BYOD (Bring Your Own Device) policies allow employees to use personal devices for work, increasing flexibility but raising significant security risks due to inconsistent device management. COPE (Corporate-Owned, Personally Enabled) offers a more secure alternative by providing company-owned devices that balance employee usability with centralized control and enhanced data protection. Choosing between BYOD and COPE depends on the organization's risk tolerance, regulatory requirements, and overall cybersecurity strategy to minimize vulnerabilities and ensure compliance.
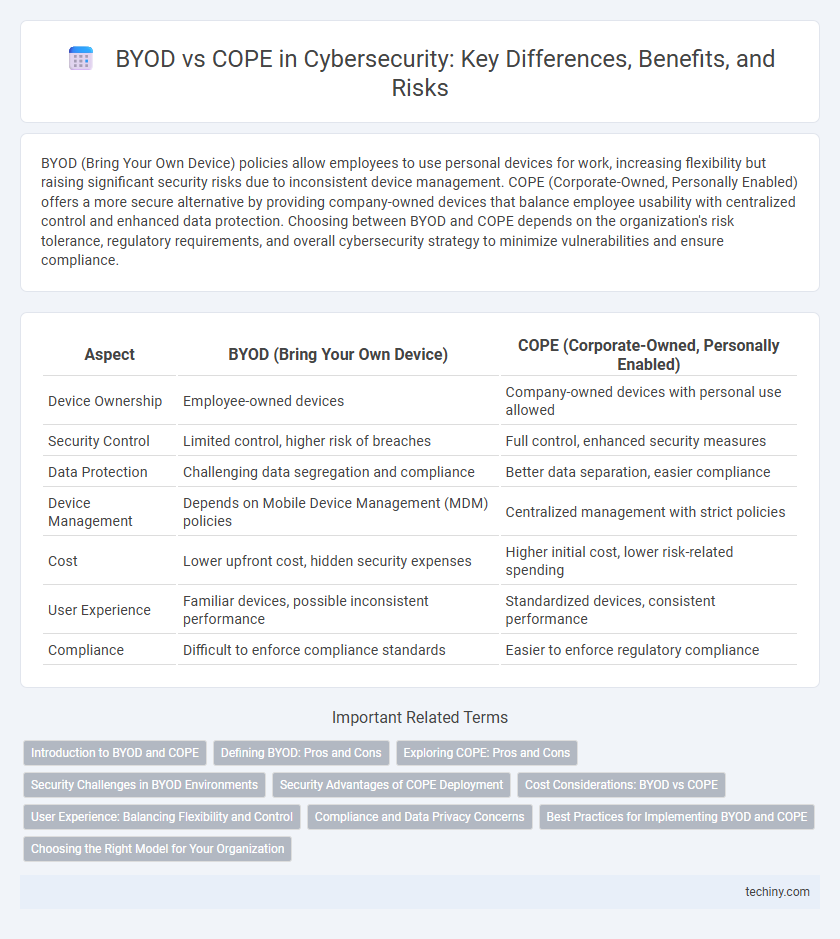
Table of Comparison
| Aspect | BYOD (Bring Your Own Device) | COPE (Corporate-Owned, Personally Enabled) |
|---|---|---|
| Device Ownership | Employee-owned devices | Company-owned devices with personal use allowed |
| Security Control | Limited control, higher risk of breaches | Full control, enhanced security measures |
| Data Protection | Challenging data segregation and compliance | Better data separation, easier compliance |
| Device Management | Depends on Mobile Device Management (MDM) policies | Centralized management with strict policies |
| Cost | Lower upfront cost, hidden security expenses | Higher initial cost, lower risk-related spending |
| User Experience | Familiar devices, possible inconsistent performance | Standardized devices, consistent performance |
| Compliance | Difficult to enforce compliance standards | Easier to enforce regulatory compliance |
Introduction to BYOD and COPE
BYOD (Bring Your Own Device) allows employees to use personal devices for work, increasing flexibility but raising security concerns due to diverse device management. COPE (Corporate-Owned, Personally Enabled) provides company-owned devices that employees can use for both work and personal tasks, offering tighter control over security policies and compliance. Companies must weigh the balance between user convenience and robust cybersecurity measures when choosing between BYOD and COPE models.
