A firewall acts as a security barrier between a trusted internal network and untrusted external networks, filtering incoming and outgoing traffic based on predetermined security rules to prevent unauthorized access. A proxy server functions as an intermediary that handles client requests for resources from other servers, offering privacy, content caching, and access control. While firewalls primarily enforce security policies at the network perimeter, proxies enhance user anonymity and can selectively allow or block specific web content.
Table of Comparison
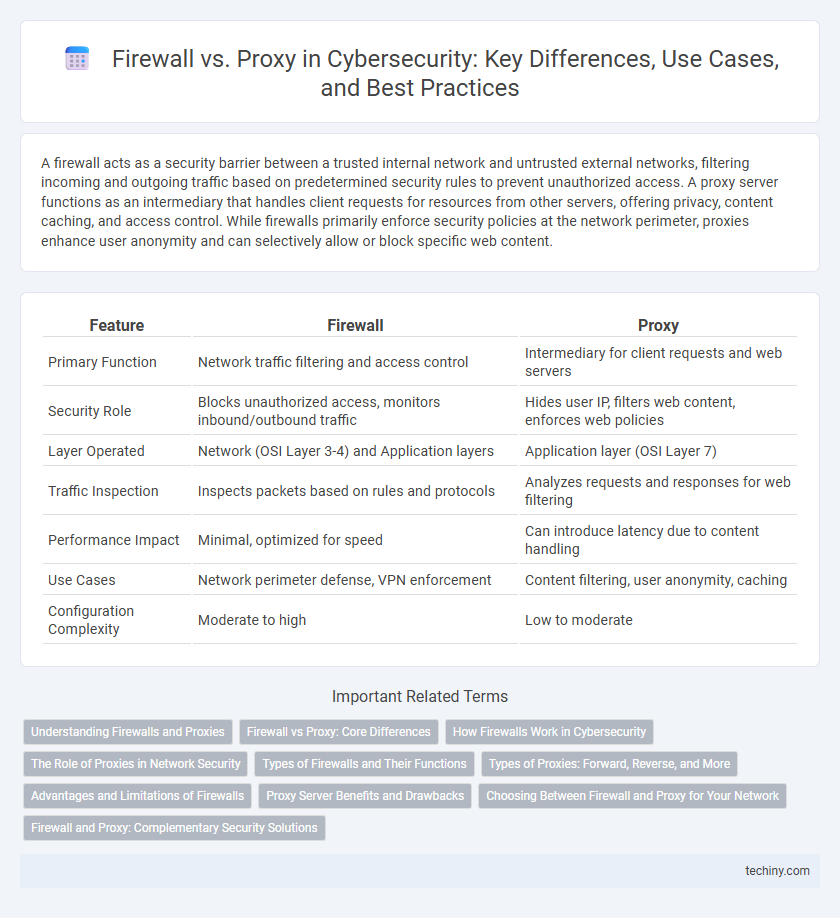
| Feature | Firewall | Proxy |
|---|---|---|
| Primary Function | Network traffic filtering and access control | Intermediary for client requests and web servers |
| Security Role | Blocks unauthorized access, monitors inbound/outbound traffic | Hides user IP, filters web content, enforces web policies |
| Layer Operated | Network (OSI Layer 3-4) and Application layers | Application layer (OSI Layer 7) |
| Traffic Inspection | Inspects packets based on rules and protocols | Analyzes requests and responses for web filtering |
| Performance Impact | Minimal, optimized for speed | Can introduce latency due to content handling |
| Use Cases | Network perimeter defense, VPN enforcement | Content filtering, user anonymity, caching |
| Configuration Complexity | Moderate to high | Low to moderate |
Understanding Firewalls and Proxies
Firewalls act as a barrier between internal networks and external threats by filtering incoming and outgoing traffic based on predetermined security rules, protecting against unauthorized access. Proxies serve as intermediaries that handle client requests to the internet, masking IP addresses and enabling content filtering or monitoring. Understanding the distinct roles of firewalls in network security and proxies in traffic management is crucial for implementing comprehensive cybersecurity measures.
