SOC 1 reports concentrate on the internal controls relevant to financial reporting, ensuring that service organizations protect client financial data accurately and reliably. SOC 2 reports evaluate the effectiveness of controls related to security, availability, processing integrity, confidentiality, and privacy, addressing broader cybersecurity risks beyond financial data. Understanding the distinction between SOC 1 and SOC 2 is crucial for organizations to meet specific compliance requirements and demonstrate their commitment to safeguarding sensitive information.
Table of Comparison
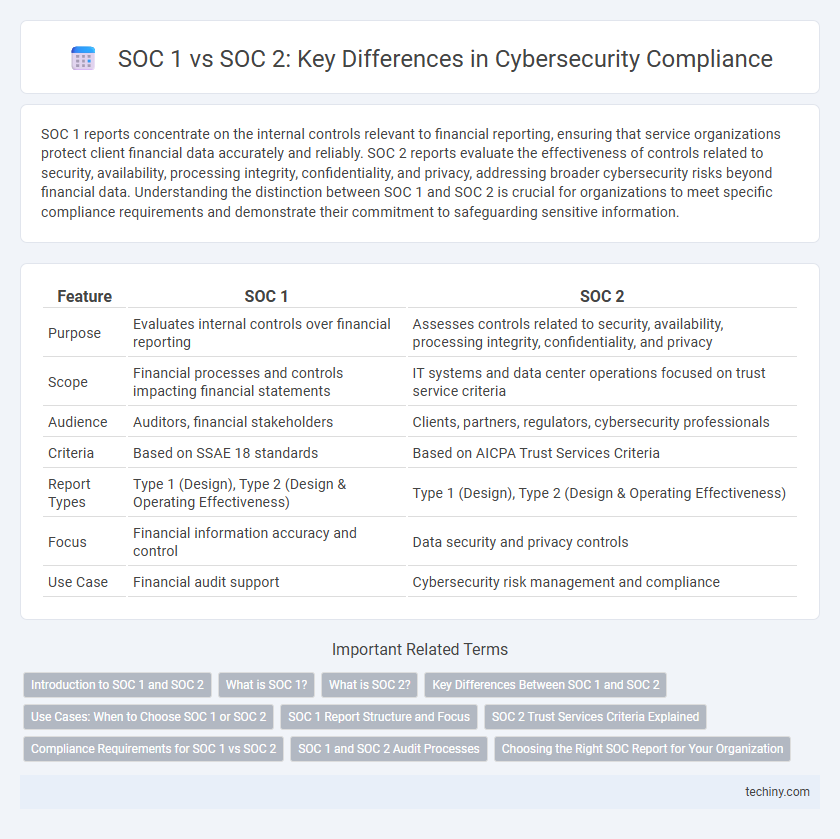
| Feature | SOC 1 | SOC 2 |
|---|---|---|
| Purpose | Evaluates internal controls over financial reporting | Assesses controls related to security, availability, processing integrity, confidentiality, and privacy |
| Scope | Financial processes and controls impacting financial statements | IT systems and data center operations focused on trust service criteria |
| Audience | Auditors, financial stakeholders | Clients, partners, regulators, cybersecurity professionals |
| Criteria | Based on SSAE 18 standards | Based on AICPA Trust Services Criteria |
| Report Types | Type 1 (Design), Type 2 (Design & Operating Effectiveness) | Type 1 (Design), Type 2 (Design & Operating Effectiveness) |
| Focus | Financial information accuracy and control | Data security and privacy controls |
| Use Case | Financial audit support | Cybersecurity risk management and compliance |
Introduction to SOC 1 and SOC 2
SOC 1 reports evaluate the internal controls over financial reporting at a service organization, ensuring compliance with standards relevant to financial data integrity. SOC 2 reports assess controls related to security, availability, processing integrity, confidentiality, and privacy of client data, focusing on operational and compliance risks beyond financial reporting. Organizations select SOC 1 or SOC 2 based on whether their primary concern is financial reporting or broader cybersecurity and data protection requirements.
What is SOC 1?
