A security audit is a formal, systematic evaluation of an organization's security policies, controls, and compliance with regulatory standards, often involving detailed checklists and documentation reviews. In contrast, a security assessment is a broader, more flexible process that identifies vulnerabilities and risks within an IT environment through vulnerability scans, penetration testing, and risk analysis. Understanding the differences helps organizations choose the appropriate approach to strengthen their cybersecurity posture effectively.
Table of Comparison
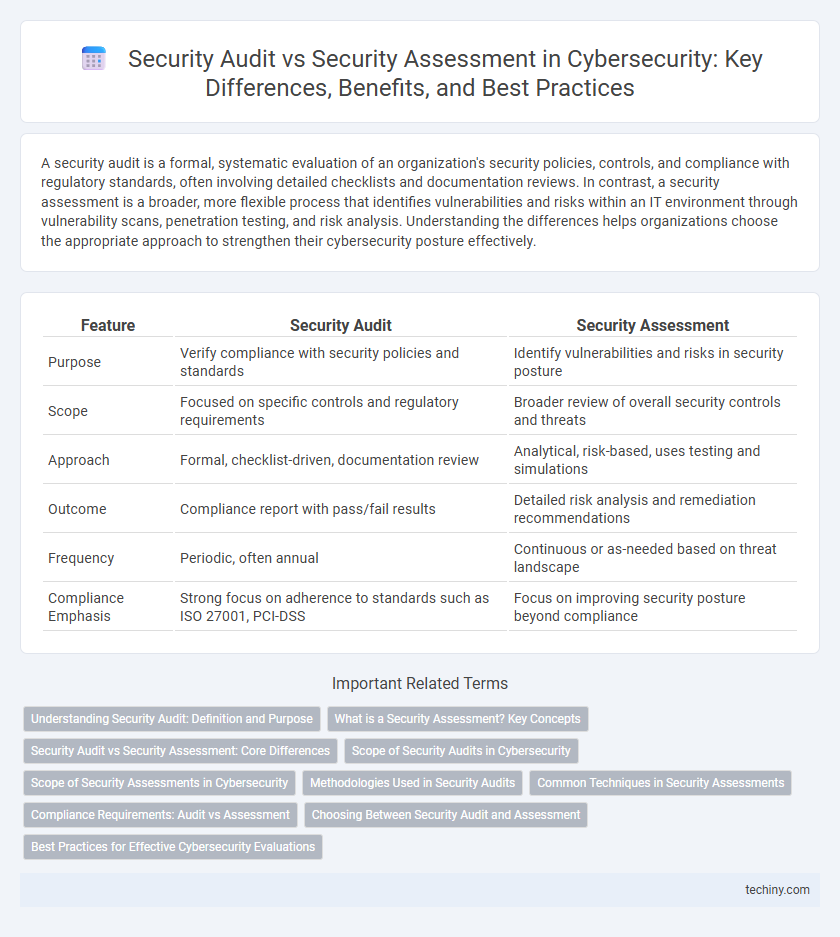
| Feature | Security Audit | Security Assessment |
|---|---|---|
| Purpose | Verify compliance with security policies and standards | Identify vulnerabilities and risks in security posture |
| Scope | Focused on specific controls and regulatory requirements | Broader review of overall security controls and threats |
| Approach | Formal, checklist-driven, documentation review | Analytical, risk-based, uses testing and simulations |
| Outcome | Compliance report with pass/fail results | Detailed risk analysis and remediation recommendations |
| Frequency | Periodic, often annual | Continuous or as-needed based on threat landscape |
| Compliance Emphasis | Strong focus on adherence to standards such as ISO 27001, PCI-DSS | Focus on improving security posture beyond compliance |
Understanding Security Audit: Definition and Purpose
A security audit is a systematic, comprehensive evaluation of an organization's information systems, policies, and controls to ensure compliance with established security standards and regulations. Its primary purpose is to identify vulnerabilities, verify the effectiveness of security measures, and ensure adherence to frameworks such as ISO 27001 or NIST. Unlike broader security assessments, security audits are formal, document-driven processes often mandated by regulatory requirements to validate and enhance cybersecurity posture.
