Credential stuffing attacks exploit stolen login credentials from data breaches to automate unauthorized access, relying heavily on reused passwords across multiple sites. Brute force attacks systematically attempt every possible password combination to gain entry, often targeting a single account or system. Both methods threaten cybersecurity by bypassing traditional authentication safeguards, emphasizing the need for multi-factor authentication and robust password policies.
Table of Comparison
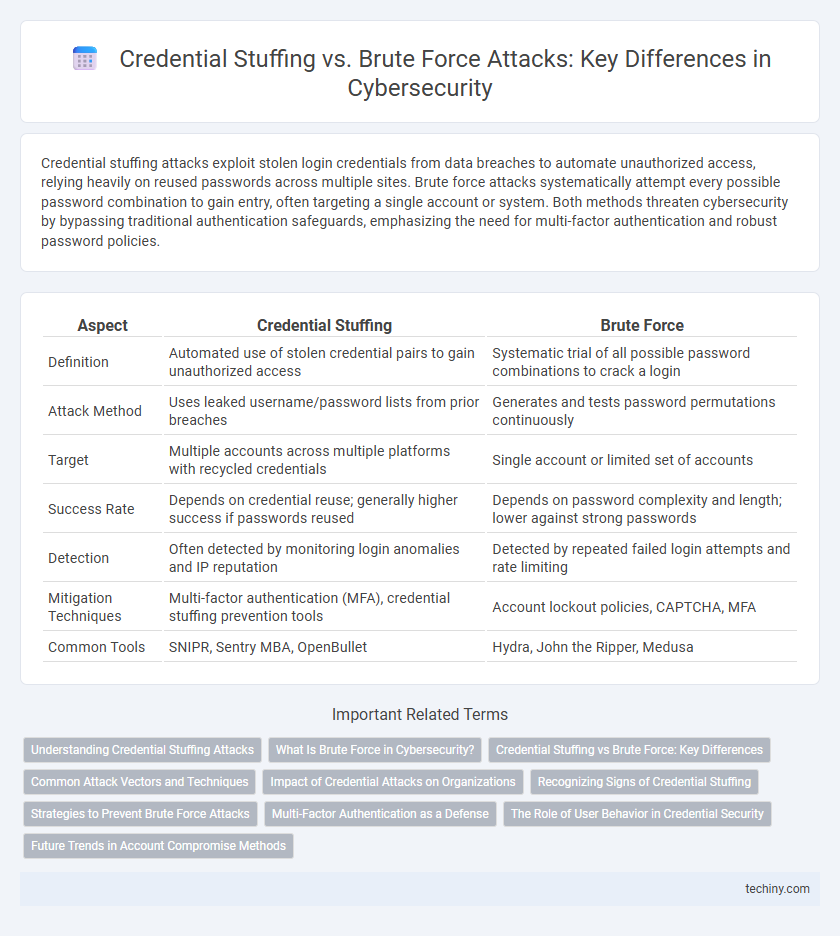
| Aspect | Credential Stuffing | Brute Force |
|---|---|---|
| Definition | Automated use of stolen credential pairs to gain unauthorized access | Systematic trial of all possible password combinations to crack a login |
| Attack Method | Uses leaked username/password lists from prior breaches | Generates and tests password permutations continuously |
| Target | Multiple accounts across multiple platforms with recycled credentials | Single account or limited set of accounts |
| Success Rate | Depends on credential reuse; generally higher success if passwords reused | Depends on password complexity and length; lower against strong passwords |
| Detection | Often detected by monitoring login anomalies and IP reputation | Detected by repeated failed login attempts and rate limiting |
| Mitigation Techniques | Multi-factor authentication (MFA), credential stuffing prevention tools | Account lockout policies, CAPTCHA, MFA |
| Common Tools | SNIPR, Sentry MBA, OpenBullet | Hydra, John the Ripper, Medusa |
Understanding Credential Stuffing Attacks
Credential stuffing attacks exploit large volumes of stolen username and password combinations to gain unauthorized access to multiple user accounts by automating login attempts on various platforms. Unlike brute force attacks that systematically try all possible password combinations, credential stuffing relies on the reuse of credentials harvested from data breaches, significantly increasing the success rate against users with weak password hygiene. Effective defenses include implementing multi-factor authentication, monitoring for unusual login patterns, and using adaptive rate-limiting to detect and block automated login attempts.
