Host-based Intrusion Detection Systems (HIDS) monitor and analyze activities on individual devices, providing detailed insights into local threats and system integrity. Network-based Intrusion Detection Systems (NIDS) inspect network traffic to identify suspicious patterns and potential attacks across the entire network. Combining HIDS and NIDS enhances overall cybersecurity by delivering comprehensive threat detection at both the host and network levels.
Table of Comparison
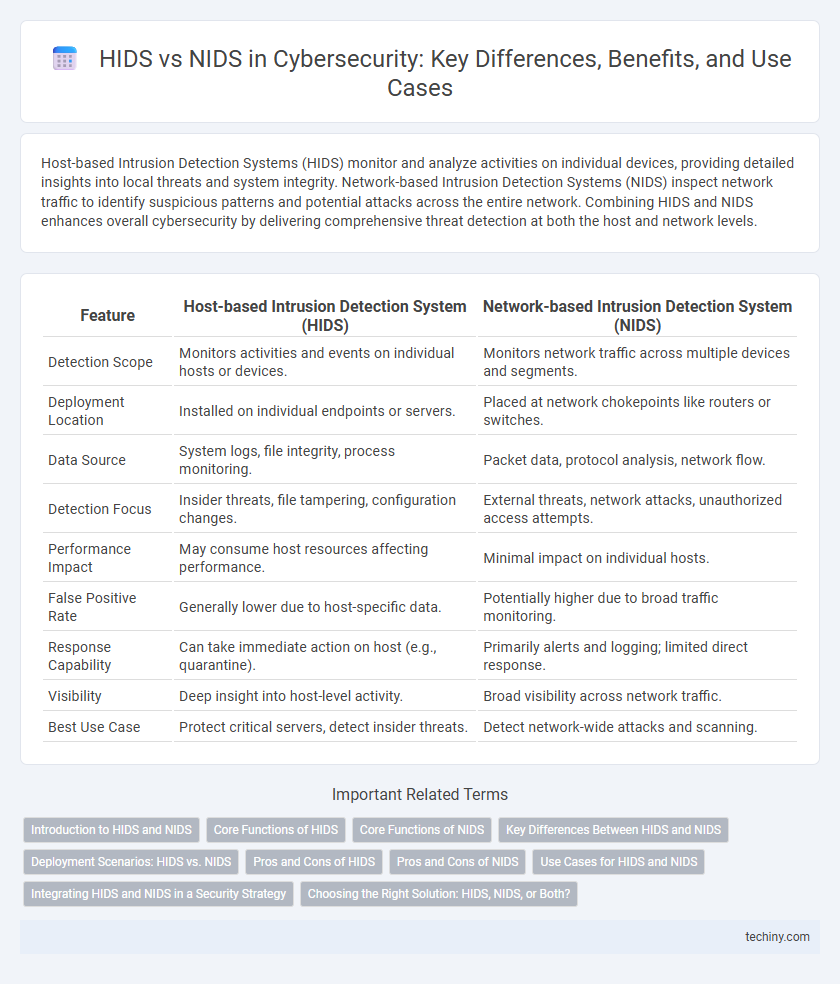
| Feature | Host-based Intrusion Detection System (HIDS) | Network-based Intrusion Detection System (NIDS) |
|---|---|---|
| Detection Scope | Monitors activities and events on individual hosts or devices. | Monitors network traffic across multiple devices and segments. |
| Deployment Location | Installed on individual endpoints or servers. | Placed at network chokepoints like routers or switches. |
| Data Source | System logs, file integrity, process monitoring. | Packet data, protocol analysis, network flow. |
| Detection Focus | Insider threats, file tampering, configuration changes. | External threats, network attacks, unauthorized access attempts. |
| Performance Impact | May consume host resources affecting performance. | Minimal impact on individual hosts. |
| False Positive Rate | Generally lower due to host-specific data. | Potentially higher due to broad traffic monitoring. |
| Response Capability | Can take immediate action on host (e.g., quarantine). | Primarily alerts and logging; limited direct response. |
| Visibility | Deep insight into host-level activity. | Broad visibility across network traffic. |
| Best Use Case | Protect critical servers, detect insider threats. | Detect network-wide attacks and scanning. |
Introduction to HIDS and NIDS
Host-based Intrusion Detection Systems (HIDS) monitor and analyze internal system activities such as file integrity, log files, and system calls to detect suspicious behavior and potential threats. Network-based Intrusion Detection Systems (NIDS) examine network traffic in real-time, capturing and analyzing packets to identify malicious activities or policy violations across a network segment. Both HIDS and NIDS are critical components in a comprehensive cybersecurity strategy, providing layered defense through detailed host monitoring and broad network surveillance.
