Macro viruses specifically target applications like word processors and spreadsheets by embedding malicious code within macros, exploiting common software features to spread. File infector viruses attach themselves to executable files, enabling them to activate whenever the infected program runs, often causing system-wide damage. Understanding these differences is crucial for deploying targeted antivirus strategies and enhancing overall cybersecurity defenses.
Table of Comparison
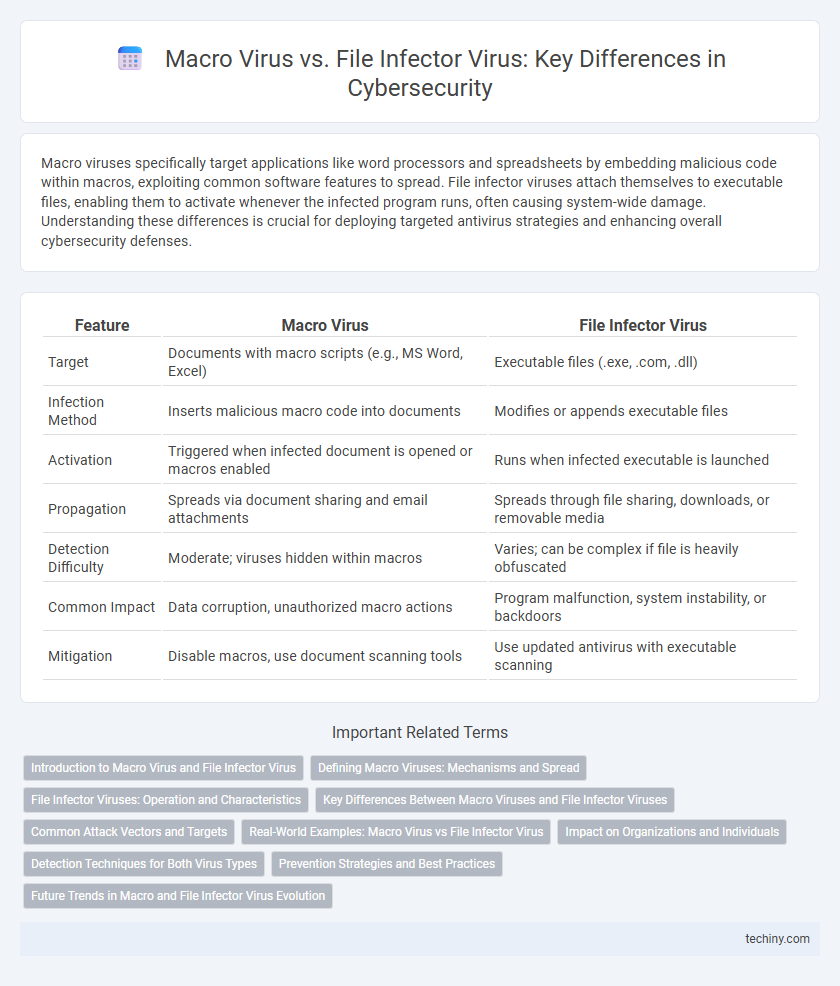
| Feature | Macro Virus | File Infector Virus |
|---|---|---|
| Target | Documents with macro scripts (e.g., MS Word, Excel) | Executable files (.exe, .com, .dll) |
| Infection Method | Inserts malicious macro code into documents | Modifies or appends executable files |
| Activation | Triggered when infected document is opened or macros enabled | Runs when infected executable is launched |
| Propagation | Spreads via document sharing and email attachments | Spreads through file sharing, downloads, or removable media |
| Detection Difficulty | Moderate; viruses hidden within macros | Varies; can be complex if file is heavily obfuscated |
| Common Impact | Data corruption, unauthorized macro actions | Program malfunction, system instability, or backdoors |
| Mitigation | Disable macros, use document scanning tools | Use updated antivirus with executable scanning |
Introduction to Macro Virus and File Infector Virus
Macro viruses target document files created by applications like Microsoft Word and Excel, embedding malicious code in macros that execute automatically when the document opens. File infector viruses attach themselves to executable files such as .exe or .com, infecting programs by inserting harmful code that runs alongside the host file. Both types of viruses compromise system security by exploiting different file vulnerabilities, with macro viruses leveraging application-specific scripts and file infectors attacking system executables.