What Is Brute Force in Cybersecurity?
Brute force in cybersecurity is a hacking technique where attackers systematically attempt all possible password combinations to gain unauthorized access to accounts. This method relies on high computational power and time to crack weak or common passwords, often targeting login systems without additional protective measures like multi-factor authentication. Unlike credential stuffing, which uses leaked credentials from other breaches, brute force generates every potential password until the correct one is discovered.
Credential Stuffing vs Brute Force: Key Differences
Credential stuffing exploits recycled credentials from data breaches to automate unauthorized access, targeting multiple accounts with valid username-password pairs. Brute force attacks systematically attempt every possible password combination for a single account until the correct one is found, often relying on computational power. The key difference lies in credential stuffing using breached data, making it faster and more efficient, while brute force depends on exhaustive trial and error without prior knowledge of passwords.
Common Attack Vectors and Techniques
Credential stuffing exploits stolen username and password pairs from data breaches for automated login attempts, relying on the reuse of credentials across multiple sites. Brute force attacks systematically try all possible password combinations to gain unauthorized access, often targeting a single account with repeated login attempts. Both techniques utilize automated tools and botnets to increase attack efficiency and evade detection by security systems.
Impact of Credential Attacks on Organizations
Credential stuffing and brute force attacks severely compromise organizational security by enabling unauthorized access to sensitive data and critical systems, often resulting in financial losses exceeding millions of dollars annually. These attacks increase the risk of data breaches, erode customer trust, and disrupt business operations, causing downtime that can reduce revenue and damage brand reputation. Implementing multi-factor authentication and continuous monitoring significantly mitigates the risks associated with credential-based cyber attacks.
Recognizing Signs of Credential Stuffing
Unusual login patterns such as multiple failed attempts from diverse IP addresses or rapid-fire submissions targeting various accounts signal credential stuffing attacks. Monitoring for sudden spikes in login failures and account lockouts helps differentiate credential stuffing from brute force attacks, which generally focus on a single account. Implementing anomaly detection systems that analyze login velocity and geographic dispersion enhances early recognition of credential stuffing threats.
Strategies to Prevent Brute Force Attacks
Implement multi-factor authentication (MFA) to add an extra layer of security beyond passwords, reducing the success of brute force attacks significantly. Implement account lockout policies after a set number of failed login attempts to slow down automated attack tools. Employ IP blacklisting, rate limiting, and CAPTCHA challenges to detect and block suspicious login behavior effectively.
Multi-Factor Authentication as a Defense
Credential stuffing attacks leverage stolen username-password pairs across multiple sites, exploiting reused credentials, while brute force attacks systematically guess passwords to breach accounts. Multi-factor authentication (MFA) significantly reduces the risk of unauthorized access by requiring additional verification factors beyond passwords. Implementing MFA creates a robust security layer that mitigates both credential stuffing and brute force attempts, enhancing overall cybersecurity posture.
The Role of User Behavior in Credential Security
User behavior plays a critical role in credential security, as weak password practices increase susceptibility to both credential stuffing and brute force attacks. Credential stuffing exploits reused or compromised passwords across multiple sites, while brute force attacks rely on systematically guessing passwords, often targeting users who employ simple or common credentials. Encouraging unique, complex passwords and multi-factor authentication significantly reduces the risk posed by both attack methods.
Future Trends in Account Compromise Methods
Emerging trends in account compromise methods reveal that credential stuffing attacks increasingly leverage artificial intelligence to automate the testing of vast volumes of leaked credentials rapidly, while brute force attacks evolve with the integration of distributed networks of compromised devices to bypass traditional rate-limiting controls. Advances in machine learning also enable attackers to optimize password generation patterns, making brute force attempts more adaptive and effective against evolving password complexity requirements. Cybersecurity defenses must anticipate these sophisticated techniques by employing multi-factor authentication and anomaly detection systems that analyze behavioral patterns beyond mere login attempts.
Credential Stuffing vs Brute Force Infographic
 techiny.com
techiny.com