Penetration testing simulates real-world cyberattacks to identify security weaknesses by exploiting vulnerabilities, providing a thorough evaluation of an organization's defense mechanisms. Vulnerability assessment systematically scans and identifies potential security flaws without actively exploiting them, offering a broader view of risks and prioritizing remediation efforts. Combining both approaches strengthens overall cybersecurity by detecting risks and validating the effectiveness of security controls.
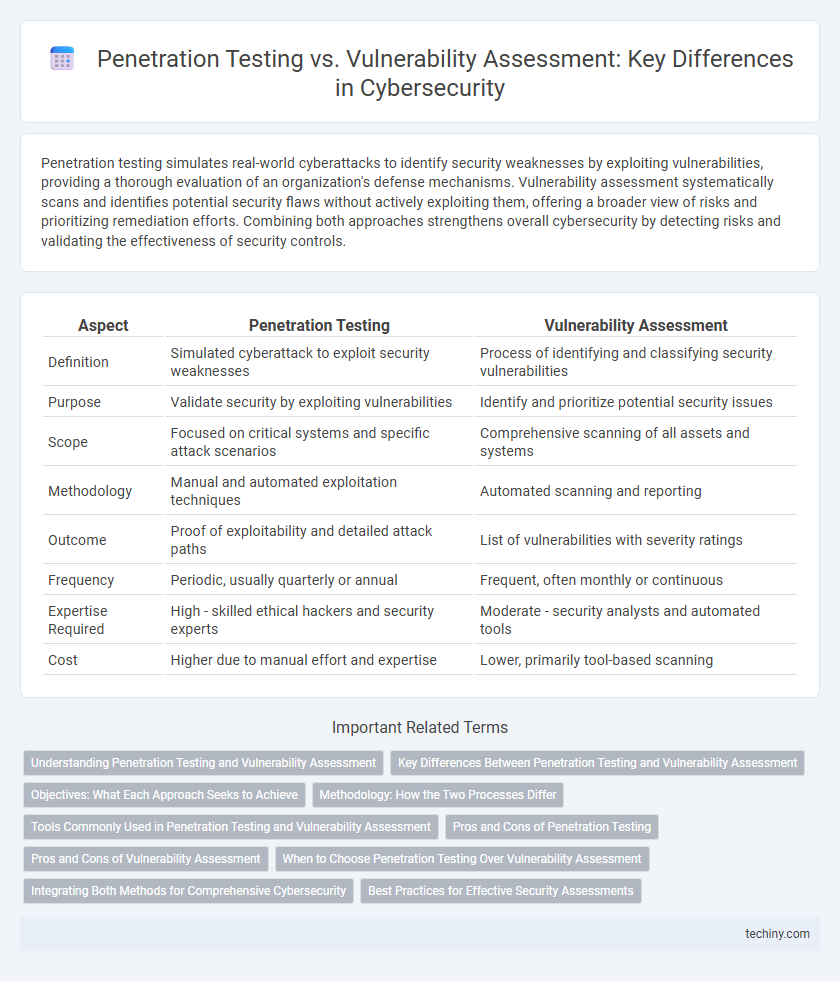
Table of Comparison
| Aspect | Penetration Testing | Vulnerability Assessment |
|---|---|---|
| Definition | Simulated cyberattack to exploit security weaknesses | Process of identifying and classifying security vulnerabilities |
| Purpose | Validate security by exploiting vulnerabilities | Identify and prioritize potential security issues |
| Scope | Focused on critical systems and specific attack scenarios | Comprehensive scanning of all assets and systems |
| Methodology | Manual and automated exploitation techniques | Automated scanning and reporting |
| Outcome | Proof of exploitability and detailed attack paths | List of vulnerabilities with severity ratings |
| Frequency | Periodic, usually quarterly or annual | Frequent, often monthly or continuous |
| Expertise Required | High - skilled ethical hackers and security experts | Moderate - security analysts and automated tools |
| Cost | Higher due to manual effort and expertise | Lower, primarily tool-based scanning |
Understanding Penetration Testing and Vulnerability Assessment
Penetration testing involves simulating real-world cyberattacks to exploit vulnerabilities in a system, providing insight into security weaknesses and their potential impact. Vulnerability assessment systematically scans and identifies security flaws without exploiting them, offering a comprehensive inventory of risks. Both methods are essential for a robust cybersecurity strategy, with penetration testing emphasizing attack simulation and vulnerability assessment focusing on risk identification.
