Static analysis examines source code or binaries without execution to identify vulnerabilities early in the development cycle, offering fast feedback on potential security flaws. Dynamic analysis observes a program's behavior in a runtime environment, detecting issues such as memory leaks, runtime errors, and complex security vulnerabilities that are not evident in static scans. Combining static and dynamic analysis provides comprehensive coverage, improving the detection and mitigation of cybersecurity threats.
Table of Comparison
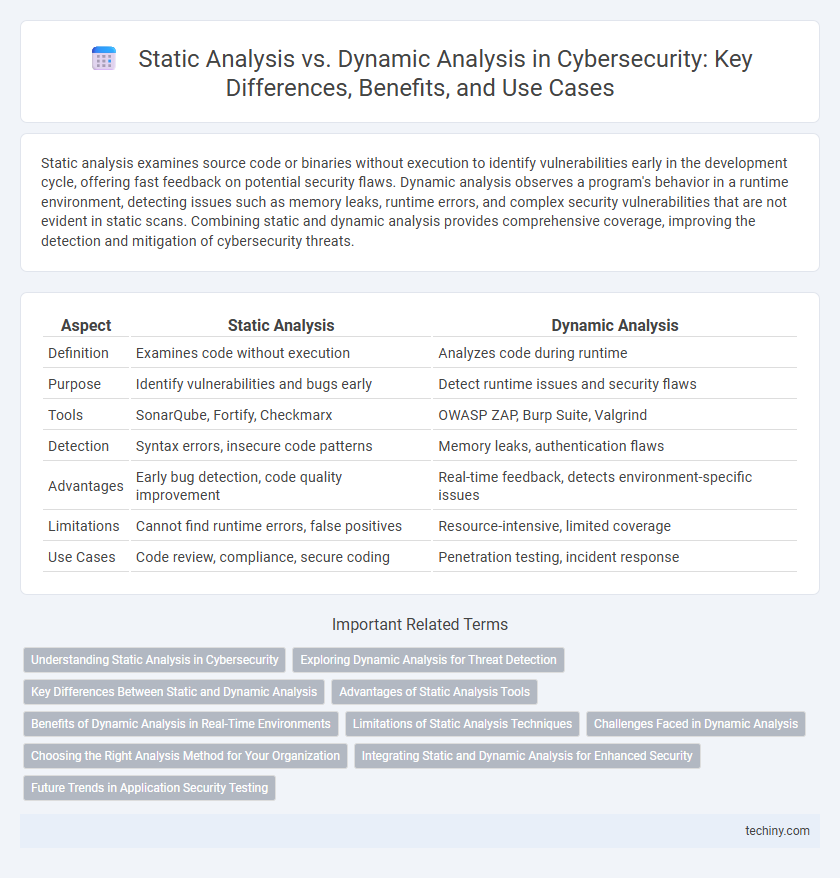
| Aspect | Static Analysis | Dynamic Analysis |
|---|---|---|
| Definition | Examines code without execution | Analyzes code during runtime |
| Purpose | Identify vulnerabilities and bugs early | Detect runtime issues and security flaws |
| Tools | SonarQube, Fortify, Checkmarx | OWASP ZAP, Burp Suite, Valgrind |
| Detection | Syntax errors, insecure code patterns | Memory leaks, authentication flaws |
| Advantages | Early bug detection, code quality improvement | Real-time feedback, detects environment-specific issues |
| Limitations | Cannot find runtime errors, false positives | Resource-intensive, limited coverage |
| Use Cases | Code review, compliance, secure coding | Penetration testing, incident response |
Understanding Static Analysis in Cybersecurity
Static analysis in cybersecurity involves examining source code or compiled binaries without executing the program to identify vulnerabilities, coding errors, and security flaws early in the development lifecycle. This method enables security teams to detect potential risks such as buffer overflows, SQL injections, and improper data handling by scanning the code against predefined rules and patterns. Tools like SonarQube, Checkmarx, and Fortify enhance security posture by automating code reviews and ensuring compliance with secure coding standards.
