Biometric authentication offers enhanced security by using unique physical or behavioral traits such as fingerprints or facial recognition, reducing the risk of password theft and phishing attacks. Password authentication remains vulnerable due to weak, reused credentials and is often compromised by brute force or social engineering methods. Implementing biometric systems can significantly improve identity verification processes while minimizing human error and enhancing user convenience.
Table of Comparison
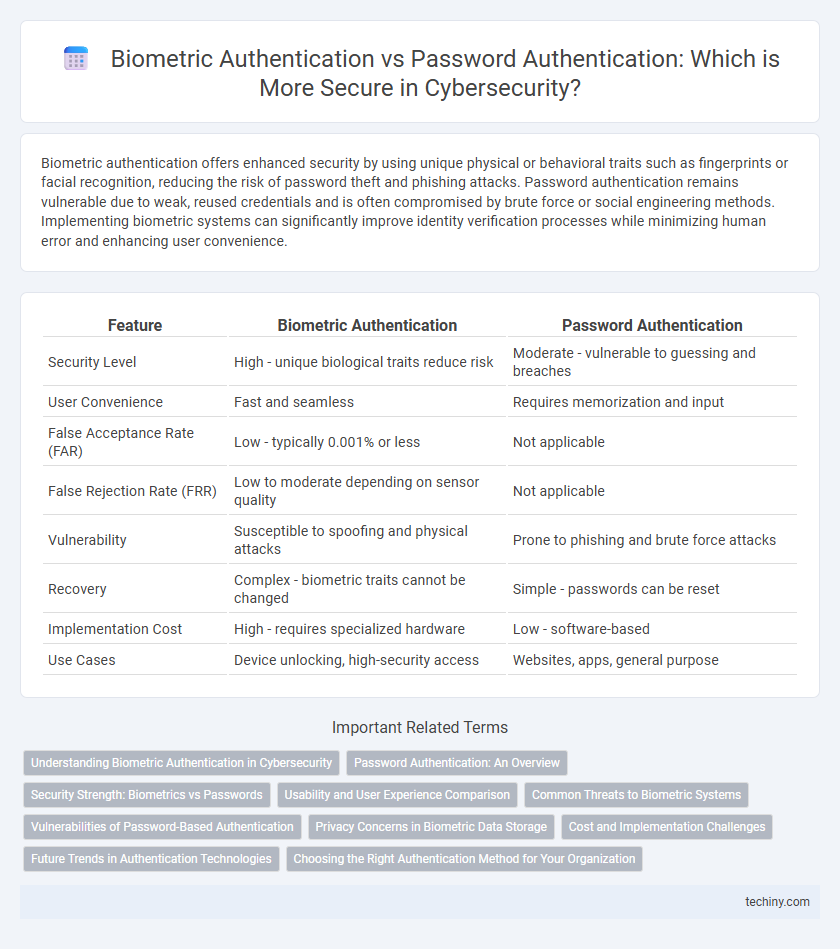
| Feature | Biometric Authentication | Password Authentication |
|---|---|---|
| Security Level | High - unique biological traits reduce risk | Moderate - vulnerable to guessing and breaches |
| User Convenience | Fast and seamless | Requires memorization and input |
| False Acceptance Rate (FAR) | Low - typically 0.001% or less | Not applicable |
| False Rejection Rate (FRR) | Low to moderate depending on sensor quality | Not applicable |
| Vulnerability | Susceptible to spoofing and physical attacks | Prone to phishing and brute force attacks |
| Recovery | Complex - biometric traits cannot be changed | Simple - passwords can be reset |
| Implementation Cost | High - requires specialized hardware | Low - software-based |
| Use Cases | Device unlocking, high-security access | Websites, apps, general purpose |
Understanding Biometric Authentication in Cybersecurity
Biometric authentication leverages unique physiological traits such as fingerprints, facial recognition, and iris patterns to verify user identity, offering enhanced security compared to traditional password methods vulnerable to hacking and phishing attacks. This technology integrates machine learning algorithms to analyze behavioral biometrics, providing continuous authentication that adapts to user patterns and reduces the risk of unauthorized access. The deployment of biometric authentication in cybersecurity frameworks significantly strengthens identity verification processes by minimizing reliance on easily compromised credentials.
