SIEM (Security Information and Event Management) collects and analyzes security data from various sources to detect threats in real-time, providing comprehensive visibility into an organization's security posture. SOAR (Security Orchestration, Automation, and Response) enhances incident response by automating workflows, integrating multiple security tools, and enabling faster mitigation of security incidents. Combining SIEM's threat detection capabilities with SOAR's automated response processes significantly improves operational efficiency and strengthens overall cybersecurity defenses.
Table of Comparison
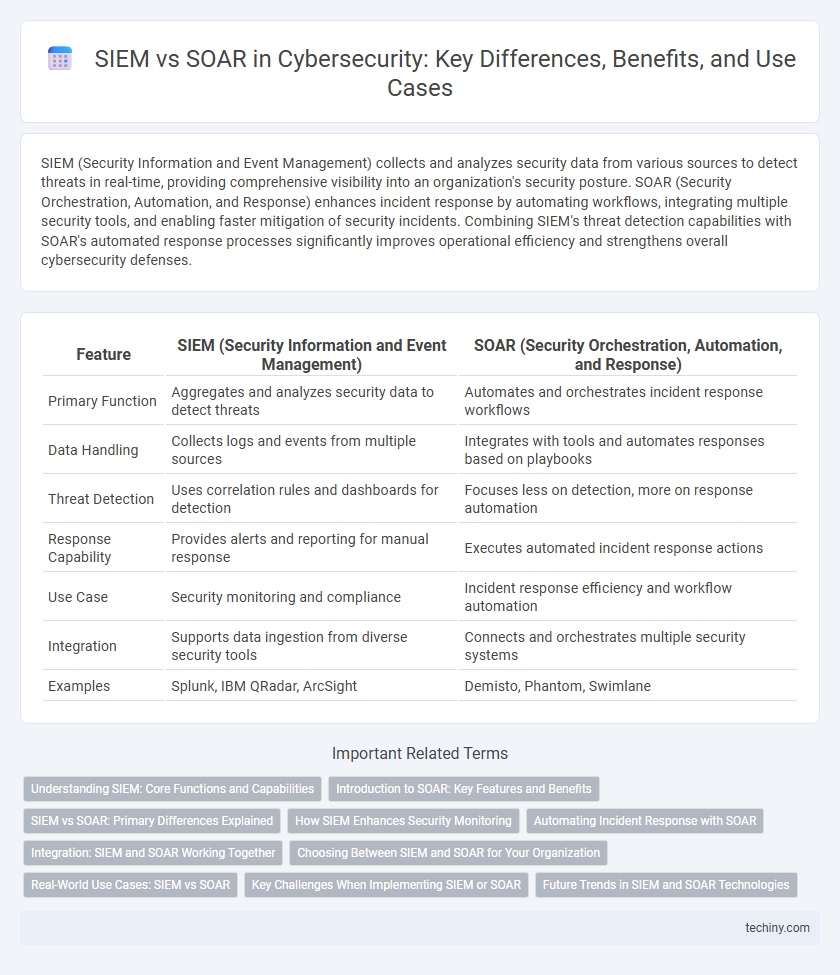
| Feature | SIEM (Security Information and Event Management) | SOAR (Security Orchestration, Automation, and Response) |
|---|---|---|
| Primary Function | Aggregates and analyzes security data to detect threats | Automates and orchestrates incident response workflows |
| Data Handling | Collects logs and events from multiple sources | Integrates with tools and automates responses based on playbooks |
| Threat Detection | Uses correlation rules and dashboards for detection | Focuses less on detection, more on response automation |
| Response Capability | Provides alerts and reporting for manual response | Executes automated incident response actions |
| Use Case | Security monitoring and compliance | Incident response efficiency and workflow automation |
| Integration | Supports data ingestion from diverse security tools | Connects and orchestrates multiple security systems |
| Examples | Splunk, IBM QRadar, ArcSight | Demisto, Phantom, Swimlane |
Understanding SIEM: Core Functions and Capabilities
SIEM (Security Information and Event Management) systems aggregate and analyze security data from diverse sources to identify potential threats and generate actionable alerts. Core functions include real-time event correlation, log management, and compliance reporting, enabling security teams to detect and respond to incidents more effectively. SIEM platforms enhance situational awareness by providing centralized visibility into network activities, user behaviors, and system anomalies.