Exploring Dynamic Analysis for Threat Detection
Dynamic analysis enhances threat detection by executing code in a controlled environment, enabling the identification of runtime vulnerabilities and malicious behaviors that static analysis might miss. It monitors system interactions, memory usage, and network activity during execution, providing deeper insights into complex threats like zero-day exploits and polymorphic malware. This method is crucial for uncovering hidden threats in modern cybersecurity defense strategies.
Key Differences Between Static and Dynamic Analysis
Static analysis examines source code or binaries without executing the program, identifying vulnerabilities early in the development cycle such as syntax errors, insecure coding practices, and potential bugs. Dynamic analysis tests software during runtime to detect issues like memory leaks, race conditions, and runtime exceptions that are only observable during execution. Static analysis provides comprehensive code coverage and early detection, while dynamic analysis offers real-world testing and behavioral insights, making both complementary in securing software applications.
Advantages of Static Analysis Tools
Static analysis tools identify vulnerabilities early in the software development lifecycle by analyzing source code without execution, enabling faster remediation and reducing overall costs. They provide comprehensive coverage of all code paths, improving detection of potential security flaws, such as buffer overflows, SQL injection, and cross-site scripting. Integration with development environments supports continuous feedback for developers, enhancing code quality and compliance with security standards.
Benefits of Dynamic Analysis in Real-Time Environments
Dynamic analysis provides real-time threat detection by monitoring applications during execution, enhancing the identification of runtime vulnerabilities missed by static analysis. This approach enables immediate response to evolving cyber threats, improving incident prevention and minimizing potential damage. Continuous behavioral monitoring in dynamic analysis also supports adaptive security measures, ensuring robust protection in complex, real-world environments.
Limitations of Static Analysis Techniques
Static analysis techniques often struggle with detecting runtime-specific vulnerabilities such as logic errors or issues caused by dynamic code behavior, limiting their effectiveness in identifying all potential security threats. These methods can produce a high rate of false positives due to rigid pattern matching and inability to fully interpret program context or external dependencies. Furthermore, static analysis tools may fail to analyze obfuscated code or encrypted data within software, reducing their accuracy in comprehensive cybersecurity assessments.
Challenges Faced in Dynamic Analysis
Dynamic analysis faces significant challenges including handling the high computational overhead required for real-time code execution monitoring and the difficulty of accurately simulating all possible runtime environments, which can result in incomplete analysis. Malware authors often employ evasion techniques such as environment checks and time delays to bypass dynamic analysis tools, complicating the detection process. Moreover, dynamic analysis struggles with scalability and resource constraints when analyzing large codebases or complex software systems, limiting its efficiency in enterprise-level cybersecurity operations.
Choosing the Right Analysis Method for Your Organization
Choosing the right analysis method for your organization depends on the specific security goals and resources available. Static analysis excels in early-stage code review by identifying vulnerabilities without executing programs, saving time in development cycles. Dynamic analysis provides real-time monitoring and detection of runtime behavior, making it ideal for uncovering complex security flaws in deployed applications.
Integrating Static and Dynamic Analysis for Enhanced Security
Integrating static and dynamic analysis combines the strengths of both methodologies, enabling comprehensive vulnerability detection by analyzing code without execution and monitoring behavior during runtime. This hybrid approach improves threat identification accuracy, reduces false positives, and uncovers hidden security flaws that single-method analysis might miss. Organizations employing integrated analysis tools benefit from faster remediation cycles and stronger protection against sophisticated cyber attacks.
Future Trends in Application Security Testing
Future trends in application security testing emphasize the integration of AI-driven static analysis tools that enhance vulnerability detection accuracy during the development phase. Advances in dynamic analysis incorporate real-time behavioral monitoring and automated exploit simulation to identify complex runtime threats. Combining these approaches with continuous integration pipelines ensures adaptive, proactive defense mechanisms against evolving cyber threats.
Static Analysis vs Dynamic Analysis Infographic
 techiny.com
techiny.com