A digital signature provides a secure way to verify the authenticity and integrity of a message or document by using cryptographic algorithms, ensuring it has not been altered. A certificate, issued by a trusted Certificate Authority (CA), serves as a digital ID that links a public key to an entity's identity, establishing trust in online communications. Together, digital signatures and certificates play a crucial role in enhancing cybersecurity by enabling secure, verifiable electronic transactions.
Table of Comparison
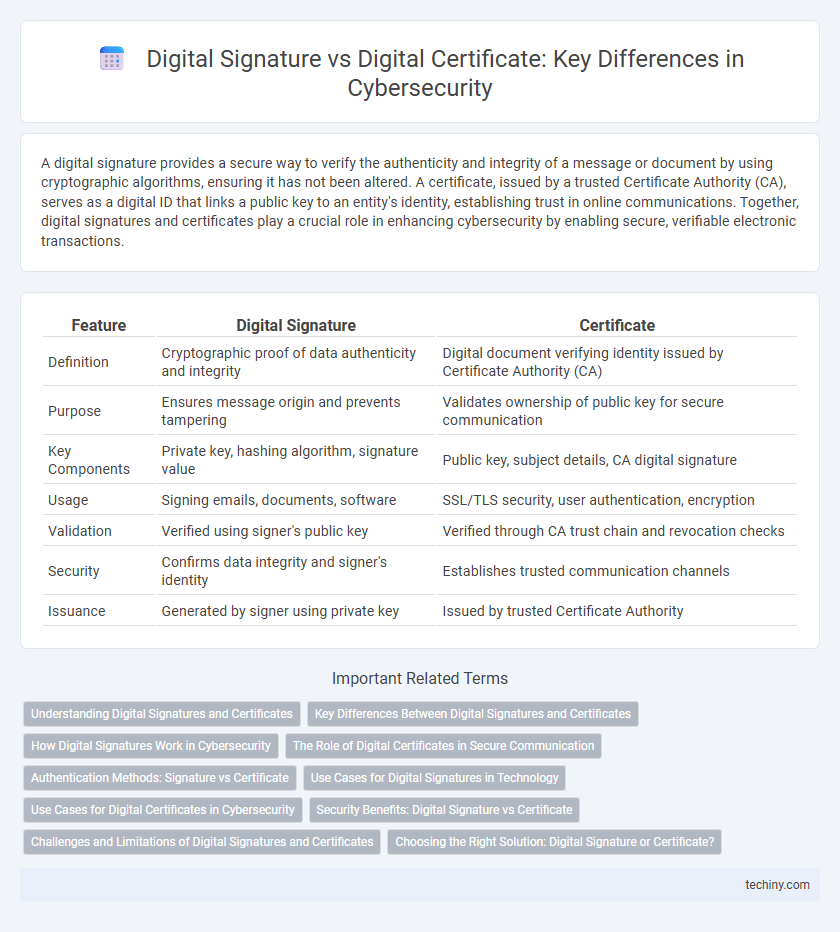
| Feature | Digital Signature | Certificate |
|---|---|---|
| Definition | Cryptographic proof of data authenticity and integrity | Digital document verifying identity issued by Certificate Authority (CA) |
| Purpose | Ensures message origin and prevents tampering | Validates ownership of public key for secure communication |
| Key Components | Private key, hashing algorithm, signature value | Public key, subject details, CA digital signature |
| Usage | Signing emails, documents, software | SSL/TLS security, user authentication, encryption |
| Validation | Verified using signer's public key | Verified through CA trust chain and revocation checks |
| Security | Confirms data integrity and signer's identity | Establishes trusted communication channels |
| Issuance | Generated by signer using private key | Issued by trusted Certificate Authority |
Understanding Digital Signatures and Certificates
Digital signatures provide data integrity and authentication by using cryptographic algorithms to verify the origin and content of a message or document. Digital certificates serve as electronic credentials issued by a trusted Certificate Authority (CA), binding a public key to an entity's identity and enabling secure communication. Understanding that digital signatures validate authenticity and certificates establish trust is crucial in implementing robust cybersecurity measures.
