Mandatory Access Control (MAC) enforces strict security policies by restricting user permissions based on predefined rules set by administrators, ensuring consistent and centralized control over resource access. Discretionary Access Control (DAC) allows owners of resources to determine access permissions, providing flexibility but introducing potential risks due to user-managed controls. MAC is favored in high-security environments for its robustness, while DAC suits less sensitive contexts prioritizing ease of management.
Table of Comparison
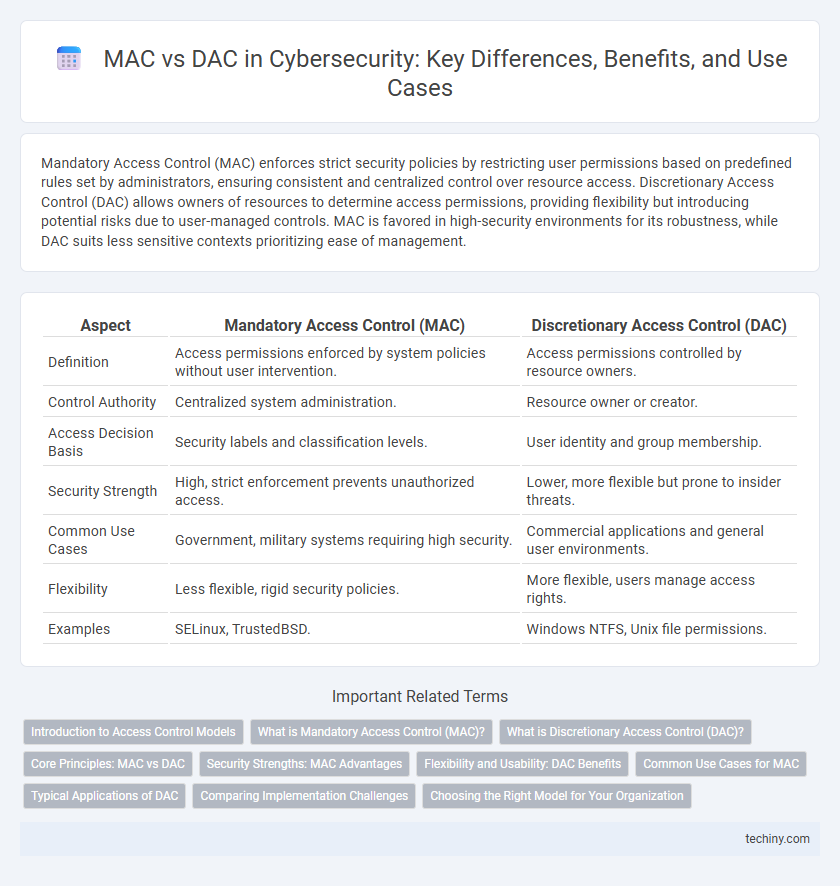
| Aspect | Mandatory Access Control (MAC) | Discretionary Access Control (DAC) |
|---|---|---|
| Definition | Access permissions enforced by system policies without user intervention. | Access permissions controlled by resource owners. |
| Control Authority | Centralized system administration. | Resource owner or creator. |
| Access Decision Basis | Security labels and classification levels. | User identity and group membership. |
| Security Strength | High, strict enforcement prevents unauthorized access. | Lower, more flexible but prone to insider threats. |
| Common Use Cases | Government, military systems requiring high security. | Commercial applications and general user environments. |
| Flexibility | Less flexible, rigid security policies. | More flexible, users manage access rights. |
| Examples | SELinux, TrustedBSD. | Windows NTFS, Unix file permissions. |
Introduction to Access Control Models
Mandatory Access Control (MAC) enforces strict policies defined by a central authority, restricting user permissions based on security labels and classification levels, commonly used in government and military environments. Discretionary Access Control (DAC) allows data owners to set access permissions at their discretion, offering flexibility but potentially higher risk due to user-managed controls. Understanding the differences between MAC and DAC is crucial for implementing effective access control strategies tailored to varying organizational security requirements.
What is Mandatory Access Control (MAC)?
Mandatory Access Control (MAC) is a security model where access permissions are regulated by a central authority based on predefined policies, rather than user discretion. MAC enforces strict access controls by classifying all users and data into security levels, typically using labels such as "confidential" or "top secret." This approach ensures high-level protection in environments requiring robust data confidentiality, like military or government systems.
What is Discretionary Access Control (DAC)?
Discretionary Access Control (DAC) is a security model where resource owners have the authority to determine access permissions for other users, enabling flexible and user-driven control over sensitive data. In DAC systems, access rights can be assigned or revoked at the discretion of the owner, often using access control lists (ACLs) or user identifiers to define permissions. This model contrasts with Mandatory Access Control (MAC) by prioritizing user autonomy over strict, centralized security policies.
Core Principles: MAC vs DAC
Mandatory Access Control (MAC) enforces strict security policies by restricting user access based on predefined regulations from a central authority, enhancing protection in highly sensitive environments. Discretionary Access Control (DAC) allows resource owners to determine access permissions, providing flexible and user-centric security management. MAC emphasizes system-wide policy enforcement for consistency, while DAC prioritizes user discretion and ease of delegation.
Security Strengths: MAC Advantages
Mandatory Access Control (MAC) offers stronger security by enforcing centralized policies that users cannot alter, reducing the risk of unauthorized data access. Its strict access rules based on security labels and classifications prevent privilege escalation and insider threats more effectively than Discretionary Access Control (DAC). MAC's robust enforcement model is ideal for environments requiring high assurance, such as government and military systems.
Flexibility and Usability: DAC Benefits
Discretionary Access Control (DAC) offers high flexibility by allowing users to set permissions on their own resources, enhancing ease of management in dynamic environments. This user-centric control model supports collaborative workflows and rapid changes without requiring strict administrative policies. DAC's usability makes it well-suited for organizations prioritizing adaptability and user empowerment over rigid security frameworks.
Common Use Cases for MAC
Mandatory Access Control (MAC) is predominantly utilized in environments requiring high levels of security, such as military and government organizations, where classified information must be strictly controlled. Its use cases include safeguarding sensitive data with fixed security policies that cannot be altered by end users, ensuring compliance with regulatory standards like HIPAA or PCI-DSS. MAC is also common in critical infrastructure systems, where preventing unauthorized access and enforcing strict access controls is essential to maintain system integrity.
Typical Applications of DAC
Discretionary Access Control (DAC) is commonly used in commercial environments where flexibility and user-driven access management are essential, such as file-sharing systems and collaborative workspaces. It enables resource owners to set permissions based on individual user identities, making it suitable for systems requiring granular control over access rights. DAC's typical applications include operating systems like Windows and Linux, where users grant access to files and applications within their discretion.
Comparing Implementation Challenges
Mandatory Access Control (MAC) presents implementation challenges due to its rigid, system-enforced policies requiring comprehensive classification and labeling of all data objects. Discretionary Access Control (DAC) offers flexibility but creates difficulties in managing user permissions and preventing unauthorized access in dynamic environments. Organizations often face higher administrative overhead with MAC while DAC systems risk inconsistent security enforcement and user errors.
Choosing the Right Model for Your Organization
Mandatory Access Control (MAC) offers heightened security by enforcing strict policies controlled by a central authority, making it ideal for organizations handling sensitive or classified information. Discretionary Access Control (DAC) provides flexible, user-managed permissions suitable for environments where collaboration and ease of access are prioritized. Evaluating your organization's security requirements, regulatory compliance, and operational needs is essential to select the most effective access control model.
MAC vs DAC Infographic
 techiny.com
techiny.com