A Security Operations Center (SOC) primarily focuses on monitoring, detecting, and responding to cybersecurity threats and incidents, ensuring the protection of an organization's digital assets. In contrast, a Network Operations Center (NOC) manages the overall network infrastructure, maintaining optimal performance, uptime, and connectivity. Both centers play crucial roles in IT management but serve distinct functions to safeguard and support enterprise technology environments.
Table of Comparison
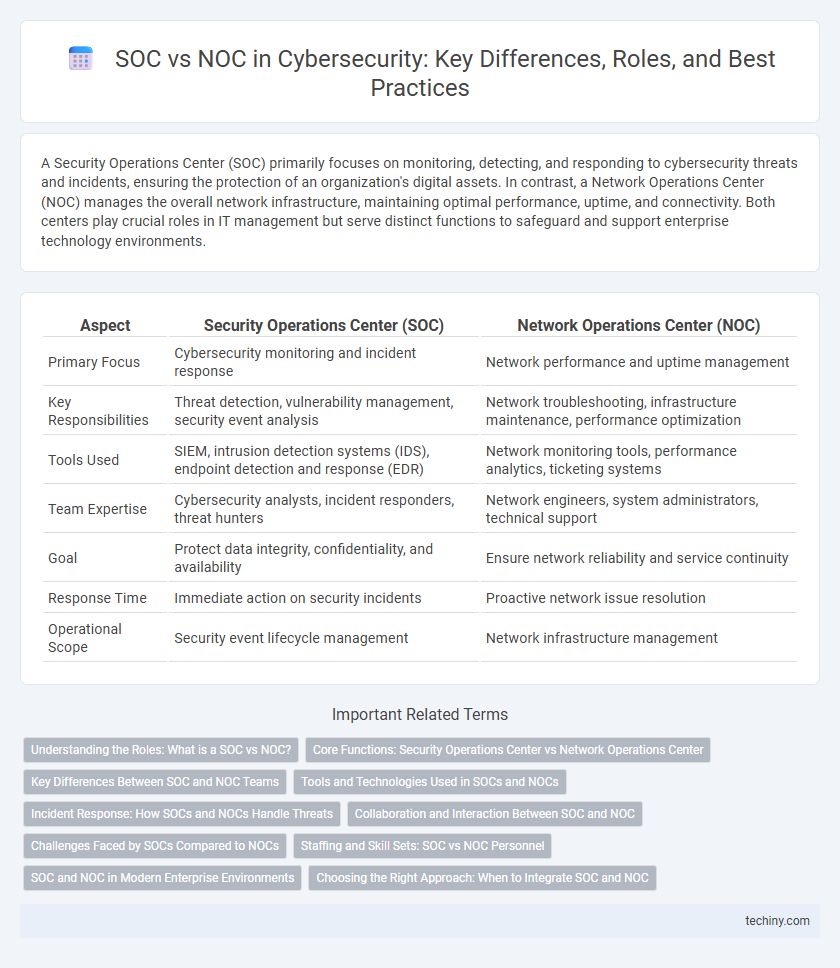
| Aspect | Security Operations Center (SOC) | Network Operations Center (NOC) |
|---|---|---|
| Primary Focus | Cybersecurity monitoring and incident response | Network performance and uptime management |
| Key Responsibilities | Threat detection, vulnerability management, security event analysis | Network troubleshooting, infrastructure maintenance, performance optimization |
| Tools Used | SIEM, intrusion detection systems (IDS), endpoint detection and response (EDR) | Network monitoring tools, performance analytics, ticketing systems |
| Team Expertise | Cybersecurity analysts, incident responders, threat hunters | Network engineers, system administrators, technical support |
| Goal | Protect data integrity, confidentiality, and availability | Ensure network reliability and service continuity |
| Response Time | Immediate action on security incidents | Proactive network issue resolution |
| Operational Scope | Security event lifecycle management | Network infrastructure management |
Understanding the Roles: What is a SOC vs NOC?
A Security Operations Center (SOC) specializes in monitoring, detecting, and responding to cybersecurity threats, focusing on protecting an organization's information systems from breaches and attacks. In contrast, a Network Operations Center (NOC) ensures the overall network performance, uptime, and reliability by managing infrastructure such as servers, routers, and switches. While SOC analysts handle incident response and threat intelligence, NOC teams prioritize network stability and resolving hardware or connectivity issues.
