MAC filtering restricts network access by allowing only devices with specific hardware addresses, enhancing security through device authentication but potentially becoming cumbersome to manage in large networks. VLAN segmentation divides a larger network into smaller, isolated segments, improving security by containing broadcast traffic and minimizing the attack surface within each VLAN. Combining MAC filtering with VLAN segmentation creates layered security controls that reduce unauthorized access and limit lateral movement in corporate networks.
Table of Comparison
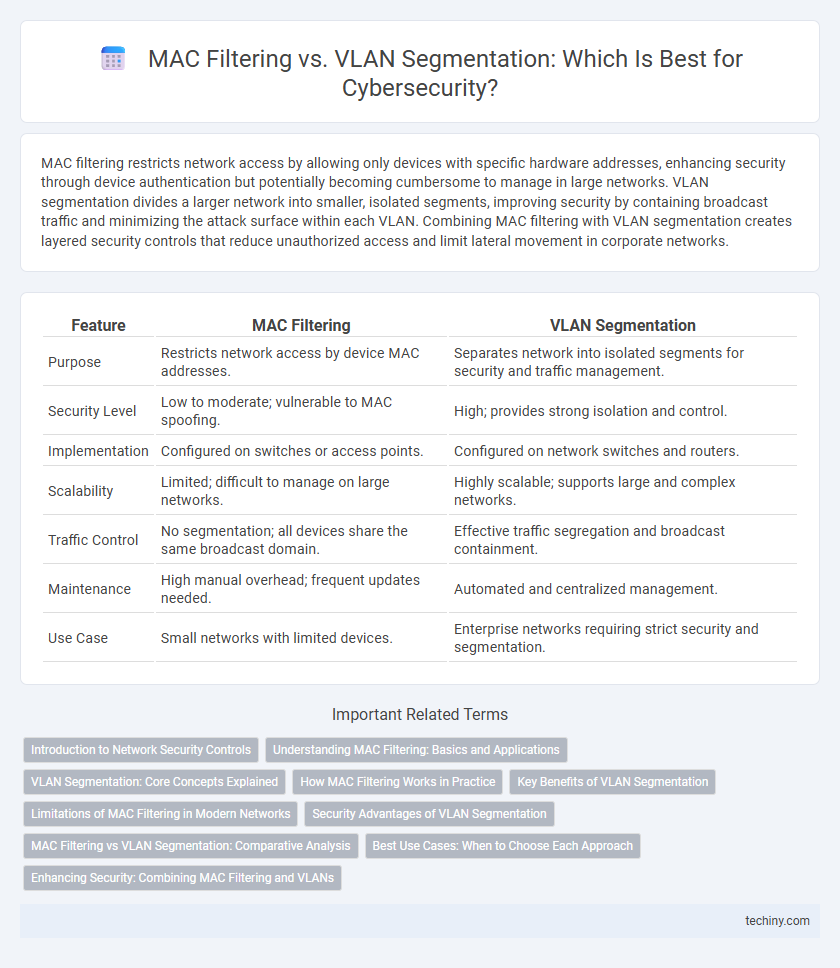
| Feature | MAC Filtering | VLAN Segmentation |
|---|---|---|
| Purpose | Restricts network access by device MAC addresses. | Separates network into isolated segments for security and traffic management. |
| Security Level | Low to moderate; vulnerable to MAC spoofing. | High; provides strong isolation and control. |
| Implementation | Configured on switches or access points. | Configured on network switches and routers. |
| Scalability | Limited; difficult to manage on large networks. | Highly scalable; supports large and complex networks. |
| Traffic Control | No segmentation; all devices share the same broadcast domain. | Effective traffic segregation and broadcast containment. |
| Maintenance | High manual overhead; frequent updates needed. | Automated and centralized management. |
| Use Case | Small networks with limited devices. | Enterprise networks requiring strict security and segmentation. |
Introduction to Network Security Controls
MAC filtering enhances network security by restricting device access based on unique hardware addresses, effectively preventing unauthorized entry. VLAN segmentation improves traffic management and security by isolating network segments, reducing broadcast domains, and containing potential threats within specific virtual networks. Both controls are fundamental in strengthening perimeter defenses and managing internal network risks.