Core Functions of HIDS
Host-based Intrusion Detection Systems (HIDS) monitor and analyze the internals of a computing system for suspicious activities by inspecting system logs, file integrity, and running processes. HIDS provides real-time alerts on unauthorized changes, privilege escalation, and malware infections by leveraging kernel-level monitoring and system call analysis. Its core functions include detailed audit trail generation, policy enforcement, and identifying anomalous behavior originating from inside the host environment.
Core Functions of NIDS
Network Intrusion Detection Systems (NIDS) monitor and analyze network traffic in real time to detect suspicious activities or potential threats. Core functions of NIDS include packet sniffing, protocol analysis, and anomaly detection, enabling early identification of network-based attacks such as denial-of-service (DoS) or port scanning. By leveraging signature and behavior-based detection methods, NIDS provide comprehensive oversight of network security without impacting host performance.
Key Differences Between HIDS and NIDS
Host-based Intrusion Detection Systems (HIDS) monitor and analyze activities on individual devices, providing detailed insights into system logs, file integrity, and processes, while Network-based Intrusion Detection Systems (NIDS) scrutinize network traffic across multiple devices to detect suspicious patterns and potential attacks. HIDS operates at the host level, allowing for deep detection of insider threats and unauthorized changes, whereas NIDS offers a broad perspective by capturing network packets and spotting widespread threats like DDoS or port scanning. The choice between HIDS and NIDS depends on the security requirements, with HIDS excelling in endpoint protection and NIDS in network perimeter defense.
Deployment Scenarios: HIDS vs. NIDS
Host-based Intrusion Detection Systems (HIDS) excel in monitoring individual devices, providing granular visibility into system-level activities such as file modifications and user behavior, making them ideal for endpoints with sensitive data. Network-based Intrusion Detection Systems (NIDS) are deployed at strategic points within the network infrastructure to analyze traffic flows and detect malicious patterns, offering broad coverage across multiple devices and network segments. Deploying HIDS complements NIDS by enabling comprehensive threat detection across both host-specific and network-wide attack vectors.
Pros and Cons of HIDS
Host-based Intrusion Detection Systems (HIDS) provide granular monitoring by analyzing internal system logs, file integrity, and user activities, allowing for detailed detection of insider threats and malicious behavior directly on the host. However, HIDS can consume significant system resources, potentially impacting host performance and generating high volumes of alerts that may require extensive management. Unlike Network-based IDS, HIDS lacks visibility into network-wide traffic, limiting its ability to detect attacks that transit multiple systems or occur outside the monitored host.
Pros and Cons of NIDS
Network Intrusion Detection Systems (NIDS) offer real-time monitoring of network traffic, enabling the detection of malicious activities and unauthorized access across multiple devices. NIDS can cover large network segments without installing software on individual hosts, making deployment less intrusive and more scalable. However, NIDS may struggle with encrypted traffic analysis, generate false positives due to high network volume, and cannot inspect internal host activities unlike host-based systems.
Use Cases for HIDS and NIDS
Host Intrusion Detection Systems (HIDS) are ideally used for monitoring critical servers and endpoints where deep visibility into file integrity, log analysis, and real-time behavior monitoring is essential to detect insider threats and unauthorized changes. Network Intrusion Detection Systems (NIDS) excel in environments requiring perimeter defense by analyzing network traffic for malicious patterns, detecting external attacks such as DDoS or port scanning, and safeguarding against lateral movement within a network. Combining HIDS and NIDS provides comprehensive security coverage by correlating host-level and network-level data for more accurate threat detection and response.
Integrating HIDS and NIDS in a Security Strategy
Integrating Host-based Intrusion Detection Systems (HIDS) and Network-based Intrusion Detection Systems (NIDS) enhances cybersecurity by providing comprehensive threat detection at both the endpoint and network levels. HIDS monitors internal system activities, including file integrity and log analysis, while NIDS examines network traffic for suspicious patterns and attacks. Combining these systems enables real-time correlation of host and network events, improving incident response accuracy and reducing false positives.
Choosing the Right Solution: HIDS, NIDS, or Both?
Choosing between Host-based Intrusion Detection Systems (HIDS) and Network-based Intrusion Detection Systems (NIDS) depends on the organization's security needs and infrastructure complexity. HIDS provides detailed monitoring of individual endpoints, ideal for detecting insider threats and unauthorized file changes, while NIDS offers broader network traffic analysis to identify external attacks and suspicious activities across multiple devices. Combining both HIDS and NIDS creates a layered defense strategy, enhancing overall cybersecurity by covering endpoint vulnerabilities and network-wide threats.
HIDS vs NIDS Infographic
 techiny.com
techiny.com