SOC 1 is a Type 1 or Type 2 report focusing on internal controls over financial reporting (ICFR) for service organizations. It is designed to provide assurance that a service organization's controls are effective in safeguarding client financial data. SOC 1 reports are typically used by auditors and stakeholders involved in financial auditing and compliance.
What is SOC 2?
SOC 2 is a cybersecurity framework designed for service providers to manage and protect customer data based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy. It assesses the effectiveness of an organization's controls in safeguarding data, ensuring systems remain secure and reliable against cyber threats. SOC 2 reports help businesses demonstrate compliance with stringent data protection standards, fostering trust with clients and partners.
Key Differences Between SOC 1 and SOC 2
SOC 1 reports primarily focus on internal controls over financial reporting and are designed for service organizations impacting client financial statements, while SOC 2 audits emphasize controls related to security, availability, processing integrity, confidentiality, and privacy of data. SOC 1 is generally used by organizations where financial data handling is critical, whereas SOC 2 suits technology and cloud service providers aiming to assure clients of their data protection measures. The frameworks differ in scope, with SOC 1 aligned to SSAE 18 standards and SOC 2 based on the Trust Services Criteria established by the AICPA.
Use Cases: When to Choose SOC 1 or SOC 2
SOC 1 reports are essential for organizations that handle financial data and require assurance on internal controls related to financial reporting, such as payroll processors and financial service providers. SOC 2 reports suit technology and cloud computing companies seeking to demonstrate controls over security, availability, processing integrity, confidentiality, and privacy for their customers' data. Choosing SOC 1 or SOC 2 depends on whether the primary concern is financial audit compliance or operational security and data protection requirements.
SOC 1 Report Structure and Focus
SOC 1 reports are primarily designed to assess the internal controls over financial reporting (ICFR) relevant to user entities and their auditors, emphasizing controls that impact financial statements. The report structure includes a detailed description of the service organization's system, management's assertion, auditor's opinion, and test results of control effectiveness. SOC 1 focuses on operational controls related to financial processes, distinguishing it from SOC 2, which centers on trust service criteria such as security, availability, and confidentiality.
SOC 2 Trust Services Criteria Explained
SOC 2 reports are designed to evaluate an organization's controls relevant to the Trust Services Criteria, which include security, availability, processing integrity, confidentiality, and privacy. These criteria provide a comprehensive framework to ensure that service providers manage data securely and maintain systems that protect customer information. SOC 1, in contrast, focuses primarily on financial reporting controls, making SOC 2 the preferred standard for assessing cybersecurity and data protection practices.
Compliance Requirements for SOC 1 vs SOC 2
SOC 1 compliance requirements center on internal controls relevant to financial reporting, ensuring service organizations manage risks impacting clients' financial data accuracy and integrity. SOC 2 compliance emphasizes controls related to security, availability, processing integrity, confidentiality, and privacy of systems, tailored for technology and cloud service providers to meet stringent data protection standards. Organizations pursuing SOC 1 focus on audit and control frameworks under SSAE 18, whereas SOC 2 aligns with Trust Services Criteria to address broader cybersecurity and privacy mandates.
SOC 1 and SOC 2 Audit Processes
SOC 1 audit processes primarily evaluate internal controls relevant to financial reporting within service organizations, emphasizing the accuracy and security of financial data handling. SOC 2 audits focus on controls related to security, availability, processing integrity, confidentiality, and privacy of systems, ensuring data protection and operational reliability. Both audits involve rigorous risk assessment, control testing, and continuous monitoring to validate compliance with established standards and regulatory requirements.
Choosing the Right SOC Report for Your Organization
Choosing the right SOC report depends on your organization's specific compliance and security needs. SOC 1 focuses on financial reporting controls, essential for organizations handling financial data, while SOC 2 emphasizes security, availability, processing integrity, confidentiality, and privacy, making it crucial for service providers prioritizing customer data protection. Evaluating the nature of your services and regulatory requirements ensures you select a SOC report that aligns with your operational risks and client expectations.
SOC 1 vs SOC 2 Infographic
 techiny.com
techiny.com