Security Models in Cloud Computing
Future trends in cloud computing security emphasize the evolution from traditional security models to the Shared Responsibility Model, where cloud providers and customers delineate security tasks to enhance protection. Increasingly sophisticated threat landscapes drive adoption of adaptive frameworks integrating automation, AI-driven threat detection, and continuous compliance monitoring. This collaborative approach optimizes risk management by balancing provider-managed infrastructure security with customer-controlled data and access security.
Shared Responsibility Model vs Traditional Security Model Infographic
 techiny.com
techiny.com