Password Authentication: An Overview
Password authentication remains one of the most widely used methods for verifying user identity, relying on secret combinations of characters known only to the user. Despite its simplicity and ease of implementation, password authentication faces significant challenges such as susceptibility to brute force attacks, phishing, and credential theft. Enhancements like multi-factor authentication and password managers help mitigate these vulnerabilities and improve overall security posture.
Security Strength: Biometrics vs Passwords
Biometric authentication leverages unique physical traits such as fingerprints, facial recognition, and iris scans, offering a higher security strength by significantly reducing the risk of credential theft and replay attacks compared to traditional passwords. Password authentication remains vulnerable to brute force attacks, phishing, and credential reuse, while biometrics provide a non-transferable, hard-to-replicate security layer that enhances identity verification accuracy. Integrating biometric systems with multi-factor authentication further fortifies protection against unauthorized access in cybersecurity frameworks.
Usability and User Experience Comparison
Biometric authentication offers superior usability by enabling quick, contactless access using unique physiological traits such as fingerprints or facial recognition, minimizing user effort and reducing the risk of forgotten credentials. Password authentication often frustrates users with complex requirements, frequent resets, and vulnerability to phishing attacks, leading to a poorer overall user experience. Enhanced convenience and speed of biometric systems significantly improve user satisfaction and accessibility in cybersecurity applications.
Common Threats to Biometric Systems
Biometric systems face common threats such as spoofing attacks, where attackers use fabricated fingerprints or facial replicas to deceive sensors. Replay attacks intercept and reuse biometric data during transmission, compromising authentication integrity. Unlike passwords, biometric data is immutable, making recovery from breaches more challenging and emphasizing the need for robust anti-spoofing and encryption measures.
Vulnerabilities of Password-Based Authentication
Password-based authentication is vulnerable to various cyber threats such as brute force attacks, phishing, and credential stuffing, making it less secure compared to biometric methods. Passwords can be easily guessed, stolen, or leaked through data breaches, exposing sensitive information to unauthorized access. In contrast, biometric authentication leverages unique physical characteristics, reducing the risk of impersonation and enhancing security in identity verification processes.
Privacy Concerns in Biometric Data Storage
Biometric authentication stores unique biological data such as fingerprints, facial recognition, and iris scans, raising significant privacy concerns regarding data breaches and unauthorized access. Unlike passwords, biometric data is immutable, making compromised data impossible to reset or change, thus heightening risks of identity theft and long-term misuse. Secure encryption, decentralized storage solutions, and strict regulatory compliance like GDPR are essential to protect biometric information and maintain user privacy.
Cost and Implementation Challenges
Biometric authentication often requires significant upfront investment in specialized hardware such as fingerprint scanners and facial recognition cameras, leading to higher implementation costs compared to password authentication, which relies mostly on existing infrastructure. The complexity of integrating biometric systems with legacy IT environments poses substantial technical challenges, requiring advanced software development and ongoing maintenance. In contrast, password authentication systems are easier to deploy but suffer from vulnerabilities and user management issues, potentially increasing long-term security risks and operational expenses.
Future Trends in Authentication Technologies
Biometric authentication is rapidly evolving with advancements in artificial intelligence and machine learning, enabling more accurate and seamless user verification through fingerprint, facial recognition, and behavioral biometrics. Password authentication faces increasing vulnerabilities due to phishing and credential theft, prompting the rise of passwordless solutions leveraging biometrics and hardware security keys. Future authentication technologies emphasize multi-factor and continuous authentication methods, integrating adaptive risk-based systems to enhance security while maintaining user convenience.
Choosing the Right Authentication Method for Your Organization
Biometric authentication leverages unique physiological traits such as fingerprints, facial recognition, or iris scans to enhance security through difficulty in replication, reducing the risk of unauthorized access compared to traditional password systems. Password authentication remains widely adopted due to ease of implementation and lower upfront costs but is vulnerable to phishing, brute force attacks, and credential theft. Organizations must evaluate factors like security requirements, user convenience, and integration capabilities to select an authentication method that aligns with their risk profile and operational needs.
biometric authentication vs password authentication Infographic
 techiny.com
techiny.com