Forward Secrecy (FS) ensures that session keys cannot be compromised even if the server's private key is exposed in the future, protecting past communications from retrospective decryption. Perfect Forward Secrecy (PFS) is a stronger implementation where every session generates unique keys independently, preventing attackers from deriving past session keys from any compromised long-term keys. PFS is essential for robust cybersecurity as it guarantees that each encrypted session remains secure, even in the event of key exposure.
Table of Comparison
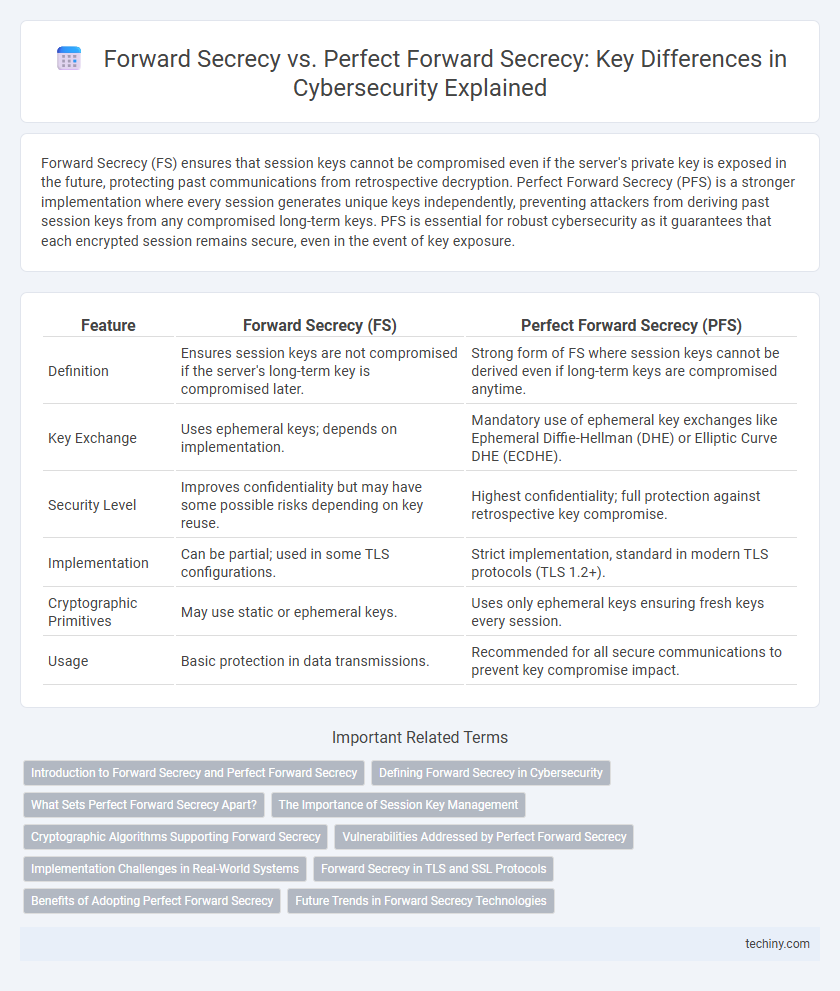
| Feature | Forward Secrecy (FS) | Perfect Forward Secrecy (PFS) |
|---|---|---|
| Definition | Ensures session keys are not compromised if the server's long-term key is compromised later. | Strong form of FS where session keys cannot be derived even if long-term keys are compromised anytime. |
| Key Exchange | Uses ephemeral keys; depends on implementation. | Mandatory use of ephemeral key exchanges like Ephemeral Diffie-Hellman (DHE) or Elliptic Curve DHE (ECDHE). |
| Security Level | Improves confidentiality but may have some possible risks depending on key reuse. | Highest confidentiality; full protection against retrospective key compromise. |
| Implementation | Can be partial; used in some TLS configurations. | Strict implementation, standard in modern TLS protocols (TLS 1.2+). |
| Cryptographic Primitives | May use static or ephemeral keys. | Uses only ephemeral keys ensuring fresh keys every session. |
| Usage | Basic protection in data transmissions. | Recommended for all secure communications to prevent key compromise impact. |
Introduction to Forward Secrecy and Perfect Forward Secrecy
Forward Secrecy (FS) ensures that session keys used for encrypting data remain secure even if the server's long-term private key is compromised later, preventing decryption of past communications. Perfect Forward Secrecy (PFS) is a stronger version of FS, guaranteeing that each session key is unique and never reused by employing ephemeral key exchanges like Diffie-Hellman, which enhances resistance against key compromise attacks. Implementing PFS in protocols such as TLS significantly improves confidentiality by isolating each communication session from the risk of exposure due to key leakage.
