Data masking conceals sensitive information by replacing original data with fictitious but realistic values, ensuring that unauthorized users cannot identify the actual data. Data encryption transforms data into an unreadable format using cryptographic algorithms, requiring a decryption key to restore the original content. While both techniques protect data privacy, masking is often used for non-production environments, and encryption secures data in transit and at rest.
Table of Comparison
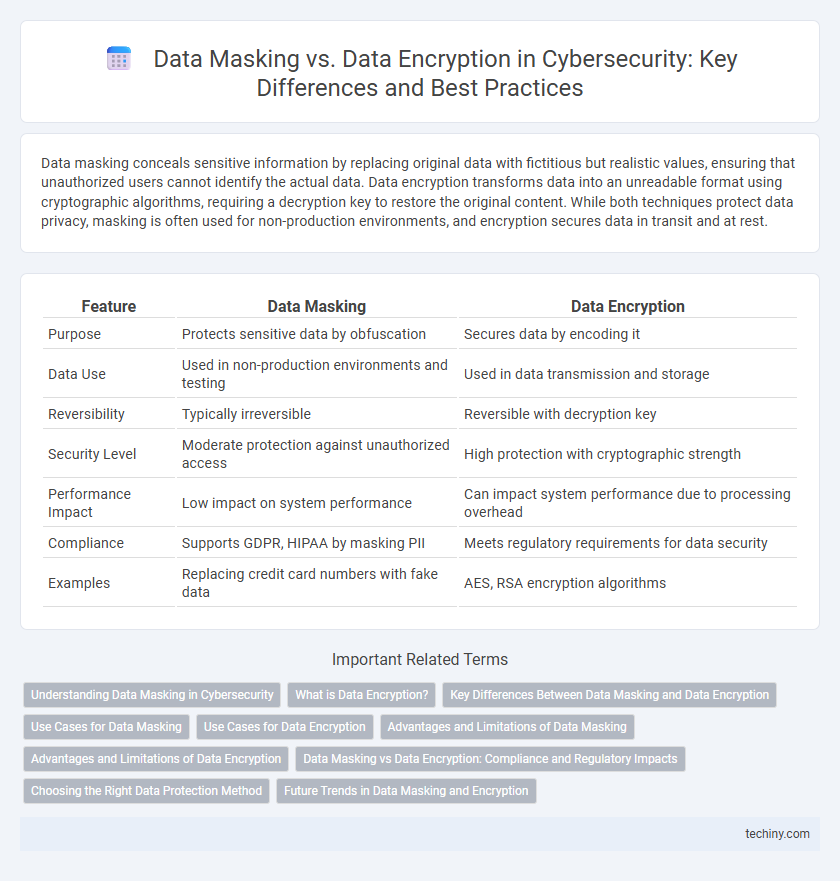
| Feature | Data Masking | Data Encryption |
|---|---|---|
| Purpose | Protects sensitive data by obfuscation | Secures data by encoding it |
| Data Use | Used in non-production environments and testing | Used in data transmission and storage |
| Reversibility | Typically irreversible | Reversible with decryption key |
| Security Level | Moderate protection against unauthorized access | High protection with cryptographic strength |
| Performance Impact | Low impact on system performance | Can impact system performance due to processing overhead |
| Compliance | Supports GDPR, HIPAA by masking PII | Meets regulatory requirements for data security |
| Examples | Replacing credit card numbers with fake data | AES, RSA encryption algorithms |
Understanding Data Masking in Cybersecurity
Data masking in cybersecurity involves obscuring sensitive information by substituting original data with realistic but fictional equivalents, ensuring confidentiality during data testing or sharing. Unlike encryption, which converts data into an unreadable format requiring decryption keys, data masking provides a non-reversible transformation to protect personally identifiable information (PII) and compliance-sensitive data. This technique is essential for safeguarding data in non-production environments while maintaining usability for analysis and development.
What is Data Encryption?