Key Differences Between Digital Signatures and Certificates
Digital signatures provide data integrity and authentication by creating a unique hash encrypted with a sender's private key, verifying the origin and ensuring content remains unaltered. Digital certificates serve as electronic credentials issued by Certificate Authorities (CAs) that bind a public key to an entity's identity, enabling trust in online communications. While digital signatures validate message authenticity, digital certificates establish and verify the trustworthiness of the public key used in the signature process.
How Digital Signatures Work in Cybersecurity
Digital signatures in cybersecurity use asymmetric cryptography to authenticate the identity of the sender and ensure data integrity by generating a unique hash of the message, encrypted with the sender's private key. When the recipient receives the data, they use the sender's public key to decrypt the hash and compare it with a newly generated hash of the received message, confirming authenticity and preventing tampering. This process is critical for secure electronic transactions, legal documents, and software distribution, offering non-repudiation and trust in digital communications.
The Role of Digital Certificates in Secure Communication
Digital certificates play a crucial role in secure communication by verifying the identity of entities and enabling trust in digital interactions. These certificates, issued by trusted Certificate Authorities (CAs), bind public keys to organizations or individuals, ensuring data integrity and preventing impersonation. Unlike digital signatures that validate the authenticity of specific messages, digital certificates establish a secure framework for encrypting data and facilitating safe exchanges across networks.
Authentication Methods: Signature vs Certificate
Digital signatures authenticate the integrity and origin of a message by using cryptographic algorithms to create a unique signature tied to the sender's private key. Certificates, issued by trusted Certificate Authorities (CAs), authenticate the identity of entities by linking public keys to verified identities in a secure, tamper-proof manner. While digital signatures provide non-repudiation and message authenticity, certificates establish trust by validating the public key infrastructure (PKI) for secure communications.
Use Cases for Digital Signatures in Technology
Digital signatures authenticate the integrity and origin of digital documents, enabling secure email communication, software distribution, and financial transactions by ensuring data has not been altered. They are integral to blockchain technology for verifying transaction legitimacy and enhancing smart contract enforcement. In contrast, digital certificates primarily establish trusted identities in secure communications, such as SSL/TLS for website encryption.
Use Cases for Digital Certificates in Cybersecurity
Digital certificates are essential in cybersecurity for authenticating the identities of websites, devices, and users, enabling secure communication through SSL/TLS encryption. They facilitate encrypted email (S/MIME), establish trust in software distribution by verifying code signatures, and support VPN access by validating client credentials. These use cases help prevent man-in-the-middle attacks, data breaches, and unauthorized access in digital environments.
Security Benefits: Digital Signature vs Certificate
Digital signatures provide enhanced security by ensuring message integrity, authentication, and non-repudiation through cryptographic algorithms, making it difficult for attackers to forge or alter documents. Digital certificates serve as a trusted third-party verification mechanism, linking a public key to the identity of an organization or individual, which helps prevent impersonation and man-in-the-middle attacks. The combined use of digital signatures and certificates strengthens overall cybersecurity by verifying both the document source and its authenticity in encrypted communications.
Challenges and Limitations of Digital Signatures and Certificates
Digital signatures face challenges such as key management complexities, potential vulnerability to quantum computing attacks, and limitations in verifying the signer's identity without a trusted certificate authority (CA). Digital certificates depend heavily on the trustworthiness of certificate authorities, which can be compromised, leading to risks like certificate forgery or mis-issuance. Both digital signatures and certificates encounter limitations in interoperability, revocation complexities, and reliance on secure infrastructure to maintain validity and authenticity in cybersecurity environments.
Choosing the Right Solution: Digital Signature or Certificate?
Choosing the right solution between a digital signature and a digital certificate depends on the specific security needs and use cases. Digital signatures provide data integrity and non-repudiation for individual documents, leveraging cryptographic algorithms to verify authenticity. Digital certificates serve as digital IDs issued by Certificate Authorities (CAs), establishing trust by validating the identity of users, websites, or devices within a Public Key Infrastructure (PKI).
Digital signature vs certificate Infographic
 techiny.com
techiny.com