Red Teaming simulates real-world attacks to identify vulnerabilities and test an organization's defenses from an adversary's perspective. Blue Teaming focuses on defending networks by detecting, responding to, and mitigating threats to maintain security and resilience. Together, these approaches enhance an organization's overall cybersecurity posture through continuous testing and improvement.
Table of Comparison
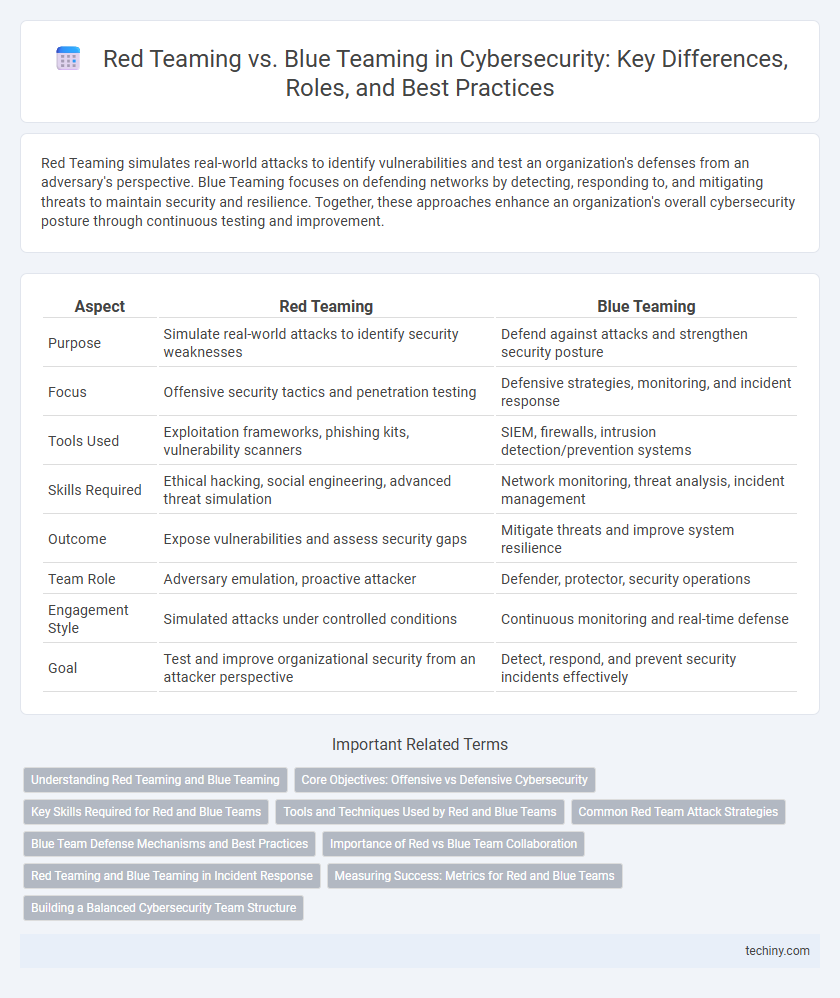
| Aspect | Red Teaming | Blue Teaming |
|---|---|---|
| Purpose | Simulate real-world attacks to identify security weaknesses | Defend against attacks and strengthen security posture |
| Focus | Offensive security tactics and penetration testing | Defensive strategies, monitoring, and incident response |
| Tools Used | Exploitation frameworks, phishing kits, vulnerability scanners | SIEM, firewalls, intrusion detection/prevention systems |
| Skills Required | Ethical hacking, social engineering, advanced threat simulation | Network monitoring, threat analysis, incident management |
| Outcome | Expose vulnerabilities and assess security gaps | Mitigate threats and improve system resilience |
| Team Role | Adversary emulation, proactive attacker | Defender, protector, security operations |
| Engagement Style | Simulated attacks under controlled conditions | Continuous monitoring and real-time defense |
| Goal | Test and improve organizational security from an attacker perspective | Detect, respond, and prevent security incidents effectively |
Understanding Red Teaming and Blue Teaming
Red Teaming involves simulated cyberattacks designed to identify vulnerabilities and test an organization's defense mechanisms by mimicking real-world adversaries. Blue Teaming focuses on defending against such attacks through continuous monitoring, threat detection, and incident response to strengthen security posture. Understanding the roles and techniques of both teams is crucial for developing comprehensive cybersecurity strategies that enhance resilience against evolving cyber threats.
