Sandboxing isolates suspicious files or programs in a controlled environment to analyze their behavior without risking system integrity, while honeypots serve as decoy systems designed to attract and detect attackers by mimicking real network targets. Sandboxing helps prevent malware from executing harmful actions, whereas honeypots gather intelligence on attack methods and threat actors. Both techniques enhance cybersecurity by enabling proactive threat detection and analysis but serve distinct purposes in defense strategies.
Table of Comparison
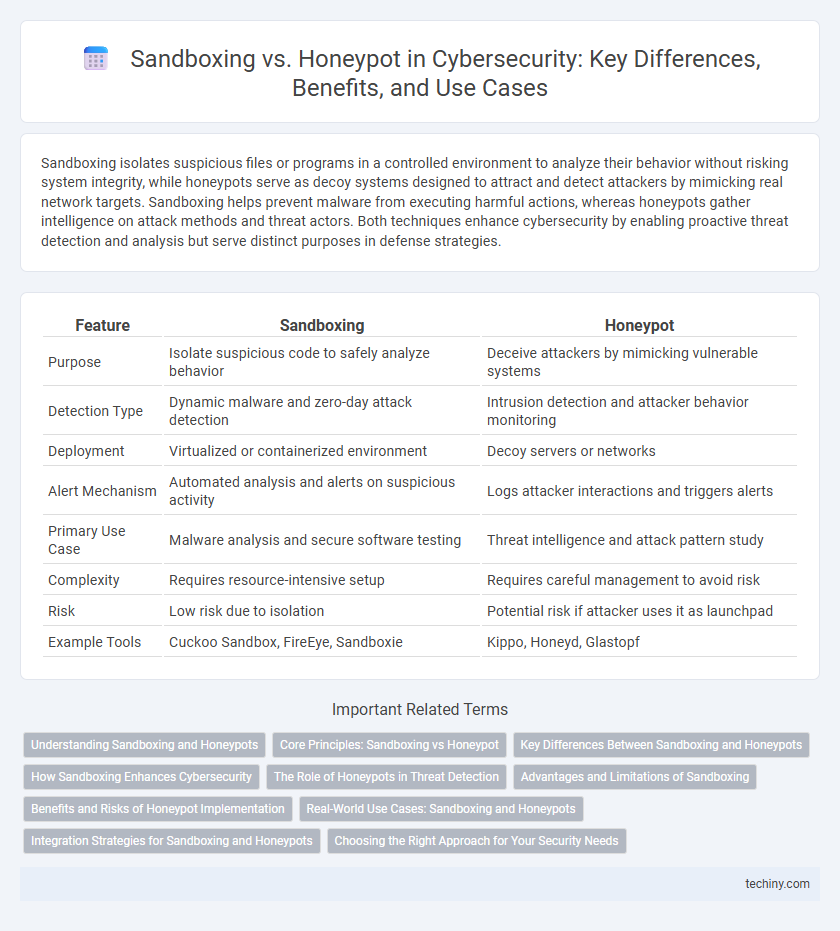
| Feature | Sandboxing | Honeypot |
|---|---|---|
| Purpose | Isolate suspicious code to safely analyze behavior | Deceive attackers by mimicking vulnerable systems |
| Detection Type | Dynamic malware and zero-day attack detection | Intrusion detection and attacker behavior monitoring |
| Deployment | Virtualized or containerized environment | Decoy servers or networks |
| Alert Mechanism | Automated analysis and alerts on suspicious activity | Logs attacker interactions and triggers alerts |
| Primary Use Case | Malware analysis and secure software testing | Threat intelligence and attack pattern study |
| Complexity | Requires resource-intensive setup | Requires careful management to avoid risk |
| Risk | Low risk due to isolation | Potential risk if attacker uses it as launchpad |
| Example Tools | Cuckoo Sandbox, FireEye, Sandboxie | Kippo, Honeyd, Glastopf |
Understanding Sandboxing and Honeypots
Sandboxing isolates suspicious files or programs within a secure environment to analyze their behavior without risking harm to the main system. Honeypots are decoy systems designed to attract attackers and gather intelligence on intrusion methods by simulating real targets. Both techniques enhance cybersecurity defenses by enabling threat detection, analysis, and mitigation through controlled interaction with potential threats.
