Firewalls serve as a security barrier that monitors and controls incoming and outgoing network traffic based on predetermined security rules, while proxies act as intermediaries that route client requests to external servers, masking the user's IP address. Firewalls primarily prevent unauthorized access and protect the network perimeter, whereas proxies enhance privacy and can filter content or cache data to improve performance. Understanding the key differences between firewalls and proxies is essential for implementing a layered cybersecurity strategy that balances protection, anonymity, and traffic management.
Table of Comparison
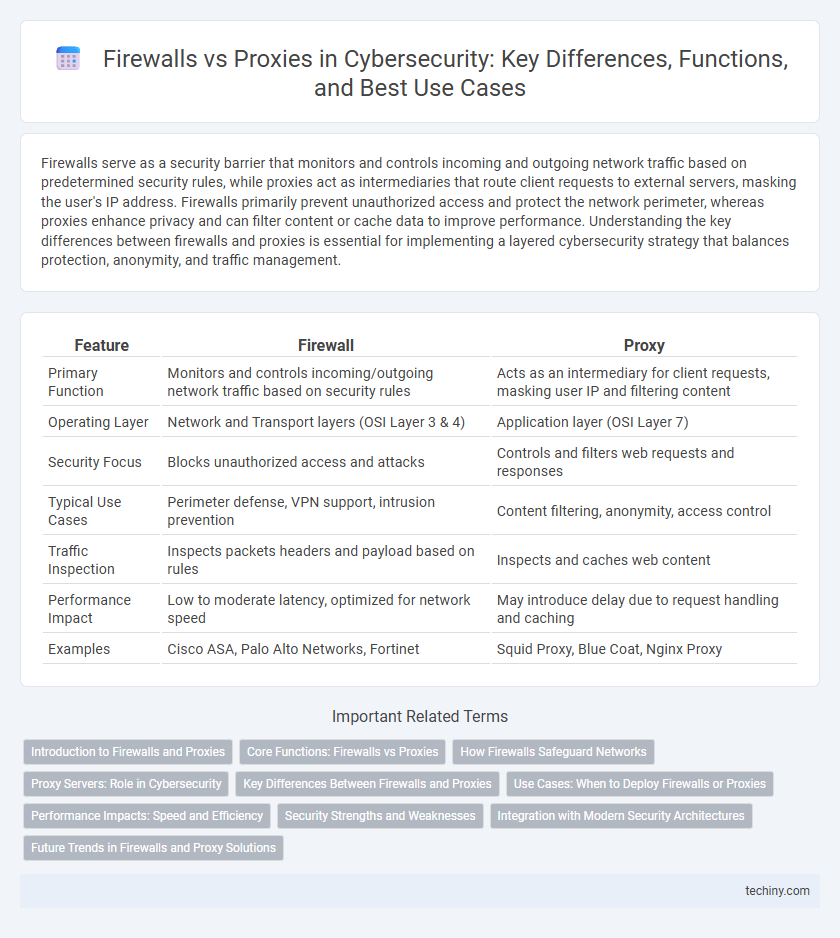
| Feature | Firewall | Proxy |
|---|---|---|
| Primary Function | Monitors and controls incoming/outgoing network traffic based on security rules | Acts as an intermediary for client requests, masking user IP and filtering content |
| Operating Layer | Network and Transport layers (OSI Layer 3 & 4) | Application layer (OSI Layer 7) |
| Security Focus | Blocks unauthorized access and attacks | Controls and filters web requests and responses |
| Typical Use Cases | Perimeter defense, VPN support, intrusion prevention | Content filtering, anonymity, access control |
| Traffic Inspection | Inspects packets headers and payload based on rules | Inspects and caches web content |
| Performance Impact | Low to moderate latency, optimized for network speed | May introduce delay due to request handling and caching |
| Examples | Cisco ASA, Palo Alto Networks, Fortinet | Squid Proxy, Blue Coat, Nginx Proxy |
Introduction to Firewalls and Proxies
Firewalls serve as a security barrier between trusted internal networks and untrusted external networks, filtering incoming and outgoing traffic based on predetermined security rules to prevent unauthorized access. Proxies act as intermediaries between users and the internet, masking client IP addresses and monitoring requests to enhance privacy and control web traffic. Both technologies are foundational in cybersecurity, offering distinct yet complementary layers of network protection and access management.
