Penetration testing simulates real-world cyberattacks to identify exploitable security weaknesses, providing a deeper, hands-on analysis of system vulnerabilities. Vulnerability scanning automates the detection of known security flaws across networks and applications, offering a broad but less detailed overview. Combining both methods enhances cybersecurity by addressing vulnerabilities comprehensively and prioritizing remediation efforts effectively.
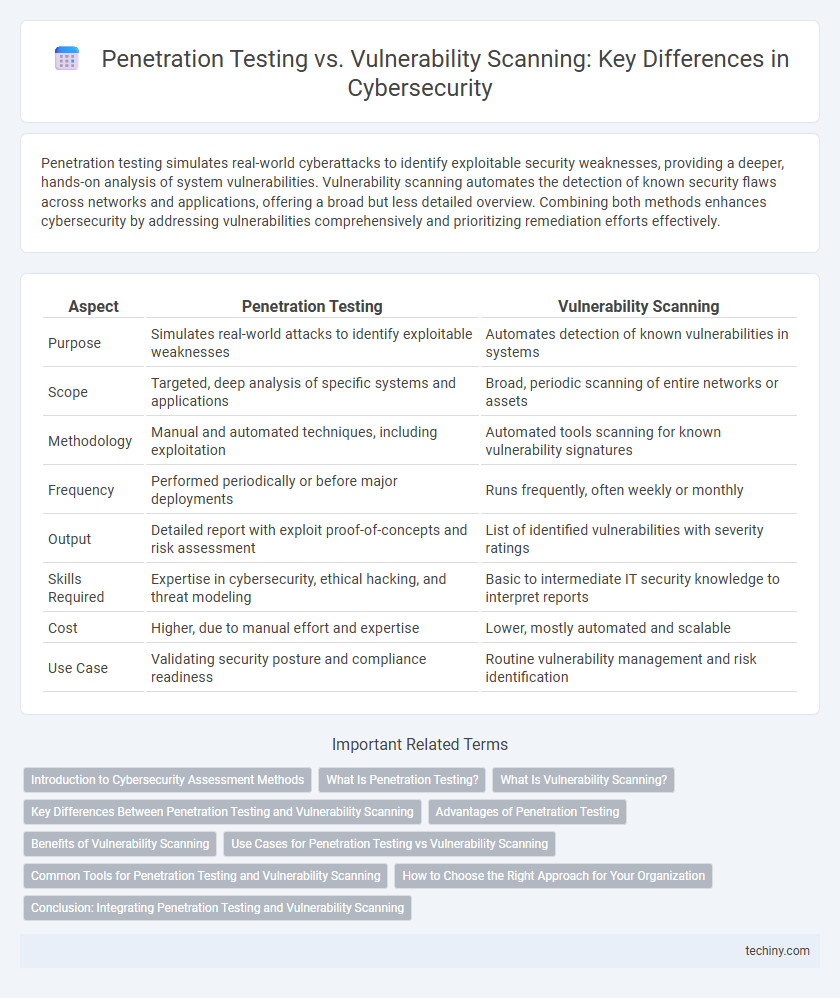
Table of Comparison
| Aspect | Penetration Testing | Vulnerability Scanning |
|---|---|---|
| Purpose | Simulates real-world attacks to identify exploitable weaknesses | Automates detection of known vulnerabilities in systems |
| Scope | Targeted, deep analysis of specific systems and applications | Broad, periodic scanning of entire networks or assets |
| Methodology | Manual and automated techniques, including exploitation | Automated tools scanning for known vulnerability signatures |
| Frequency | Performed periodically or before major deployments | Runs frequently, often weekly or monthly |
| Output | Detailed report with exploit proof-of-concepts and risk assessment | List of identified vulnerabilities with severity ratings |
| Skills Required | Expertise in cybersecurity, ethical hacking, and threat modeling | Basic to intermediate IT security knowledge to interpret reports |
| Cost | Higher, due to manual effort and expertise | Lower, mostly automated and scalable |
| Use Case | Validating security posture and compliance readiness | Routine vulnerability management and risk identification |
Introduction to Cybersecurity Assessment Methods
Penetration testing simulates real-world cyberattacks to identify exploitable security weaknesses by actively exploiting vulnerabilities in systems, networks, or applications. Vulnerability scanning uses automated tools to detect known security flaws and misconfigurations without exploiting them, providing a comprehensive inventory of potential risks. Both methods are essential in cybersecurity assessment strategies, offering complementary insights to strengthen organizational defenses.
