Certificate Pinning enhances security by ensuring that clients only accept a specific cryptographic certificate, preventing man-in-the-middle attacks through fraudulent certificates. HSTS (HTTP Strict Transport Security) enforces secure HTTPS connections by instructing browsers to reject insecure HTTP requests, reducing the risk of protocol downgrade attacks. Combining Certificate Pinning and HSTS creates a robust defense against interception and impersonation in web communications.
Table of Comparison
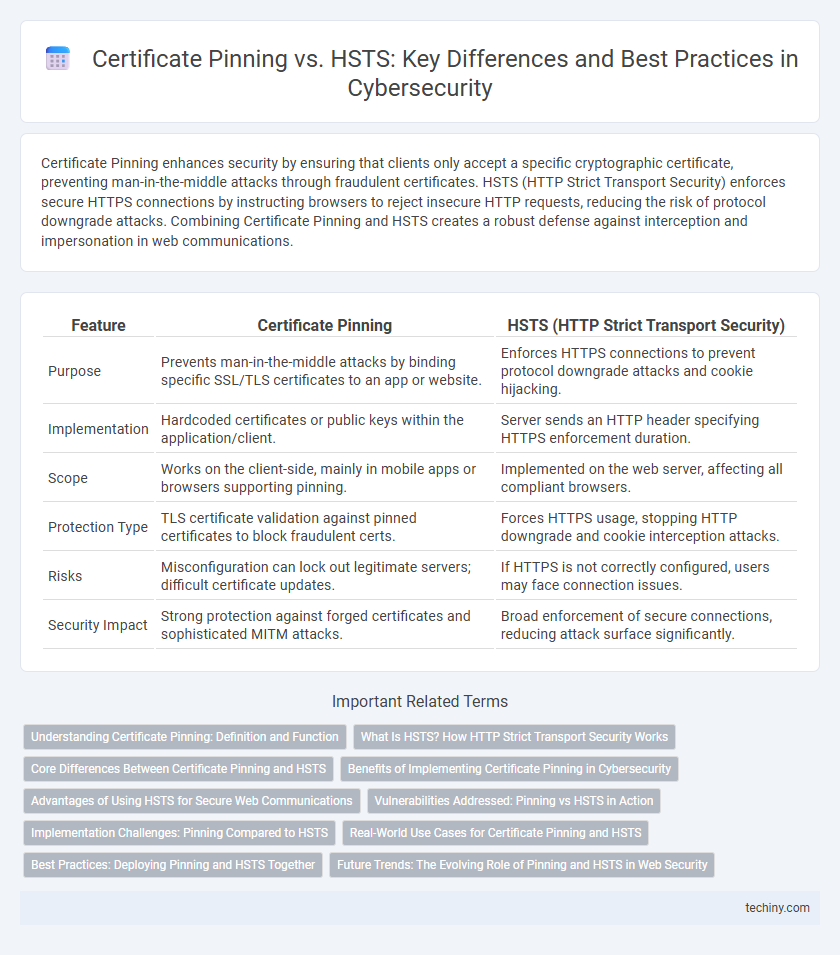
| Feature | Certificate Pinning | HSTS (HTTP Strict Transport Security) |
|---|---|---|
| Purpose | Prevents man-in-the-middle attacks by binding specific SSL/TLS certificates to an app or website. | Enforces HTTPS connections to prevent protocol downgrade attacks and cookie hijacking. |
| Implementation | Hardcoded certificates or public keys within the application/client. | Server sends an HTTP header specifying HTTPS enforcement duration. |
| Scope | Works on the client-side, mainly in mobile apps or browsers supporting pinning. | Implemented on the web server, affecting all compliant browsers. |
| Protection Type | TLS certificate validation against pinned certificates to block fraudulent certs. | Forces HTTPS usage, stopping HTTP downgrade and cookie interception attacks. |
| Risks | Misconfiguration can lock out legitimate servers; difficult certificate updates. | If HTTPS is not correctly configured, users may face connection issues. |
| Security Impact | Strong protection against forged certificates and sophisticated MITM attacks. | Broad enforcement of secure connections, reducing attack surface significantly. |
Understanding Certificate Pinning: Definition and Function
Certificate Pinning is a security mechanism that associates a host with their expected X.509 certificate or public key to prevent man-in-the-middle attacks and unauthorized certificate authorities. This technique enhances trust by ensuring the client only accepts a specific certificate or key regardless of the certificate chain validation. Unlike HSTS, which enforces HTTPS usage, Certificate Pinning directly verifies the authenticity of the server's identity through pinned certificates.
