Heuristic analysis detects cyber threats by examining behavioral patterns and suspicious activities, enabling identification of novel or unknown malware. Signature-based detection relies on known malware signatures, providing fast and accurate identification of previously documented threats but failing against new variants. Combining both methods enhances cybersecurity by balancing speed, accuracy, and adaptability to emerging attacks.
Table of Comparison
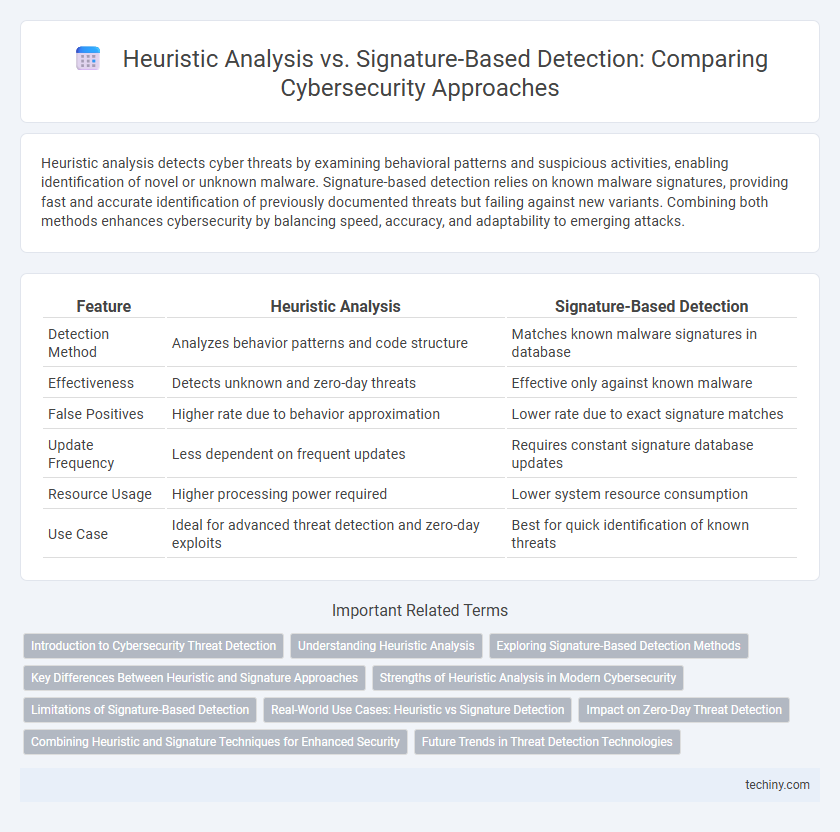
| Feature | Heuristic Analysis | Signature-Based Detection |
|---|---|---|
| Detection Method | Analyzes behavior patterns and code structure | Matches known malware signatures in database |
| Effectiveness | Detects unknown and zero-day threats | Effective only against known malware |
| False Positives | Higher rate due to behavior approximation | Lower rate due to exact signature matches |
| Update Frequency | Less dependent on frequent updates | Requires constant signature database updates |
| Resource Usage | Higher processing power required | Lower system resource consumption |
| Use Case | Ideal for advanced threat detection and zero-day exploits | Best for quick identification of known threats |
Introduction to Cybersecurity Threat Detection
Heuristic analysis identifies cybersecurity threats by examining behavior patterns and irregularities, enabling detection of new or unknown malware. Signature-based detection relies on predefined malware signatures stored in databases to quickly recognize known threats. Combining both methods enhances threat detection accuracy and reduces vulnerabilities in cybersecurity systems.
Understanding Heuristic Analysis
Heuristic analysis in cybersecurity detects threats by examining behavioral patterns and anomalies rather than relying solely on known malware signatures. This proactive method identifies new and evolving malware variants by analyzing code structure and suspicious activities, enabling the detection of zero-day exploits. Unlike signature-based detection, heuristic analysis offers adaptive protection against emerging cyber threats and polymorphic malware.
Exploring Signature-Based Detection Methods
Signature-based detection methods in cybersecurity rely on identifying known patterns of malware by matching files or activities against a database of recognized signatures, enabling rapid and accurate threat identification. These methods excel in detecting previously encountered malware with high precision, but struggle to identify new or obfuscated threats without updated signature databases. Continuous updating and integration with other detection techniques are essential to maintain effectiveness against evolving cyber threats.
Key Differences Between Heuristic and Signature Approaches
Heuristic analysis in cybersecurity identifies threats by examining behaviors and patterns that suggest malicious intent, enabling detection of unknown or zero-day malware. Signature-based detection relies on pre-existing databases of known malware signatures, offering precise identification but limited to recognized threats. The key difference lies in heuristic methods providing proactive defense against emerging threats while signature-based systems offer reactive protection grounded in historical data.
Strengths of Heuristic Analysis in Modern Cybersecurity
Heuristic analysis excels in modern cybersecurity by detecting unknown and zero-day malware through behavioral patterns and anomaly detection, unlike signature-based detection which relies on known threat databases. Its strength lies in identifying novel threats by evaluating code behavior, enabling proactive defense mechanisms against emerging cyberattacks. This advanced approach reduces false negatives and improves real-time threat detection, enhancing overall network security resilience.
Limitations of Signature-Based Detection
Signature-based detection in cybersecurity struggles to identify new or unknown malware due to its reliance on predefined signatures stored in threat databases. This method fails against polymorphic and zero-day attacks that constantly change their code to evade static detection patterns. Consequently, it requires frequent updates and cannot effectively detect emerging threats without prior knowledge.
Real-World Use Cases: Heuristic vs Signature Detection
Heuristic analysis excels in identifying previously unknown or polymorphic malware by analyzing behavior patterns and code anomalies, making it ideal for zero-day threat detection in dynamic environments. Signature-based detection remains effective for quickly identifying known threats through predefined signatures, often used in antivirus software for enterprise networks with established threat databases. Real-world deployments commonly combine both methods to enhance cybersecurity defenses, leveraging heuristic analysis for emerging threats and signature detection for rapid response against known malware strains.
Impact on Zero-Day Threat Detection
Heuristic analysis enhances zero-day threat detection by identifying suspicious behavior patterns and anomalies even when specific malware signatures are absent. Signature-based detection relies on known malware fingerprints, limiting its effectiveness against newly emerging threats without established signatures. Employing heuristic methods significantly improves proactive defense capabilities against previously unknown cyberattacks and zero-day vulnerabilities.
Combining Heuristic and Signature Techniques for Enhanced Security
Combining heuristic analysis with signature-based detection significantly enhances cybersecurity by merging the strengths of both methods, enabling the identification of known threats through signature databases and unknown or evolving malware via behavioral patterns. This hybrid approach improves detection rates and reduces false positives by leveraging machine learning algorithms and real-time threat intelligence integration. Organizations adopting this dual strategy achieve comprehensive protection against sophisticated cyberattacks and zero-day exploits.
Future Trends in Threat Detection Technologies
Heuristic analysis and signature-based detection represent evolving strategies in cybersecurity threat detection, where heuristic methods leverage behavioral patterns and machine learning to identify unknown threats beyond the limitations of traditional signature databases. Future trends emphasize the integration of artificial intelligence and real-time analytics, enhancing predictive capabilities and adaptive response to sophisticated cyber attacks. Advancements in cloud-based threat intelligence sharing and automated incident response will further transform threat detection, enabling faster identification and mitigation of emerging vulnerabilities.
Heuristic Analysis vs Signature-Based Detection Infographic
 techiny.com
techiny.com