Understanding MAC Filtering: Basics and Applications
MAC filtering is a network security method that controls device access by allowing or denying traffic based on unique Media Access Control (MAC) addresses. This technique is effective in restricting unauthorized devices within smaller networks but lacks scalability and is vulnerable to MAC address spoofing attacks. Implementing MAC filtering alongside VLAN segmentation enhances overall network security by providing both access control and logical network separation.
VLAN Segmentation: Core Concepts Explained
VLAN segmentation divides a physical network into multiple logical networks, enhancing security by isolating traffic based on function, department, or user role. This method reduces broadcast domains, mitigates the risk of unauthorized access, and improves network performance through targeted traffic management. Unlike MAC filtering, which controls access at the device level, VLAN segmentation enforces security policies through network architecture, providing scalable and granular control over data flows.
How MAC Filtering Works in Practice
MAC filtering operates by allowing network administrators to specify which devices can connect to the network based on their unique MAC addresses, effectively permitting or blocking access at the data link layer. In practice, network switches or wireless access points maintain a whitelist or blacklist of MAC addresses, enabling enforcement of device-level access policies. This method provides a basic layer of security by restricting unauthorized devices but can be circumvented through MAC spoofing, highlighting the need for complementary security measures like VLAN segmentation.
Key Benefits of VLAN Segmentation
VLAN segmentation enhances network security by isolating sensitive data and restricting access to specific network segments, reducing the attack surface. It improves traffic management and minimizes broadcast storms, ensuring efficient bandwidth usage and enhanced performance. VLANs enable scalable network design with granular control over user access, supporting compliance with security policies and regulatory requirements.
Limitations of MAC Filtering in Modern Networks
MAC filtering faces significant limitations in modern networks due to its vulnerability to MAC address spoofing and its inability to effectively scale with large and dynamic network environments. Unlike VLAN segmentation, which provides robust traffic isolation and improved security by logically separating network segments, MAC filtering offers only basic access control that can be easily bypassed by attackers. This makes MAC filtering insufficient as a standalone security measure in protecting against advanced network intrusions and unauthorized access.
Security Advantages of VLAN Segmentation
VLAN segmentation enhances network security by isolating sensitive data traffic within distinct virtual networks, limiting the attack surface from unauthorized access. Unlike MAC filtering, which relies on physical address validation and can be bypassed through MAC spoofing, VLAN segmentation enforces traffic separation at the switch level, reducing the risk of lateral movement by attackers. This granular control over network segments supports compliance with security policies and improves incident containment during cyber threats.
MAC Filtering vs VLAN Segmentation: Comparative Analysis
MAC filtering limits network access by allowing only pre-approved device MAC addresses, providing a basic layer of security but susceptible to MAC spoofing. VLAN segmentation isolates network traffic into separate virtual LANs, enhancing security by containing broadcast domains and restricting lateral movement of threats. Compared to MAC filtering, VLAN segmentation offers more robust protection through improved traffic control and network segmentation capabilities.
Best Use Cases: When to Choose Each Approach
MAC filtering is best suited for small networks where controlling device access based on unique hardware addresses enhances security with minimal complexity. VLAN segmentation excels in larger, dynamic environments requiring scalable network segmentation, improved traffic management, and isolation between different departments or user groups. Choose MAC filtering for straightforward access control and VLANs for comprehensive network organization and threat containment.
Enhancing Security: Combining MAC Filtering and VLANs
Combining MAC filtering and VLAN segmentation significantly enhances network security by restricting device access through MAC address whitelisting and isolating traffic within distinct VLANs to limit broadcast domains and potential attack surfaces. MAC filtering enforces strict device-level control, while VLAN segmentation partitions the network logically, preventing unauthorized lateral movement between segments. This layered approach mitigates risks of MAC spoofing and internal threats, ensuring robust protection for sensitive resources and critical infrastructure.
MAC Filtering vs VLAN Segmentation Infographic
 techiny.com
techiny.com