Defining Macro Viruses: Mechanisms and Spread
Macro viruses exploit embedded scripting languages in applications like Microsoft Word and Excel, enabling them to automate malicious tasks within documents. These viruses propagate by attaching themselves to macro-enabled files and activate when users open or edit infected documents, facilitating rapid spread through file sharing and email attachments. Unlike traditional file infector viruses, macro viruses target the application layer rather than system executables, leveraging user interaction to execute harmful macros.
File Infector Viruses: Operation and Characteristics
File infector viruses operate by attaching themselves to executable files, such as .exe or .com files, and activate when the infected file runs, allowing them to replicate and spread across systems. They modify host files by injecting malicious code, often increasing file size or altering file behavior, which complicates detection by antivirus software. These viruses exhibit persistence by embedding in system files or boot sectors, enabling them to survive system reboots and execution of infected programs.
Key Differences Between Macro Viruses and File Infector Viruses
Macro viruses specifically target documents and templates by embedding malicious code within macros in software like Microsoft Word or Excel, exploiting the macro scripting environment. File infector viruses attach themselves to executable files, modifying or replacing these files to spread and execute harmful code when programs run. The primary distinction is the infection vector: macro viruses rely on document macros, while file infector viruses directly compromise executable files.
Common Attack Vectors and Targets
Macro viruses primarily exploit vulnerabilities in document-based applications like Microsoft Word and Excel by embedding malicious code within macros, targeting office files to execute unauthorized actions when opened. File infector viruses attach themselves to executable files (.exe, .com) and spread through software installations, focusing on system files and applications to disrupt normal operations. Both viruses commonly propagate via email attachments, infected downloads, and removable media, exploiting human interaction and weak security controls to infiltrate systems.
Real-World Examples: Macro Virus vs File Infector Virus
Macro viruses like Melissa and ILOVEYOU exploited Microsoft Office macros to spread rapidly through email attachments, causing massive data loss and network disruption in the late 1990s and early 2000s. File infector viruses such as the CIH (Chernobyl) virus and the Cascade virus targeted executable files, corrupting programs and sometimes causing hardware damage by overwriting BIOS data. Understanding these real-world examples highlights the distinct attack vectors and impacts of macro viruses versus file infectors in cybersecurity defense strategies.
Impact on Organizations and Individuals
Macro viruses primarily target documents and office files, potentially causing widespread disruption by corrupting critical business data and enabling unauthorized access to sensitive information, posing significant risks to both organizations and individuals. File infector viruses attach to executable files, leading to system instability, data loss, and impaired operational efficiency, which can result in costly downtime and compromised personal data security. Both types of viruses demand robust cybersecurity measures to prevent financial damage, reputational harm, and the breach of confidential information.
Detection Techniques for Both Virus Types
Detection techniques for macro viruses often rely on pattern recognition within document macros and heuristic analysis to identify suspicious code sequences embedded in applications like Microsoft Word or Excel. File infector viruses are typically detected through signature-based scanning, monitoring changes to executable files, and integrity verification methods that track unexpected file modifications. Behavioral analysis tools complement these techniques by observing unusual system activities triggered by both virus types, enhancing early detection and response.
Prevention Strategies and Best Practices
Macro viruses exploit vulnerabilities in office documents, making regular software updates and cautious handling of email attachments crucial for prevention. File infector viruses attach themselves to executable files, necessitating robust antivirus solutions and restricting unauthorized software installations. Adopting comprehensive endpoint protection and continuous user awareness training effectively mitigates risks posed by both virus types.
Future Trends in Macro and File Infector Virus Evolution
Emerging trends in macro and file infector viruses highlight increasing sophistication in evasion techniques and encryption methods, making detection more challenging for traditional antivirus solutions. Advances in AI-driven malware enable adaptive behaviors that customize attacks based on target environments, increasing the risk of widespread breaches. Future cybersecurity strategies must integrate machine learning analytics and behavioral detection models to counteract these evolving threats effectively.
Macro Virus vs File Infector Virus Infographic
 techiny.com
techiny.com