Steganography conceals information within non-suspicious files to avoid detection, while cryptography transforms data into an unreadable format to protect its content from unauthorized access. Both techniques enhance cybersecurity by safeguarding sensitive information, but steganography prioritizes hiding the existence of the message, whereas cryptography emphasizes securing the message itself. Combining these methods can provide robust protection against data breaches and cyberattacks.
Table of Comparison
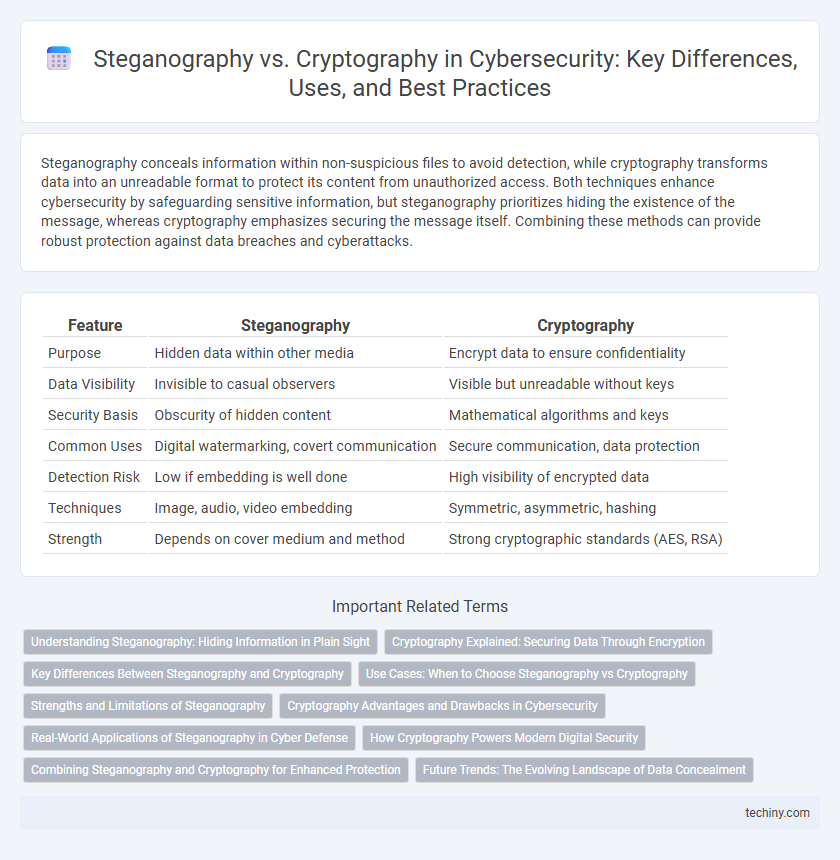
| Feature | Steganography | Cryptography |
|---|---|---|
| Purpose | Hidden data within other media | Encrypt data to ensure confidentiality |
| Data Visibility | Invisible to casual observers | Visible but unreadable without keys |
| Security Basis | Obscurity of hidden content | Mathematical algorithms and keys |
| Common Uses | Digital watermarking, covert communication | Secure communication, data protection |
| Detection Risk | Low if embedding is well done | High visibility of encrypted data |
| Techniques | Image, audio, video embedding | Symmetric, asymmetric, hashing |
| Strength | Depends on cover medium and method | Strong cryptographic standards (AES, RSA) |
Understanding Steganography: Hiding Information in Plain Sight
Steganography conceals messages within innocuous-looking files such as images, audio, or video, making the hidden data undetectable to the human eye or basic inspection tools. Unlike cryptography, which encrypts information to render it unreadable without a decryption key, steganography aims to mask the very existence of the message by embedding it in digital media. This technique is critical in cybersecurity for covert communication and information hiding, especially in scenarios where encrypted data might attract unwanted attention.
Cryptography Explained: Securing Data Through Encryption
Cryptography secures data by converting plaintext into unreadable ciphertext using algorithms like AES and RSA, ensuring confidentiality and integrity during transmission. It employs techniques such as symmetric and asymmetric encryption to protect sensitive information against unauthorized access and cyber threats. Modern cryptographic protocols also provide authentication and non-repudiation, reinforcing trust in digital communications and data storage.
