Endpoint Detection and Response (EDR) provides advanced threat detection, continuous monitoring, and rapid incident response capabilities, surpassing traditional Antivirus (AV) solutions that primarily focus on signature-based malware detection. EDR leverages behavioral analysis and machine learning to identify suspicious activities and unknown threats in real time, enabling proactive defense strategies. While AV remains essential for basic protection against known viruses, EDR offers a more comprehensive approach to securing endpoints in today's complex cyber threat landscape.
Table of Comparison
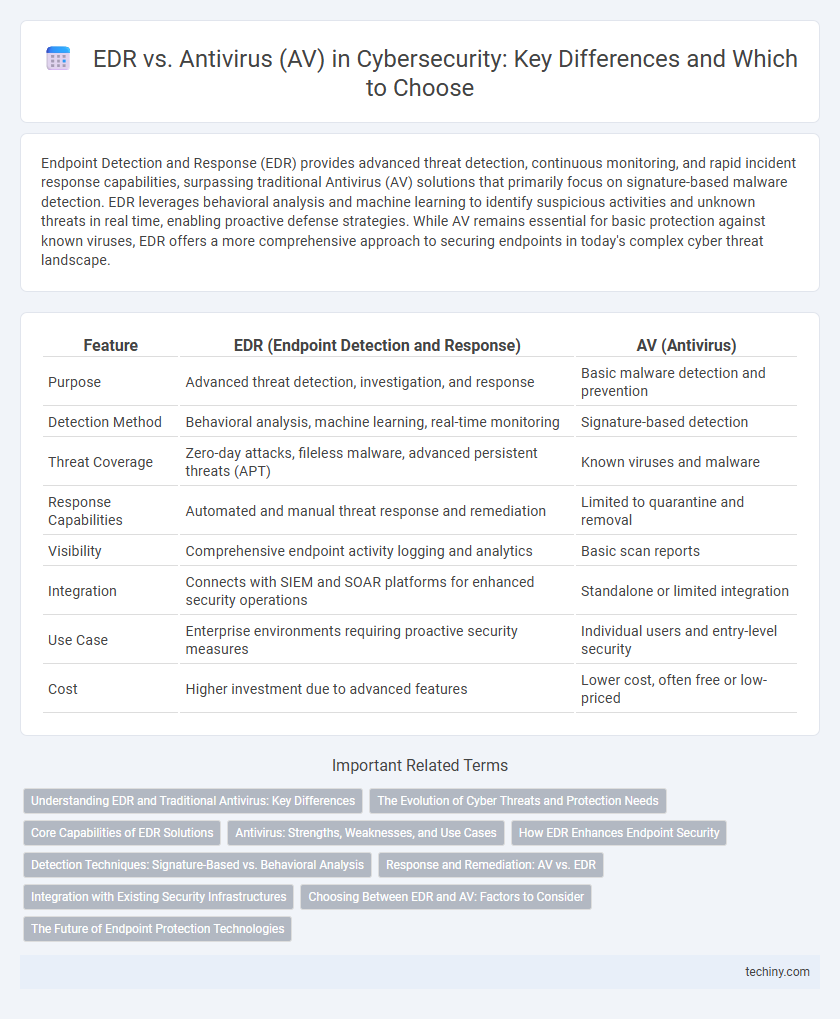
| Feature | EDR (Endpoint Detection and Response) | AV (Antivirus) |
|---|---|---|
| Purpose | Advanced threat detection, investigation, and response | Basic malware detection and prevention |
| Detection Method | Behavioral analysis, machine learning, real-time monitoring | Signature-based detection |
| Threat Coverage | Zero-day attacks, fileless malware, advanced persistent threats (APT) | Known viruses and malware |
| Response Capabilities | Automated and manual threat response and remediation | Limited to quarantine and removal |
| Visibility | Comprehensive endpoint activity logging and analytics | Basic scan reports |
| Integration | Connects with SIEM and SOAR platforms for enhanced security operations | Standalone or limited integration |
| Use Case | Enterprise environments requiring proactive security measures | Individual users and entry-level security |
| Cost | Higher investment due to advanced features | Lower cost, often free or low-priced |
Understanding EDR and Traditional Antivirus: Key Differences
Endpoint Detection and Response (EDR) and traditional Antivirus (AV) differ significantly in their approach to cybersecurity; EDR provides continuous monitoring, real-time threat detection, and automated response capabilities, while AV primarily relies on signature-based detection to identify known malware. EDR systems leverage behavioral analysis, machine learning, and forensic data to detect sophisticated threats such as zero-day attacks and advanced persistent threats (APTs) that evade traditional AV detection. Organizations integrating EDR benefit from enhanced visibility, incident investigation tools, and proactive defense mechanisms beyond the reactive scanning and removal processes offered by conventional antivirus software.