What is a Security Assessment? Key Concepts
A security assessment is a comprehensive evaluation of an organization's cybersecurity posture that identifies vulnerabilities, threats, and risks across systems and networks. It involves systematic analysis using tools such as vulnerability scanners, penetration testing, and compliance checks to measure security controls against established standards like ISO 27001 or NIST. Security assessments aim to provide actionable insights for risk mitigation, improve defense mechanisms, and ensure adherence to regulatory requirements.
Security Audit vs Security Assessment: Core Differences
Security Audit involves a systematic, formal evaluation of an organization's security policies, controls, and compliance with regulatory standards, often conducted by external auditors. Security Assessment is a broader, ongoing process that identifies vulnerabilities, risks, and threats within an IT environment, typically performed internally using various tools and techniques. The core difference lies in the audit's emphasis on compliance and documentation, while assessments focus on proactive risk identification and mitigation strategies.
Scope of Security Audits in Cybersecurity
Security audits in cybersecurity involve a comprehensive evaluation of an organization's adherence to established security policies, regulatory requirements, and industry standards, focusing primarily on verification and compliance. The scope of security audits typically includes detailed examination of access controls, network security configurations, user activities, and documentation accuracy to ensure alignment with security frameworks like ISO 27001, NIST, or HIPAA. Unlike broader security assessments that identify vulnerabilities or risks, security audits emphasize formal validation, systematic testing, and evidence-based reporting to support audit compliance and risk management processes.
Scope of Security Assessments in Cybersecurity
Security assessments in cybersecurity encompass a comprehensive evaluation of an organization's entire security posture, including policies, procedures, technical controls, and compliance requirements, while security audits focus on verifying adherence to specific security standards and regulatory mandates. The scope of security assessments is broader, covering vulnerability identification, risk management, and threat analysis across networks, applications, and endpoints. Effective security assessments provide actionable insights to strengthen defenses and align security objectives with business operations.
Methodologies Used in Security Audits
Security audits primarily use systematic methodologies such as compliance checklists, penetration testing, and vulnerability scanning to evaluate an organization's adherence to established security policies and regulatory standards. These methodologies involve detailed documentation reviews, configuration analyses, and risk assessments to identify gaps in security controls and ensure effective implementation. Security audits emphasize structured, repeatable processes that provide verifiable evidence of compliance and operational security effectiveness.
Common Techniques in Security Assessments
Security assessments commonly employ techniques such as vulnerability scanning, penetration testing, and risk analysis to identify potential threats and weaknesses in an organization's cybersecurity posture. These methods provide a proactive evaluation of system defenses, network infrastructure, and application security to detect vulnerabilities before exploitation. Unlike security audits that primarily review compliance with established standards, security assessments focus on uncovering actionable risks through hands-on testing and scenario-based analysis.
Compliance Requirements: Audit vs Assessment
Security audits rigorously evaluate an organization's adherence to regulatory compliance requirements by systematically reviewing policies, procedures, and controls against defined standards such as ISO 27001, HIPAA, or PCI DSS. Security assessments identify vulnerabilities and risks within systems and processes, providing a broader perspective on potential threats but may not specifically measure compliance against established mandates. While audits prioritize verifying conformity to legal and industry regulations, assessments focus on enhancing overall security posture beyond compliance mandates.
Choosing Between Security Audit and Assessment
Choosing between a security audit and a security assessment depends on organizational goals and compliance requirements. Security audits provide a formal, compliance-focused evaluation against established standards, such as ISO 27001 or NIST, ensuring regulatory adherence and identifying gaps in security controls. Security assessments offer a broader, risk-oriented analysis, helping identify vulnerabilities and recommend improvements beyond compliance, suitable for proactive cybersecurity strategies.
Best Practices for Effective Cybersecurity Evaluations
Security audits involve comprehensive, formal reviews of an organization's compliance with established cybersecurity policies and regulatory standards, while security assessments provide broader evaluations of system vulnerabilities and risk exposures. Best practices for effective cybersecurity evaluations include conducting regular, scheduled audits to ensure ongoing policy adherence, integrating automated tools for thorough vulnerability scanning, and involving cross-functional teams to enhance contextual understanding. Prioritizing detailed documentation and action-oriented reporting accelerates risk mitigation and strengthens overall security posture.
security audit vs security assessment Infographic
 techiny.com
techiny.com