Key Differences Between Steganography and Cryptography
Steganography conceals the existence of a message by embedding it within another medium, whereas cryptography encrypts the message, transforming it into an unreadable format to unauthorized users. Steganography prioritizes hiding the fact that communication is taking place, while cryptography focuses on protecting the content's confidentiality and integrity. Key differences include steganography's use of cover media like images or audio versus cryptography's reliance on algorithms and keys to secure the data.
Use Cases: When to Choose Steganography vs Cryptography
Steganography is ideal for covert communication where hiding the very existence of the message is crucial, such as embedding confidential data within images or audio files to avoid detection in espionage or digital watermarking. Cryptography should be chosen when securing data integrity and confidentiality is paramount, especially for encrypting sensitive information like passwords, financial transactions, or confidential communications against unauthorized access. Combining both techniques enhances cybersecurity by first encrypting data and then concealing it, providing robust protection in high-stakes scenarios such as military or intelligence operations.
Strengths and Limitations of Steganography
Steganography offers the unique strength of concealing the very existence of a message, making it less likely to attract unauthorized attention compared to cryptography, which scrambles content but signals encrypted communication. Its limitations include vulnerability to detection through steganalysis techniques and restricted capacity for embedding data without degrading the host file's quality. Steganography is most effective when combined with cryptographic methods to enhance security by both hiding and encrypting sensitive information.
Cryptography Advantages and Drawbacks in Cybersecurity
Cryptography enhances cybersecurity by ensuring data confidentiality, integrity, and authentication through advanced encryption algorithms like AES and RSA. Its main advantages include strong protection against unauthorized access and secure communication over untrusted networks, while drawbacks involve computational overhead and vulnerability to sophisticated attacks if key management is weak. Despite challenges, cryptography remains essential for safeguarding sensitive information in digital environments.
Real-World Applications of Steganography in Cyber Defense
Steganography is widely used in cyber defense to covertly embed sensitive information within digital media, such as images, audio, and video files, enabling secure communication without arousing suspicion. Unlike cryptography, which encrypts data to prevent unauthorized access, steganography hides the existence of the message itself, making it effective for data exfiltration prevention and secure watermarking in digital forensics. Real-world applications include embedding authentication codes in software distributions, protecting intellectual property, and facilitating covert communication channels for intelligence agencies.
How Cryptography Powers Modern Digital Security
Cryptography underpins modern digital security by encrypting sensitive data, ensuring confidentiality, integrity, and authentication across communication channels. Unlike steganography, which conceals information within other media, cryptography transforms data into complex ciphertext, making unauthorized access computationally infeasible. Advanced algorithms such as AES and RSA enable secure online transactions, virtual private networks (VPNs), and encrypted messaging, forming the backbone of cybersecurity defenses against hacking and data breaches.
Combining Steganography and Cryptography for Enhanced Protection
Combining steganography and cryptography creates a robust dual-layer security approach by first encrypting sensitive data and then hiding it within innocuous files, making detection and interception significantly more difficult. This synergy enhances confidentiality, as cryptography ensures data confidentiality even if discovered, while steganography obscures the very existence of the message. Implementing both technologies addresses vulnerabilities inherent in each technique when used alone, providing a comprehensive cybersecurity protection mechanism against unauthorized access and data breaches.
Future Trends: The Evolving Landscape of Data Concealment
Steganography and cryptography are both critical in data protection, with cryptography focusing on encrypting data to ensure confidentiality, while steganography conceals the existence of data within other media. Future trends in cybersecurity indicate a growing integration of these techniques to enhance security protocols, leveraging advancements in AI-driven pattern recognition and quantum-resistant algorithms. The evolving landscape emphasizes real-time adaptive systems that combine cryptographic encryption with dynamic steganographic methods to counter increasingly sophisticated cyber threats.
Steganography vs cryptography Infographic
 techiny.com
techiny.com