Key Differences Between Penetration Testing and Vulnerability Assessment
Penetration testing simulates real-world cyberattacks to exploit vulnerabilities and assess the effectiveness of security defenses, while vulnerability assessment identifies and categorizes potential vulnerabilities without actively exploiting them. Penetration tests provide insights into the actual impact and risk associated with vulnerabilities, offering a deeper understanding of system weaknesses compared to vulnerability assessments that deliver comprehensive vulnerability inventories. The scope, methodology, and outcome focus distinguish penetration testing as a hands-on attack simulation and vulnerability assessment as a broad security posture evaluation.
Objectives: What Each Approach Seeks to Achieve
Penetration Testing aims to identify and exploit security weaknesses by simulating real-world cyberattacks, providing a practical evaluation of an organization's defense capabilities. Vulnerability Assessment focuses on systematically scanning and cataloging potential security flaws without exploitation, prioritizing identification and risk management. Both approaches target improving security posture but differ in scope and depth: penetration testing validates exploitability, while vulnerability assessment ensures comprehensive detection.
Methodology: How the Two Processes Differ
Penetration testing involves simulated real-world attacks to exploit vulnerabilities and assess the impact on system security, providing a hands-on evaluation of threat exposure. Vulnerability assessment systematically scans and identifies security weaknesses through automated tools without actively exploiting them, focusing on risk detection and prioritization. The methodology difference lies in penetration testing's active exploitation approach versus vulnerability assessment's passive vulnerability identification.
Tools Commonly Used in Penetration Testing and Vulnerability Assessment
Penetration testing commonly employs tools such as Metasploit, Burp Suite, and Nmap to simulate real-world attacks and identify exploitable security weaknesses. Vulnerability assessments often utilize scanners like Nessus, OpenVAS, and Qualys that focus on detecting and reporting potential vulnerabilities without exploiting them. Both methodologies rely on automated and manual tools to enhance an organization's security posture by identifying risks from different angles.
Pros and Cons of Penetration Testing
Penetration testing offers a thorough evaluation of security by simulating real-world attacks, identifying exploitable vulnerabilities and providing actionable insights for remediation. However, it can be costly, time-consuming, and may disrupt normal operations, requiring skilled testers to avoid false positives or system damage. Despite these drawbacks, penetration testing remains a critical tool for validating defenses beyond automated vulnerability assessments.
Pros and Cons of Vulnerability Assessment
Vulnerability assessment identifies and categorizes security weaknesses in systems, providing a broad overview of potential risks without exploiting them, which allows organizations to prioritize remediation efforts efficiently. It is less intrusive and requires fewer resources compared to penetration testing but may miss complex attack vectors that only hands-on exploitation can reveal. Although cost-effective and quick for regular audits, vulnerability assessments sometimes generate false positives and lack the in-depth analysis needed to fully understand the exploitability of vulnerabilities.
When to Choose Penetration Testing Over Vulnerability Assessment
Penetration testing is ideal when organizations require a real-world simulation of cyberattacks to identify exploitable security weaknesses and assess the effectiveness of existing defenses, especially for critical systems or after major infrastructure changes. It provides deep insights into the potential impact of threats through controlled exploit attempts, unlike vulnerability assessments, which only catalog known vulnerabilities without exploitation. Choose penetration testing when the goal is to understand attack vectors fully and prioritize remediation based on actual risk exposure rather than just vulnerability presence.
Integrating Both Methods for Comprehensive Cybersecurity
Integrating penetration testing and vulnerability assessment creates a robust cybersecurity strategy by combining deep exploitation analysis with broad vulnerability identification. Penetration testing simulates real-world attacks to uncover exploitable security gaps, while vulnerability assessments provide systematic scans to detect potential weaknesses across systems. Utilizing both methods ensures comprehensive security coverage, enabling organizations to prioritize remediation efforts and strengthen defenses against evolving cyber threats.
Best Practices for Effective Security Assessments
Penetration testing simulates real-world attacks to identify exploitable vulnerabilities, while vulnerability assessments provide a comprehensive inventory of security weaknesses without exploitation. Effective security assessments combine both approaches, leveraging vulnerability scans to map risks and penetration tests to validate exploitability, ensuring thorough threat detection. Regularly updating tools, maintaining clear scope definitions, and integrating findings into a continuous security improvement process are key best practices for maximizing assessment accuracy and organizational resilience.
Penetration Testing vs Vulnerability Assessment Infographic
 techiny.com
techiny.com