Defining BYOD: Pros and Cons
Bring Your Own Device (BYOD) policies allow employees to use personal devices for work purposes, enhancing flexibility and reducing hardware costs. However, BYOD introduces significant security risks including data leakage, inconsistent device management, and challenges in enforcing corporate security protocols. Effective BYOD management requires robust endpoint protection, comprehensive user training, and clear policies to mitigate vulnerabilities while leveraging the benefits of increased employee mobility.
Exploring COPE: Pros and Cons
Corporate-Owned, Personally Enabled (COPE) combines corporate control with employee personal use, enhancing security through standardized device management and enforcing consistent compliance policies. COPE allows IT teams to implement robust security measures such as Mobile Device Management (MDM), data encryption, and remote wiping, reducing risks of data breaches compared to Bring Your Own Device (BYOD). However, COPE can increase costs and may impact user privacy and device personalization, requiring balanced policies to maintain employee satisfaction while ensuring cybersecurity.
Security Challenges in BYOD Environments
BYOD environments introduce significant security challenges due to the use of personal devices that often lack standardized security controls, increasing the risk of data breaches and malware infections. Unlike COPE models, where devices are company-owned and centrally managed, BYOD complicates the enforcement of consistent security policies and mobile device management (MDM). This results in vulnerabilities such as unauthorized access, data leakage, and difficulty in monitoring and securing diverse operating systems and applications.
Security Advantages of COPE Deployment
COPE deployment enhances cybersecurity by providing organizations with full control over device configurations, enabling consistent enforcement of security policies and minimizing vulnerabilities. By owning and managing devices, companies can implement uniform encryption, endpoint protection, and mobile device management (MDM) solutions, reducing risks of data breaches and unauthorized access. This controlled environment ensures compliance with regulatory standards and simplifies incident response compared to the varied and less predictable security posture of BYOD.
Cost Considerations: BYOD vs COPE
BYOD reduces upfront hardware expenses by leveraging employees' personal devices, but increases costs in managing security risks and potential data breaches. COPE entails higher initial investments in standardized devices and licensing but offers streamlined management and stronger security controls, lowering long-term operational expenses. Evaluating total cost of ownership (TCO) for BYOD versus COPE requires balancing direct hardware savings against indirect costs like IT support, compliance, and data protection.
User Experience: Balancing Flexibility and Control
BYOD (Bring Your Own Device) enhances user experience by offering flexible access to work resources on personal devices but challenges IT with inconsistent security standards. COPE (Corporate Owned, Personally Enabled) provides greater control over device management and security policies while allowing limited personal use, resulting in a more secure yet slightly restrictive user experience. Balancing flexibility and control requires implementing robust endpoint security solutions and clear usage policies to protect corporate data without compromising employee productivity.
Compliance and Data Privacy Concerns
BYOD (Bring Your Own Device) policies often pose significant compliance challenges due to the difficulty of enforcing uniform security protocols and managing diverse personal devices, increasing the risk of data breaches and unauthorized access to sensitive information. In contrast, COPE (Corporate-Owned, Personally Enabled) models offer greater control over devices and data, enabling stricter compliance with regulations such as GDPR and HIPAA through centralized management and standardized security measures. Prioritizing COPE can enhance data privacy protections and reduce vulnerabilities associated with personal device usage in corporate environments.
Best Practices for Implementing BYOD and COPE
Implement strict access controls and encryption protocols to safeguard sensitive data on BYOD and COPE devices, minimizing risk of breaches. Implement comprehensive mobile device management (MDM) solutions that ensure consistent security policies, software updates, and remote wipe capabilities. Conduct regular employee training on cybersecurity awareness specific to BYOD and COPE environments, reinforcing safe device usage and incident reporting.
Choosing the Right Model for Your Organization
Selecting the appropriate mobile device management model depends on balancing security, control, and employee flexibility. Bring Your Own Device (BYOD) offers cost savings and increased user convenience but presents higher risks of data leakage and inconsistent security enforcement. Corporate Owned, Personally Enabled (COPE) provides stronger security through centralized control and standardized protocols, making it ideal for organizations with stringent compliance requirements and sensitive data protection needs.
BYOD vs COPE Infographic
 techiny.com
techiny.com