Firewall vs Proxy: Core Differences
Firewalls primarily filter incoming and outgoing network traffic based on predetermined security rules, acting as a barrier between trusted and untrusted networks to prevent unauthorized access. Proxies serve as intermediaries that relay requests between clients and servers, often masking the client's IP address and providing content filtering or caching. While firewalls inspect and control traffic at the network or transport layer, proxies operate at the application layer, making their function and scope distinctly different in cybersecurity infrastructure.
How Firewalls Work in Cybersecurity
Firewalls serve as a critical barrier in cybersecurity by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. They analyze data packets at the network perimeter, filtering out malicious content and unauthorized access attempts to protect internal systems. By enforcing policies like IP blocking and port filtering, firewalls prevent cyber threats such as malware, ransomware, and unauthorized intrusions from compromising sensitive data.
The Role of Proxies in Network Security
Proxies act as intermediaries that mask client IP addresses, enhancing privacy and controlling access to web content by filtering requests based on defined security policies. Unlike firewalls that primarily block or allow traffic based on IP addresses and ports, proxies inspect the content of web traffic, enabling detection of malicious payloads and prevention of data leaks. Deploying proxies in network security frameworks helps organizations enforce granular access controls and monitor user behavior to mitigate cyber threats effectively.
Types of Firewalls and Their Functions
Packet-filtering firewalls monitor incoming and outgoing traffic based on predefined rules, allowing or blocking data packets by IP address, port, or protocol to prevent unauthorized access. Stateful inspection firewalls track the state of active connections and make decisions based on the context of the traffic, enhancing security by ensuring only legitimate sessions pass through. Next-generation firewalls (NGFW) combine traditional firewall capabilities with advanced features like intrusion prevention, application awareness, and deep packet inspection to provide comprehensive network protection against sophisticated cyber threats.
Types of Proxies: Forward, Reverse, and More
Forward proxies act as intermediaries for client requests, enabling users to access external resources while masking their IP addresses and filtering content for security. Reverse proxies sit in front of web servers, handling incoming traffic, improving load balancing, and protecting backend servers from threats by inspecting and filtering requests. Other proxy types include transparent proxies that monitor traffic without modification and anonymous proxies that enhance privacy by concealing user identity during internet access.
Advantages and Limitations of Firewalls
Firewalls provide robust network security by monitoring incoming and outgoing traffic based on predetermined security rules, effectively blocking unauthorized access and preventing cyber threats such as malware and intrusion attempts. Their advantages include real-time traffic filtering, customizable rule sets for granular control, and protecting entire networks or individual devices from external attacks. Limitations of firewalls involve difficulty in detecting encrypted threats, inability to prevent insider attacks, and potential performance impacts due to traffic inspection overhead.
Proxy Server Benefits and Drawbacks
Proxy servers enhance cybersecurity by masking the user's IP address, filtering web traffic, and controlling access to external websites, which improves privacy and enforces corporate policies. They reduce bandwidth usage through caching, speeding up access to frequently visited sites while providing content filtering and monitoring capabilities. However, proxy servers can introduce latency, may not encrypt traffic like VPNs or firewalls, and can be bypassed by users with technical knowledge, limiting their effectiveness in high-security environments.
Choosing Between Firewall and Proxy for Your Network
Choosing between a firewall and a proxy for your network depends on the level of security and control required. Firewalls provide robust protection by monitoring and filtering incoming and outgoing traffic based on predefined security rules, effectively blocking unauthorized access and threats. Proxies serve as intermediaries that manage client requests and can enhance privacy and access control but may not offer comprehensive protection against all types of cyber threats.
Firewall and Proxy: Complementary Security Solutions
Firewalls and proxies serve distinct but complementary roles in cybersecurity by providing robust network protection and enhanced privacy controls. Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules, effectively blocking unauthorized access and preventing cyber threats. Proxies act as intermediaries for client requests, masking IP addresses and filtering content to enhance user privacy and secure web traffic, thereby augmenting the overall defense strategy when deployed alongside firewalls.
Firewall vs Proxy Infographic
 techiny.com
techiny.com