The Evolution of Cyber Threats and Protection Needs
Cyber threats have evolved from simple malware attacks to complex, multi-stage intrusions that bypass traditional antivirus (AV) solutions, necessitating advanced endpoint detection and response (EDR) systems for real-time monitoring and behavioral analysis. While AV primarily focuses on signature-based detection to identify known malware, EDR employs machine learning algorithms, threat intelligence integration, and continuous endpoint visibility to detect and mitigate sophisticated threats such as zero-day exploits, ransomware, and fileless attacks. The shift from AV to EDR reflects the increasing demand for proactive, adaptive cybersecurity defenses capable of responding to the dynamic and rapidly evolving threat landscape.
Core Capabilities of EDR Solutions
EDR solutions provide continuous real-time monitoring, advanced threat detection through behavioral analysis, and rapid incident response capabilities that surpass traditional antivirus (AV) software. Core capabilities include endpoint data collection, automated threat hunting, and detailed forensic investigation, enabling proactive defense against sophisticated cyber attacks. Unlike AV, which primarily relies on signature-based detection, EDR integrates machine learning and analytics to identify and mitigate emerging threats effectively.
Antivirus: Strengths, Weaknesses, and Use Cases
Antivirus (AV) software excels at identifying and removing known malware through signature-based detection, making it effective for blocking common viruses and trojans. Its weaknesses include limited capability against zero-day threats, advanced persistent threats (APTs), and fileless attacks due to reliance on signature databases. AV is best suited for baseline endpoint protection in environments requiring simple, cost-effective security against traditional malware infections.
How EDR Enhances Endpoint Security
Endpoint Detection and Response (EDR) significantly enhances endpoint security by continuously monitoring and analyzing endpoint activities to detect and respond to threats in real time. Unlike traditional Antivirus (AV) solutions that rely primarily on signature-based detection, EDR uses behavior analysis and advanced threat intelligence to identify sophisticated cyberattacks and zero-day threats. This proactive approach enables quicker incident response, reduces dwell time of attackers, and improves overall organizational cybersecurity posture.
Detection Techniques: Signature-Based vs. Behavioral Analysis
Endpoint Detection and Response (EDR) leverages behavioral analysis to detect anomalies and sophisticated threats by monitoring real-time activities and patterns, while traditional Antivirus (AV) relies primarily on signature-based detection, identifying known malware through database matching. Behavioral analysis in EDR enables proactive threat hunting and zero-day attack identification beyond the limitations of static signatures. Signature-based AV offers quick detection of established malware but often fails against polymorphic and emerging threats that do not match existing signatures.
Response and Remediation: AV vs. EDR
Endpoint Detection and Response (EDR) solutions provide advanced threat detection with real-time response capabilities, enabling rapid containment and remediation of complex cyberattacks, whereas traditional Antivirus (AV) primarily focuses on signature-based malware detection and basic removal. EDR platforms offer comprehensive forensic analysis, automated response actions, and continuous monitoring to minimize damage and downtime. AV tools are limited in their incident response scope and often require manual intervention, making them less effective against sophisticated or zero-day threats.
Integration with Existing Security Infrastructures
Endpoint Detection and Response (EDR) integrates seamlessly with existing Security Information and Event Management (SIEM) systems, enhancing real-time threat detection and automated response across complex IT environments. Traditional Antivirus (AV) solutions often function as standalone tools with limited interoperability, focusing primarily on signature-based malware detection. EDR platforms provide comprehensive telemetry and behavioral analysis, enabling unified dashboards and improved correlation with firewalls, intrusion detection systems, and threat intelligence feeds for proactive cybersecurity management.
Choosing Between EDR and AV: Factors to Consider
When choosing between Endpoint Detection and Response (EDR) and traditional Antivirus (AV), consider factors such as threat detection capabilities, response speed, and visibility into sophisticated attacks. EDR provides continuous monitoring and detailed analytics to identify and mitigate advanced persistent threats, while AV primarily focuses on signature-based malware detection. Organizations facing complex cyber threats benefit from EDR's comprehensive approach, whereas smaller environments with basic protection needs may find AV sufficient.
The Future of Endpoint Protection Technologies
Endpoint Detection and Response (EDR) surpasses traditional Antivirus (AV) by offering continuous monitoring, advanced threat analytics, and automated response capabilities essential for combating sophisticated cyber threats. Future endpoint protection technologies will increasingly integrate AI-driven behavioral analysis and cloud-based intelligence to detect zero-day exploits and polymorphic malware. This evolution emphasizes proactive threat hunting and real-time endpoint visibility, marking a shift from reactive defense models to adaptive cybersecurity frameworks.
EDR vs AV Infographic
 techiny.com
techiny.com