Introduction to SOAR: Key Features and Benefits
Security Orchestration, Automation, and Response (SOAR) platforms enhance cybersecurity operations by integrating threat intelligence, incident response, and automated workflows into a unified system. Key features include automated playbooks, real-time data correlation, and collaborative case management, enabling faster detection and remediation of cyber threats. SOAR improves efficiency by reducing manual tasks and enhancing response accuracy, significantly lowering the mean time to respond (MTTR) and strengthening overall security posture.
SIEM vs SOAR: Primary Differences Explained
SIEM (Security Information and Event Management) primarily focuses on real-time data collection, correlation, and analysis to detect security threats by aggregating logs from various sources. SOAR (Security Orchestration, Automation, and Response) enhances incident response by automating workflows, integrating multiple security tools, and orchestrating processes to mitigate threats faster. The key difference lies in SIEM's role in threat detection and alert generation versus SOAR's emphasis on response automation and operational efficiency.
How SIEM Enhances Security Monitoring
SIEM (Security Information and Event Management) enhances security monitoring by aggregating and analyzing log data from various sources in real-time to detect suspicious activities and potential threats. It provides comprehensive visibility across the IT infrastructure, enabling security teams to correlate events and prioritize incidents based on severity. By offering automated alerts and detailed forensic data, SIEM improves threat detection accuracy and accelerates incident response efforts.
Automating Incident Response with SOAR
SOAR (Security Orchestration, Automation, and Response) platforms enhance cybersecurity operations by automating incident response processes, reducing manual efforts and accelerating threat mitigation. Unlike SIEM (Security Information and Event Management) systems that primarily focus on data aggregation and analysis, SOAR integrates with SIEM to execute predefined playbooks, enabling real-time responsiveness and consistent incident handling. Automation through SOAR decreases response times, improves operational efficiency, and minimizes human error in complex security environments.
Integration: SIEM and SOAR Working Together
SIEM platforms collect and analyze large volumes of security data to detect threats, while SOAR systems automate incident response and orchestration workflows. Integrating SIEM with SOAR enables seamless data sharing and accelerates threat detection and remediation by combining real-time analytics with automated playbooks. This collaboration enhances overall cybersecurity posture by reducing response times and improving operational efficiency.
Choosing Between SIEM and SOAR for Your Organization
Choosing between SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) depends on your organization's security maturity and operational needs. SIEM excels at real-time log analysis and threat detection by aggregating data from diverse sources, while SOAR enhances incident response efficiency through automation and orchestration of security workflows. Organizations with high alert volumes and the need for rapid, coordinated responses benefit most from integrating SOAR with an existing SIEM platform.
Real-World Use Cases: SIEM vs SOAR
SIEM solutions excel in real-world use cases by providing comprehensive log aggregation, threat detection, and compliance reporting to identify suspicious activities across diverse IT environments. SOAR platforms enhance incident response through automated workflows, threat intelligence integration, and orchestration of security tools, reducing response times and minimizing human error. Organizations often combine SIEM's threat detection capabilities with SOAR's automation to create an effective, scalable security operations center (SOC).
Key Challenges When Implementing SIEM or SOAR
Implementing SIEM or SOAR systems often faces key challenges such as integration complexity with existing IT infrastructure, high volume of false positives causing alert fatigue, and the need for specialized expertise in configuration and tuning. Data overload from multiple sources can hinder effective threat detection, while maintaining up-to-date threat intelligence requires continuous effort and resources. Organizations also struggle with automating incident response workflows in SOAR, balancing automation and manual intervention to avoid disruption.
Future Trends in SIEM and SOAR Technologies
Emerging future trends in SIEM and SOAR technologies include enhanced AI-driven threat detection and automated incident response capabilities, allowing organizations to manage vast amounts of security data with greater precision and speed. Integration of machine learning models and behavioral analytics will improve anomaly detection, reducing false positives and enabling proactive cybersecurity measures. Cloud-native SIEM and SOAR solutions are expected to gain prominence, supporting hybrid environments and scalability to address evolving cyber threats efficiently.
SIEM vs SOAR Infographic
 techiny.com
techiny.com