Core Principles: Sandboxing vs Honeypot
Sandboxing isolates untrusted code or applications in a controlled environment to prevent malicious activity from affecting the host system, using virtualization or containerization technologies. Honeypots simulate vulnerable systems or services to attract and analyze attackers, collecting intelligence on threat behaviors and attack vectors. Both approaches enhance cybersecurity by containing threats and providing actionable insights, with sandboxing focused on prevention and honeypots on detection and deception.
Key Differences Between Sandboxing and Honeypots
Sandboxing isolates suspicious files or applications in a controlled environment to analyze behavior safely, preventing potential threats from affecting the main system. Honeypots act as decoy systems designed to attract and detect attackers, gathering intelligence on attack methods and behavior. Key differences include their primary purpose--sandboxing focuses on threat analysis and containment, while honeypots emphasize deception and attacker monitoring.
How Sandboxing Enhances Cybersecurity
Sandboxing enhances cybersecurity by isolating suspicious files or programs in a controlled virtual environment, preventing malware from affecting the main system. It allows security analysts to safely observe the behavior of unknown threats without risking network integrity. This proactive defense mechanism reduces the risk of zero-day attacks and improves malware detection accuracy.
The Role of Honeypots in Threat Detection
Honeypots play a critical role in threat detection by acting as decoy systems designed to lure cyberattackers, enabling security teams to monitor malicious activities in real-time without risking actual assets. Unlike sandboxing, which isolates suspicious files for analysis, honeypots provide valuable intelligence on attacker techniques, tactics, and procedures (TTPs) by capturing interaction data within a controlled environment. This proactive approach enhances threat detection capabilities by identifying emerging threats and zero-day exploits through continuous observation of attacker behavior.
Advantages and Limitations of Sandboxing
Sandboxing offers a secure environment to analyze suspicious files or code without risking system integrity, effectively isolating threats and preventing malware execution on the host system. Its primary advantages include real-time behavior monitoring, compatibility with various file types, and automated threat detection, enabling early identification of zero-day exploits. However, limitations arise from resource intensiveness, the inability to fully simulate all environmental interactions, and evasion techniques used by sophisticated malware that detect and bypass sandbox environments.
Benefits and Risks of Honeypot Implementation
Honeypots provide cybersecurity benefits by simulating vulnerable systems to attract attackers, enabling detailed analysis of attack methods and early threat detection, which enhances overall network defense strategies. However, risks include the potential for honeypots to be discovered and exploited by attackers for launching further attacks, as well as the resource-intensive nature of maintaining and monitoring these systems. Effective deployment requires careful isolation and continuous monitoring to mitigate exposure to real network assets while maximizing intelligence-gathering capabilities.
Real-World Use Cases: Sandboxing and Honeypots
Sandboxing is extensively used in malware analysis and secure application testing, isolating suspicious files in a controlled environment to detect malicious behavior without risk to production systems. Honeypots serve as decoy systems designed to attract, detect, and analyze attackers by mimicking vulnerable targets, providing valuable intelligence on attacker tactics and threat patterns. Organizations deploy sandboxing to prevent zero-day exploits in software development, while honeypots are integral in identifying advanced persistent threats and enhancing network defense strategies.
Integration Strategies for Sandboxing and Honeypots
Integration strategies for sandboxing and honeypots in cybersecurity involve deploying sandbox environments to analyze suspicious files and behaviors in isolation, while honeypots attract and monitor attacker activities to gather threat intelligence. Combining sandboxing with honeypots enhances detection capabilities by correlating behavioral data from sandboxed malware executions with real-world attacker interactions captured by honeypots. Effective integration requires centralized management platforms that enable seamless data sharing, real-time alerting, and adaptive response mechanisms across both systems to improve threat analysis and incident response.
Choosing the Right Approach for Your Security Needs
Sandboxing offers a controlled environment to safely analyze suspicious files and code by isolating them from the main system, making it ideal for detecting zero-day threats and preventing malware execution. Honeypots serve as decoy systems designed to attract and study attacker behavior, providing valuable intelligence on intrusion methods and attack patterns. Selecting between sandboxing and honeypots depends on whether the priority is real-time threat containment or in-depth attacker analysis to enhance overall cybersecurity defenses.
Sandboxing vs Honeypot Infographic
 techiny.com
techiny.com