What Is HSTS? How HTTP Strict Transport Security Works
HTTP Strict Transport Security (HSTS) is a web security policy mechanism that protects websites against man-in-the-middle attacks by forcing browsers to only interact with servers over secure HTTPS connections. When a website implements HSTS, it sends an HTTP header instructing the browser to automatically convert all HTTP requests to HTTPS for a specified duration, preventing downgrade attacks and cookie hijacking. This protocol enhances user security by ensuring encrypted communication and eliminating insecure HTTP fallback.
Core Differences Between Certificate Pinning and HSTS
Certificate Pinning secures communication by binding a specific cryptographic certificate to a host, preventing attackers from using fraudulent or compromised certificates. HSTS (HTTP Strict Transport Security) enforces the use of HTTPS connections by instructing browsers to refuse insecure HTTP requests, reducing the risk of man-in-the-middle attacks. The core difference lies in Certificate Pinning verifying certificate authenticity at the application level, while HSTS ensures strict transport security at the protocol level.
Benefits of Implementing Certificate Pinning in Cybersecurity
Implementing certificate pinning enhances cybersecurity by preventing man-in-the-middle attacks through strict validation of server certificates, ensuring only trusted certificates are accepted. It reduces reliance on external Certificate Authorities, minimizing risks associated with compromised or fraudulent certificates. Certificate pinning strengthens secure communication by maintaining a consistent verification process, boosting overall trust in encrypted connections.
Advantages of Using HSTS for Secure Web Communications
HSTS (HTTP Strict Transport Security) enforces secure HTTPS connections across entire domains, preventing protocol downgrade attacks and cookie hijacking. It reduces the risk of man-in-the-middle attacks by instructing browsers to only interact with servers over secure connections, enhancing overall web security. Unlike certificate pinning, HSTS offers seamless protection without requiring frequent certificate updates, making it easier to maintain robust encrypted communication.
Vulnerabilities Addressed: Pinning vs HSTS in Action
Certificate pinning protects against man-in-the-middle attacks by binding an application to a specific public key or certificate, preventing use of fraudulent certificates during TLS handshakes. HTTP Strict Transport Security (HSTS) enforces secure HTTPS connections by instructing browsers to refuse insecure HTTP access, mitigating SSL stripping attacks. While pinning addresses certificate spoofing at the client level, HSTS focuses on ensuring consistent transport-layer security across web sessions, complementing each other to close different vulnerability gaps.
Implementation Challenges: Pinning Compared to HSTS
Certificate pinning demands meticulous management of pinned certificates across client applications, posing challenges during certificate renewals and increasing the risk of connection failures if pins become outdated. In contrast, HSTS implementation is less complex, relying on server-side headers to enforce HTTPS without requiring client updates, thereby reducing operational overhead. The rigidity of pinning mechanisms risks service disruption, whereas HSTS provides a more flexible and scalable approach to securing web connections.
Real-World Use Cases for Certificate Pinning and HSTS
Certificate pinning is widely adopted in mobile banking apps and enterprise VPNs to prevent man-in-the-middle attacks by ensuring the client trusts only specific certificates. HSTS is commonly implemented by major websites, including Google and Facebook, to enforce HTTPS and protect users from protocol downgrade attacks and cookie hijacking. Both techniques complement each other by strengthening transport layer security and safeguarding sensitive user data in real-world applications.
Best Practices: Deploying Pinning and HSTS Together
Deploying Certificate Pinning alongside HTTP Strict Transport Security (HSTS) enhances web security by ensuring both certificate authenticity and enforcing HTTPS connections. Best practices for integrating these include configuring HSTS with a long max-age and includeSubDomains directive while implementing pinning with multiple backup pins to prevent service disruption. Combining them mitigates risks from man-in-the-middle attacks and reduces the chances of certificate-based vulnerabilities.
Future Trends: The Evolving Role of Pinning and HSTS in Web Security
Certificate pinning enhances web security by binding a specific public key to a server, mitigating risks of man-in-the-middle attacks, while HSTS (HTTP Strict Transport Security) enforces secure connections by instructing browsers to only use HTTPS. Future trends indicate increased integration of dynamic pinning and automated HSTS policies within browsers to strengthen resistance against certificate forgery and downgrade attacks. Advances in machine learning and threat intelligence further enable adaptive security measures, evolving pinning and HSTS into proactive defenses in modern cybersecurity frameworks.
Certificate Pinning vs HSTS Infographic
 techiny.com
techiny.com