Data encryption is a cybersecurity technique that converts plaintext data into an unreadable format called ciphertext using cryptographic algorithms, ensuring confidentiality and protection against unauthorized access. It employs symmetric or asymmetric keys to encode and decode information, making data secure during transmission or storage. Widely used in securing sensitive information such as financial transactions, personal records, and communication, encryption is essential for maintaining data privacy and integrity.
Key Differences Between Data Masking and Data Encryption
Data masking transforms sensitive data into a non-sensitive format for use in testing or training environments, preserving data usability without exposing actual information. Data encryption converts data into unreadable ciphertext using cryptographic algorithms, requiring a key to decrypt and access the original content, ensuring protection during storage or transmission. The key difference lies in masking's irreversible obfuscation for limited contexts versus encryption's reversible process designed for secure data access control.
Use Cases for Data Masking
Data masking is essential for protecting sensitive information in non-production environments, such as development, testing, and training, where real data is unnecessary but realistic data formats are required. It allows organizations to maintain data utility while ensuring compliance with privacy regulations like GDPR and HIPAA by obfuscating personally identifiable information (PII) without altering underlying data structures. Unlike encryption, data masking enables controlled access to anonymized data, facilitating data sharing and analysis without exposing original sensitive content.
Use Cases for Data Encryption
Data encryption protects sensitive information by converting it into unreadable ciphertext, making it essential for securing data in transit across networks and stored in cloud environments. It is widely used for safeguarding personal identifiable information (PII), financial transactions, and confidential business records against unauthorized access. Encryption also plays a critical role in compliance with regulations like GDPR and HIPAA by ensuring data confidentiality throughout its lifecycle.
Advantages and Limitations of Data Masking
Data masking enhances data security by substituting sensitive information with realistic but fictitious data, reducing the risk of exposure during development or testing phases. It allows safe use of datasets without compromising confidentiality, supporting compliance with regulations like GDPR and HIPAA. However, data masking's limitation lies in its inability to protect data in transit or at rest and may not be suitable for all use cases requiring full data reversibility, unlike encryption.
Advantages and Limitations of Data Encryption
Data encryption offers robust protection by converting sensitive information into unreadable ciphertext, ensuring confidentiality even if data is intercepted or accessed without authorization. It enables secure storage and transmission across untrusted networks, supporting compliance with regulations such as GDPR and HIPAA. Limitations include potential performance overhead due to encryption and decryption processes, key management complexities, and the risk of data being exposed if encryption keys are compromised.
Data Masking vs Data Encryption: Compliance and Regulatory Impacts
Data masking and data encryption both play critical roles in compliance with regulations like GDPR, HIPAA, and PCI-DSS, offering distinct approaches to safeguard sensitive information. Data masking ensures non-reversible obfuscation of data, allowing safe use in testing and development environments without exposing real data, which aligns with regulatory requirements for data minimization and privacy. Data encryption protects data by converting it into inaccessible ciphertext, requiring authorized keys for decryption, making it essential for secure data storage and transmission to meet compliance standards.
Choosing the Right Data Protection Method
Data masking and data encryption serve distinct roles in cybersecurity, with data masking providing obfuscated versions of sensitive information for non-production environments, while data encryption transforms data into unreadable formats to protect it during transmission and storage. Choosing the right data protection method depends on the use case: data masking is ideal for development and testing scenarios where data utility must be preserved without exposing real data, whereas encryption is essential for securing data from unauthorized access across networks and storage systems. Evaluating factors such as regulatory compliance, risk levels, and operational requirements ensures the selection of an appropriate strategy that safeguards sensitive data effectively.
Future Trends in Data Masking and Encryption
Future trends in data masking and encryption emphasize the integration of artificial intelligence and machine learning to enhance adaptive protection mechanisms. Quantum-resistant encryption algorithms are being developed to secure sensitive data against next-generation cyber threats. Cloud-native masking solutions will become prevalent, enabling scalable and dynamic data privacy in hybrid and multi-cloud environments.
Data Masking vs Data Encryption Infographic
 techiny.com
techiny.com