Core Functions: Security Operations Center vs Network Operations Center
Security Operations Centers (SOC) specialize in continuous threat monitoring, incident detection, and rapid response to cybersecurity breaches, focusing on protecting an organization's information assets. Network Operations Centers (NOC) concentrate on ensuring network performance, availability, and infrastructure reliability, addressing issues such as hardware failures, network outages, and connectivity problems. Both SOC and NOC are critical for organizational resilience but serve distinct roles: SOC safeguards against cyber threats, while NOC maintains optimal network functionality.
Key Differences Between SOC and NOC Teams
SOC teams specialize in detecting, investigating, and responding to cybersecurity threats using tools like SIEM and threat intelligence platforms. NOC teams focus on network performance monitoring, infrastructure uptime, and addressing hardware or software issues to ensure operational continuity. While SOC prioritizes security incident management, NOC emphasizes network availability and maintenance.
Tools and Technologies Used in SOCs and NOCs
Security Operations Centers (SOCs) utilize advanced threat detection tools such as SIEM (Security Information and Event Management), endpoint detection and response (EDR), and intrusion detection systems (IDS) to monitor and analyze security events in real-time. Network Operations Centers (NOCs) rely on network monitoring solutions, performance management software, and configuration management tools to ensure optimal network availability and performance. Both employ automation platforms, but SOC tools emphasize cybersecurity analytics, while NOC technologies focus on network infrastructure health and incident resolution.
Incident Response: How SOCs and NOCs Handle Threats
Security Operations Centers (SOCs) specialize in threat detection, analysis, and incident response by continuously monitoring security alerts and coordinating containment measures to mitigate cyberattacks. Network Operations Centers (NOCs) focus on maintaining network performance and uptime, addressing network faults, and ensuring infrastructure stability, but typically escalate security incidents to SOCs for detailed threat investigation. Effective incident response relies on the SOC's expertise in vulnerability assessment, intrusion detection systems (IDS), and real-time threat intelligence integration, while NOCs support by providing network data and operational context.
Collaboration and Interaction Between SOC and NOC
The Security Operations Center (SOC) and Network Operations Center (NOC) collaborate closely to enhance organizational cybersecurity by sharing critical data and incident insights. SOC focuses on threat detection and response, while NOC manages network performance and uptime, with their interaction enabling faster identification and mitigation of security threats affecting network infrastructure. Effective communication and real-time data exchange between SOC and NOC teams are essential for maintaining robust cybersecurity posture and minimizing system vulnerabilities.
Challenges Faced by SOCs Compared to NOCs
Security Operations Centers (SOCs) face significant challenges compared to Network Operations Centers (NOCs) due to the complexity of detecting and responding to sophisticated cyber threats, requiring advanced threat intelligence and continuous monitoring. SOCs must manage vast amounts of security alerts and differentiate between false positives and real attacks, which increases the demand for skilled cybersecurity analysts and automated solutions. Unlike NOCs that focus on network performance and availability, SOCs are tasked with protecting sensitive data and ensuring compliance with security regulations, adding layers of operational and legal complexity.
Staffing and Skill Sets: SOC vs NOC Personnel
SOC personnel specialize in cybersecurity expertise, including threat analysis, incident response, and forensic investigation, requiring certifications like CISSP, CEH, or GIAC. NOC staff focus on network performance monitoring, troubleshooting, and maintaining uptime, with skills in network protocols, hardware management, and tools like SNMP and Wireshark. The distinct skill sets reflect their roles: SOC teams defend against cyber threats, while NOC teams ensure network reliability and operational continuity.
SOC and NOC in Modern Enterprise Environments
SOC (Security Operations Center) and NOC (Network Operations Center) are integral to modern enterprise cybersecurity, where SOC specializes in detecting, analyzing, and responding to security threats in real-time. NOC focuses on maintaining network performance, availability, and infrastructure stability, ensuring seamless IT operations. Together, SOC and NOC provide comprehensive protection and operational efficiency by addressing both security risks and network management challenges.
Choosing the Right Approach: When to Integrate SOC and NOC
Integrating Security Operations Centers (SOC) and Network Operations Centers (NOC) optimizes threat detection and network performance by leveraging specialized expertise within cybersecurity and IT management. Organizations experiencing rapid growth or complex threat landscapes benefit most from combining SOC and NOC functions to ensure continuous monitoring, incident response, and infrastructure stability. Prioritizing integration depends on business size, risk tolerance, regulatory requirements, and the need for streamlined communication between security analysts and network engineers.
SOC vs NOC Infographic
 techiny.com
techiny.com