Core Objectives: Offensive vs Defensive Cybersecurity
Red Teaming centers on offensive cybersecurity by simulating real-world cyber attacks to identify vulnerabilities and weaknesses within an organization's infrastructure. Blue Teaming focuses on defensive measures, continuously monitoring, detecting, and responding to threats to protect systems and data. Together, these teams enhance cybersecurity resilience by balancing proactive attack simulations with robust defense strategies.
Key Skills Required for Red and Blue Teams
Red Teaming requires expertise in ethical hacking, penetration testing, social engineering, and threat simulation to identify vulnerabilities before attackers exploit them. Blue Teaming focuses on skills in incident detection, network defense, log analysis, and real-time threat response to safeguard organizational assets. Both teams need a strong understanding of cybersecurity frameworks, malware analysis, and continuous learning to stay ahead of evolving cyber threats.
Tools and Techniques Used by Red and Blue Teams
Red teams employ advanced penetration testing tools such as Metasploit, Cobalt Strike, and custom exploit frameworks to simulate real-world cyberattacks and identify system vulnerabilities. Blue teams utilize security information and event management (SIEM) systems, intrusion detection systems (IDS), endpoint detection and response (EDR) tools, and network traffic analysis to monitor, detect, and respond to threats in real time. Red team techniques focus on social engineering, vulnerability exploitation, and lateral movement, while blue teams emphasize threat hunting, incident response, and continuous security monitoring to strengthen defenses.
Common Red Team Attack Strategies
Red Team attack strategies typically include spear phishing to gain initial access, exploiting vulnerabilities through social engineering and zero-day exploits, and simulating insider threats to test organizational resilience. They often use advanced persistent threats (APTs) to maintain stealthy access over time, leveraging lateral movement techniques to explore network architecture and extract sensitive data. These tactics aim to identify security gaps and improve Blue Team defenses by mimicking real-world cyber attack scenarios.
Blue Team Defense Mechanisms and Best Practices
Blue Team defense mechanisms focus on proactive threat detection, incident response, and continuous system monitoring to safeguard organizational assets. Best practices include deploying advanced intrusion detection systems (IDS), implementing multi-factor authentication (MFA), maintaining up-to-date security patches, and conducting regular vulnerability assessments. Effective Blue Team operations also emphasize comprehensive log analysis, network segmentation, and employee cybersecurity training to minimize attack surfaces and rapidly mitigate threats.
Importance of Red vs Blue Team Collaboration
Effective cybersecurity relies on the collaborative efforts of Red and Blue Teams, where Red Teams simulate real-world attacks to identify vulnerabilities, and Blue Teams defend by strengthening security measures. Their collaboration enhances threat detection and response capabilities, bridging the gap between offensive tactics and defensive strategies. Continuous interaction ensures a proactive security posture, reducing the risk of breaches and improving organizational resilience.
Red Teaming and Blue Teaming in Incident Response
Red Teaming simulates sophisticated cyberattacks to expose vulnerabilities in an organization's defenses, providing critical insights that enhance incident response strategies. Blue Teaming specializes in real-time threat detection, mitigation, and recovery, ensuring continuous monitoring and rapid response to security incidents. Together, both teams create a dynamic, proactive cybersecurity posture by identifying weaknesses and strengthening defense mechanisms during incident response.
Measuring Success: Metrics for Red and Blue Teams
Measuring success for Red Teams involves tracking metrics such as the number of vulnerabilities discovered, time to breach, and exploitation effectiveness to evaluate the realism and impact of simulated attacks. Blue Teams focus on detection rates, incident response times, and the reduction of false positives to gauge their capability to identify, contain, and mitigate threats in real time. Combining these metrics enables organizations to strengthen overall cybersecurity posture through continuous improvement in both offensive and defensive strategies.
Building a Balanced Cybersecurity Team Structure
Building a balanced cybersecurity team structure involves integrating Red Teaming and Blue Teaming to enhance organizational defense mechanisms. Red Teams simulate real-world attacks to identify vulnerabilities, while Blue Teams focus on monitoring, detecting, and responding to threats in real-time. Combining these proactive offensive and defensive strategies ensures comprehensive risk assessment and strengthens overall security posture.
Red Teaming vs Blue Teaming Infographic
 techiny.com
techiny.com