What Is Penetration Testing?
Penetration testing is a simulated cyberattack authorized to evaluate the security of an IT system by identifying and exploiting vulnerabilities in applications, networks, or devices. This proactive approach provides in-depth insight into the potential impact of real-world threats by mimicking hacker techniques to uncover security weaknesses. Unlike automated vulnerability scanning, penetration testing involves manual, expert-driven analysis to deliver comprehensive risk assessments and actionable remediation strategies.
What Is Vulnerability Scanning?
Vulnerability scanning is an automated process that identifies security weaknesses in computer systems, networks, and applications by comparing them against a database of known vulnerabilities. This method provides a broad overview of potential risks, allowing organizations to prioritize remediation efforts before attackers exploit these weaknesses. Unlike penetration testing, vulnerability scanning does not simulate real-world attacks but offers continuous monitoring to detect emerging threats and configuration issues.
Key Differences Between Penetration Testing and Vulnerability Scanning
Penetration testing involves simulating real-world cyberattacks to identify exploitable security weaknesses, providing a detailed assessment of an organization's security posture. Vulnerability scanning uses automated tools to detect known vulnerabilities and configuration issues across systems, delivering a broad inventory of potential risks. The key difference lies in penetration testing's manual, exploit-focused approach versus vulnerability scanning's automated, surface-level detection, resulting in varying depth and precision of security insights.
Advantages of Penetration Testing
Penetration testing offers a comprehensive evaluation by simulating real-world cyberattacks to identify exploitable vulnerabilities within an organization's network, applications, and systems. It provides detailed insights into security gaps, assesses the effectiveness of existing defensive measures, and helps prioritize remediation efforts based on actual attack scenarios. Unlike automated vulnerability scanning, penetration testing delivers actionable intelligence through manual techniques, uncovering complex vulnerabilities that scanners often miss.
Benefits of Vulnerability Scanning
Vulnerability scanning provides automated, continuous monitoring to identify security weaknesses across networks, systems, and applications, enabling organizations to maintain an up-to-date security posture. It efficiently detects known vulnerabilities, misconfigurations, and compliance issues, reducing the risk of exploitation by cyber attackers. Regular vulnerability scans support proactive security management by prioritizing risks and facilitating timely remediation efforts.
Use Cases for Penetration Testing vs Vulnerability Scanning
Penetration testing is essential for simulating real-world cyberattacks to identify exploit vulnerabilities in complex and high-risk environments, making it ideal for assessing business-critical systems and compliance requirements. Vulnerability scanning is best suited for routine, automated identification of known security weaknesses across large networks, enabling continuous monitoring and rapid patch management. Organizations leverage penetration testing for detailed security posture validation and vulnerability scanning for broad-spectrum risk assessment and asset management.
Common Tools for Penetration Testing and Vulnerability Scanning
Common tools for penetration testing include Metasploit, Burp Suite, and Kali Linux, which allow security professionals to simulate real-world attacks and identify exploitable vulnerabilities. Vulnerability scanning relies heavily on automated solutions such as Nessus, OpenVAS, and Qualys, designed to quickly detect known security weaknesses across systems and networks. Both tool types complement each other by combining in-depth exploit testing with broad vulnerability identification for comprehensive cybersecurity assessment.
How to Choose the Right Approach for Your Organization
Penetration testing provides a comprehensive, hands-on assessment by simulating real-world cyberattacks to identify exploitable vulnerabilities, making it ideal for organizations requiring in-depth security analysis. Vulnerability scanning offers automated, broad-spectrum detection of known weaknesses, suitable for frequent assessments and compliance monitoring. Selecting the right approach depends on factors such as the organization's risk tolerance, regulatory requirements, budget constraints, and the desired depth of security insights.
Conclusion: Integrating Penetration Testing and Vulnerability Scanning
Integrating penetration testing and vulnerability scanning creates a robust cybersecurity strategy by combining automated vulnerability identification with in-depth manual exploitation analysis. This synergy enhances threat detection accuracy, prioritizes remediation efforts, and strengthens overall network defense. Organizations adopting both methodologies can effectively reduce security risks and improve resilience against sophisticated cyberattacks.
Penetration Testing vs Vulnerability Scanning Infographic
 techiny.com
techiny.com