Defining Forward Secrecy in Cybersecurity
Forward Secrecy in cybersecurity ensures that session keys used to encrypt communications are not compromised even if the server's long-term private key is exposed in the future. This security feature protects past encrypted sessions from being decrypted retroactively, maintaining confidentiality against data breaches. By generating unique session keys for each communication session, Forward Secrecy minimizes the risk of mass data exposure, enhancing overall cryptographic security.
What Sets Perfect Forward Secrecy Apart?
Perfect Forward Secrecy (PFS) ensures that session keys are not compromised even if the server's long-term private key is exposed, providing enhanced security compared to basic forward secrecy. PFS achieves this by generating unique, ephemeral session keys for each communication session, preventing attackers from decrypting past sessions. This critical security feature is widely implemented in modern protocols like TLS to safeguard sensitive data against future key compromises.
The Importance of Session Key Management
Forward Secrecy ensures that session keys cannot be compromised if long-term keys are exposed, by generating unique keys for each session. Perfect Forward Secrecy (PFS) enhances this by guaranteeing that even if private keys are compromised, past communications remain secure due to ephemeral key exchange mechanisms like Diffie-Hellman. Effective session key management minimizes risks of data breaches, safeguards encrypted communications, and supports regulatory compliance in cybersecurity frameworks.
Cryptographic Algorithms Supporting Forward Secrecy
Forward Secrecy is supported primarily by ephemeral key exchange algorithms like Diffie-Hellman Ephemeral (DHE) and Elliptic Curve Diffie-Hellman Ephemeral (ECDHE), which generate unique session keys for each communication, preventing retrospective decryption even if long-term keys are compromised. Perfect Forward Secrecy (PFS) is a stringent implementation of Forward Secrecy principles, enforced by protocols mandating these ephemeral key mechanisms to ensure no session keys are ever stored or reused. Cryptographic protocols such as TLS 1.3 and modern versions of SSH incorporate ECDHE and DHE to provide robust Forward Secrecy, safeguarding encrypted data against future key exposure.
Vulnerabilities Addressed by Perfect Forward Secrecy
Perfect Forward Secrecy (PFS) enhances traditional Forward Secrecy by ensuring that session keys cannot be compromised even if long-term private keys are exposed, effectively mitigating risks from future attacks. PFS addresses vulnerabilities such as retrospective decryption, where attackers intercept encrypted traffic and decrypt it once private keys are obtained, and key compromise impersonation, protecting ongoing sessions from being decrypted. By generating unique session keys for each communication, PFS significantly improves the confidentiality and security of cryptographic protocols against advanced persistent threats.
Implementation Challenges in Real-World Systems
Implementing Forward Secrecy (FS) and Perfect Forward Secrecy (PFS) in real-world systems faces challenges such as increased computational overhead and the need for frequent key exchanges, which can strain system resources and impact latency. PFS requires generating unique session keys for every communication session, complicating key management and demanding robust protocol support like TLS 1.3. Balancing security benefits with performance constraints and ensuring seamless integration into legacy systems remains a critical hurdle for widespread adoption.
Forward Secrecy in TLS and SSL Protocols
Forward Secrecy in TLS and SSL protocols ensures that session keys are not compromised even if the server's long-term private key is exposed, by generating unique keys for each session through ephemeral key exchanges. This feature significantly enhances data confidentiality by preventing attackers from decrypting past communications despite future key compromises. Implementing Forward Secrecy typically involves using ephemeral Diffie-Hellman (DHE) or elliptic-curve Diffie-Hellman (ECDHE) key exchange algorithms within TLS versions 1.2 and 1.3.
Benefits of Adopting Perfect Forward Secrecy
Perfect Forward Secrecy (PFS) ensures that session keys cannot be compromised even if long-term private keys are exposed, significantly enhancing data confidentiality in cybersecurity. By generating unique encryption keys for each session, PFS mitigates risks from retrospective decryption attacks and protects sensitive communications against future quantum computing threats. Adopting Perfect Forward Secrecy strengthens overall network security resilience and compliance with stringent data protection standards like GDPR and HIPAA.
Future Trends in Forward Secrecy Technologies
Forward Secrecy (FS) ensures session keys remain secure even if long-term keys are compromised, while Perfect Forward Secrecy (PFS) extends this principle by generating ephemeral keys that are never reused. Emerging trends in forward secrecy technologies emphasize integration with post-quantum cryptographic algorithms to safeguard against quantum computing threats, enhancing resilience in secure communications. Enhanced protocols leveraging advanced key exchange mechanisms like lattice-based cryptography are gaining traction to future-proof data confidentiality in evolving cybersecurity landscapes.
Forward Secrecy vs Perfect Forward Secrecy Infographic
 techiny.com
techiny.com