Core Functions: Firewalls vs Proxies
Firewalls primarily control incoming and outgoing network traffic based on predetermined security rules to prevent unauthorized access. Proxies act as intermediaries between users and the internet, masking IP addresses and filtering web content to enhance privacy and control. Both tools serve critical but distinct roles in network security, with firewalls enforcing network boundaries and proxies managing user requests and content filtering.
How Firewalls Safeguard Networks
Firewalls safeguard networks by monitoring and controlling incoming and outgoing traffic based on predetermined security rules, effectively blocking unauthorized access and cyber threats. They create a barrier between trusted internal networks and untrusted external networks, filtering data packets to prevent malicious activities such as hacking, malware, and data breaches. Firewalls also log network traffic, enabling administrators to detect and respond to suspicious behavior in real time, enhancing overall network security.
Proxy Servers: Role in Cybersecurity
Proxy servers serve as intermediary gateways between users and the internet, filtering inbound and outbound traffic to prevent unauthorized access and data breaches. They enhance cybersecurity by masking IP addresses, enforcing organizational policies, and blocking malicious websites or content. Proxies also enable monitoring and logging of network activity, supporting threat detection and compliance with security regulations.
Key Differences Between Firewalls and Proxies
Firewalls serve as a security barrier that monitors and controls incoming and outgoing network traffic based on predefined security rules, while proxies act as intermediaries that handle client requests to other servers, often providing anonymity and content filtering. Firewalls operate at both the network and transport layers to block unauthorized access, whereas proxies primarily function at the application layer, managing specific protocols such as HTTP or FTP. The key difference lies in firewalls focusing on access control and threat prevention at a broader network level, while proxies specialize in mediating user requests and enhancing privacy.
Use Cases: When to Deploy Firewalls or Proxies
Firewalls are best deployed to protect entire networks by filtering inbound and outbound traffic based on predetermined security rules, making them ideal for perimeter defense and intrusion prevention. Proxies serve as intermediaries for client requests, enabling content filtering, user anonymity, and access control, which is beneficial for monitoring and controlling employee internet usage. Use firewalls when securing network layers and traffic flow, while proxies are preferred for managing application-level access and enforcing organizational browsing policies.
Performance Impacts: Speed and Efficiency
Firewalls primarily filter traffic based on predetermined security rules, impacting speed minimally while maintaining robust network protection. Proxies can introduce additional latency by inspecting and caching content, which may slow down data transmission but enhance efficiency through traffic management. Evaluating performance impacts depends on network size and usage patterns, where firewalls optimize speed and proxies improve resource utilization.
Security Strengths and Weaknesses
Firewalls provide robust perimeter defense by filtering incoming and outgoing network traffic based on predefined security rules, effectively blocking unauthorized access and preventing malware infiltration. Proxies enhance privacy and control by masking IP addresses and selectively caching content, but they offer limited protection against direct network attacks and cannot inspect encrypted traffic at the packet level. Combining firewalls' strong protocol-level filtering with proxies' content control creates a layered security approach that mitigates individual weaknesses and strengthens overall cybersecurity posture.
Integration with Modern Security Architectures
Firewalls and proxies serve distinct roles in modern security architectures, with firewalls primarily controlling network traffic based on predefined security rules, while proxies act as intermediaries to filter content and conceal user identities. Integration of firewalls with Security Information and Event Management (SIEM) systems enhances real-time threat detection and response capabilities. Proxies combined with Data Loss Prevention (DLP) and Secure Web Gateways (SWG) align with Zero Trust models by enforcing granular access control and monitoring outbound traffic.
Future Trends in Firewalls and Proxy Solutions
Next-generation firewalls (NGFWs) integrate AI-powered threat detection and behavioral analytics to enhance real-time intrusion prevention and adaptive security policies. Proxy solutions are evolving with encrypted traffic inspection and zero-trust network access (ZTNA) to provide granular control and secure remote connectivity. Both technologies increasingly leverage cloud-based management and automation for scalable, context-aware cybersecurity defenses.
Firewalls vs Proxies Infographic
 techiny.com
techiny.com