Blacklist blocks access to known malicious sites and IP addresses, preventing threats by denying entry to harmful entities. Whitelist permits only pre-approved applications, websites, or users, providing strict control by allowing access solely to trusted sources. Combining both approaches enhances cybersecurity by minimizing attack surfaces and improving network defense.
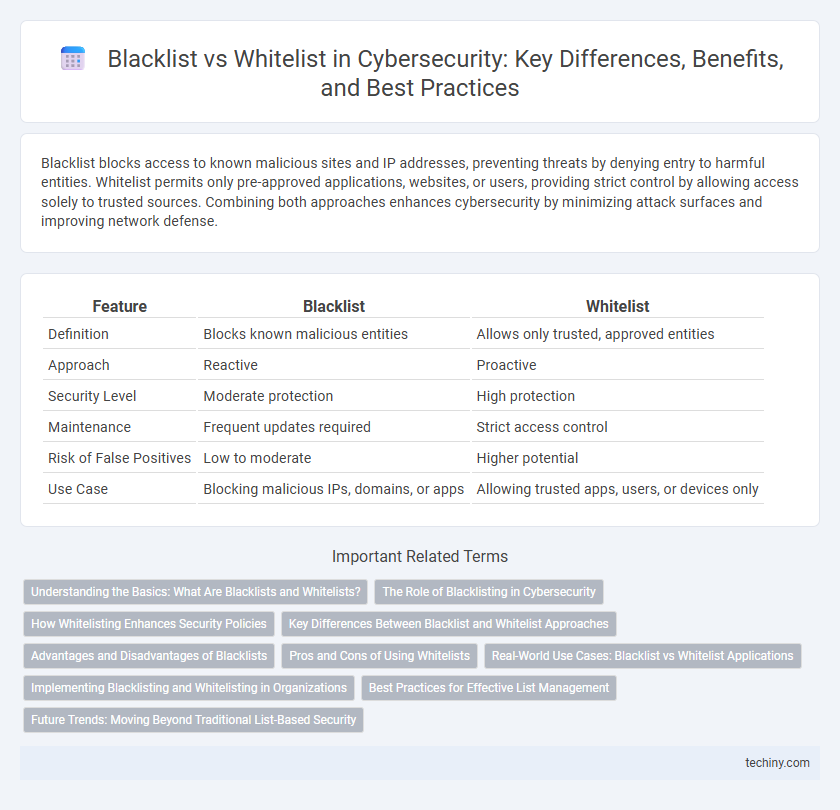
Table of Comparison
| Feature | Blacklist | Whitelist |
|---|---|---|
| Definition | Blocks known malicious entities | Allows only trusted, approved entities |
| Approach | Reactive | Proactive |
| Security Level | Moderate protection | High protection |
| Maintenance | Frequent updates required | Strict access control |
| Risk of False Positives | Low to moderate | Higher potential |
| Use Case | Blocking malicious IPs, domains, or apps | Allowing trusted apps, users, or devices only |
Understanding the Basics: What Are Blacklists and Whitelists?
Blacklists and whitelists are essential tools in cybersecurity for controlling access to systems and networks. A blacklist contains a list of entities such as IP addresses, domains, or applications that are explicitly blocked due to suspicious or malicious behavior. Conversely, a whitelist specifies approved entities that are granted access, ensuring that only trusted sources can interact with the protected environment.
The Role of Blacklisting in Cybersecurity
Blacklisting in cybersecurity involves blocking known malicious IP addresses, domains, or applications to prevent unauthorized access and protect systems from threats such as malware, phishing, and ransomware. This method relies on continuously updated databases of identified threats to enhance network security and reduce attack surfaces. Blacklisting complements other security measures by filtering out high-risk entities before they can cause harm.
How Whitelisting Enhances Security Policies
Whitelisting enhances security policies by allowing only pre-approved applications, users, or IP addresses to access systems, significantly reducing the attack surface. This proactive approach prevents unauthorized and potentially malicious entities from executing, unlike blacklisting, which only blocks known threats after detection. By enforcing strict access controls, whitelisting minimizes risks of malware, ransomware, and zero-day exploits, ensuring a more robust cybersecurity posture.
Key Differences Between Blacklist and Whitelist Approaches
Blacklist and whitelist approaches differ primarily in their access control strategies; blacklists block known malicious entities while allowing all others, whereas whitelists permit only pre-approved entities, blocking the rest. Blacklists require continuous updates to identify and block new threats, making them reactive, while whitelists provide proactive security by restricting access to a controlled set. This fundamental contrast affects system vulnerability, management overhead, and overall cybersecurity posture.
Advantages and Disadvantages of Blacklists
Blacklists in cybersecurity provide a straightforward method to block known malicious IP addresses, domains, or applications, effectively reducing exposure to recognized threats and minimizing the risk of unauthorized access. However, blacklists require continuous updating to maintain their effectiveness, and they may fail to prevent new or unknown threats, leading to potential security gaps. Their reactive nature can also result in false positives, where legitimate entities are mistakenly blocked, potentially disrupting normal network operations.
Pros and Cons of Using Whitelists
Whitelists in cybersecurity offer robust protection by allowing only pre-approved applications or IP addresses, significantly reducing the risk of unauthorized access and malware infections. However, they require continuous maintenance and updates to accommodate legitimate new entries, which can be time-consuming and may hinder operational flexibility. The strict nature of whitelisting may cause delays in deployment and increase administrative overhead, especially in dynamic or large-scale environments.
Real-World Use Cases: Blacklist vs Whitelist Applications
Blacklist applications in cybersecurity involve blocking known malicious IP addresses, domains, or software to prevent unauthorized access and attacks, commonly used in email spam filters and firewall rules. Whitelist approaches allow only pre-approved entities, enhancing security in environments like corporate networks and application control by permitting trusted devices and software exclusively. Organizations often combine both methods to balance flexibility and protection, using blacklists to identify threats and whitelists to minimize false positives and ensure operational continuity.
Implementing Blacklisting and Whitelisting in Organizations
Implementing blacklisting in organizations involves creating and maintaining a list of known malicious IP addresses, domains, or applications to block unauthorized access and malware threats effectively. Whitelisting restricts system access to pre-approved, trusted software and users, enhancing security by minimizing the attack surface and preventing zero-day exploits. Combining blacklisting and whitelisting strategies ensures comprehensive protection by balancing flexibility in access control with strict threat prevention measures.
Best Practices for Effective List Management
Effective list management in cybersecurity prioritizes dynamic updating of blacklists and whitelists to mitigate emerging threats while ensuring access to trusted entities. Implementing automated monitoring tools enhances accuracy by quickly identifying unauthorized or malicious activities, reducing reliance on manual oversight. Segmentation of lists based on risk levels and regularly reviewing entries help maintain optimal protection and minimize false positives or negatives.
Future Trends: Moving Beyond Traditional List-Based Security
Future trends in cybersecurity emphasize shifting from traditional blacklist and whitelist frameworks to adaptive, AI-driven threat detection systems that analyze behavior patterns and real-time data. Zero Trust Architecture integrates continuous authentication and micro-segmentation, reducing reliance on static lists by dynamically assessing risk scores. This evolution enhances resilience against sophisticated cyber threats, enabling proactive defense mechanisms that anticipate and mitigate attacks before they manifest.
Blacklist vs Whitelist Infographic
 techiny.com
techiny.com