Zero-day exploits target previously unknown vulnerabilities, leaving systems defenseless until patches are developed and deployed, while known exploits attack already identified flaws that have existing security measures or updates. Organizations prioritize zero-day threat detection through advanced monitoring and behavior analysis to mitigate risks before exploits are weaponized. Understanding the distinction between zero-day and known exploits enables cybersecurity teams to tailor defenses and response strategies effectively.
Table of Comparison
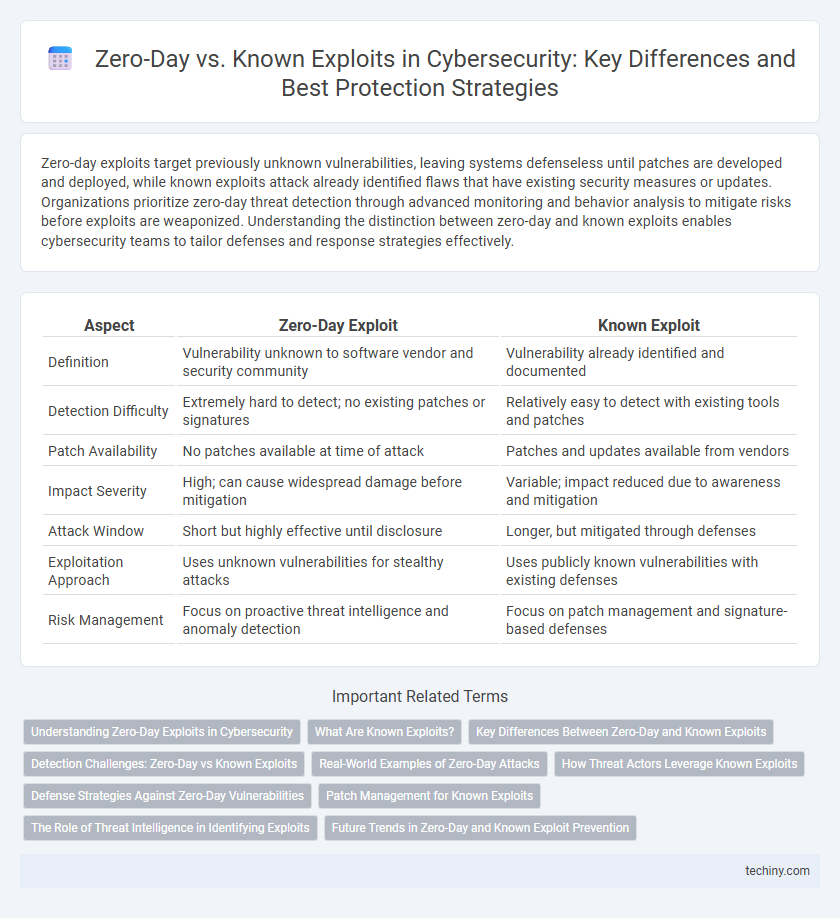
| Aspect | Zero-Day Exploit | Known Exploit |
|---|---|---|
| Definition | Vulnerability unknown to software vendor and security community | Vulnerability already identified and documented |
| Detection Difficulty | Extremely hard to detect; no existing patches or signatures | Relatively easy to detect with existing tools and patches |
| Patch Availability | No patches available at time of attack | Patches and updates available from vendors |
| Impact Severity | High; can cause widespread damage before mitigation | Variable; impact reduced due to awareness and mitigation |
| Attack Window | Short but highly effective until disclosure | Longer, but mitigated through defenses |
| Exploitation Approach | Uses unknown vulnerabilities for stealthy attacks | Uses publicly known vulnerabilities with existing defenses |
| Risk Management | Focus on proactive threat intelligence and anomaly detection | Focus on patch management and signature-based defenses |
Understanding Zero-Day Exploits in Cybersecurity
Zero-day exploits target unknown vulnerabilities that have no existing patches or fixes, making them highly dangerous in cybersecurity. Unlike known exploits, which hackers use after vulnerabilities are publicly disclosed and security patches are available, zero-day attacks exploit flaws before developers are aware. Effective defense against zero-day exploits involves advanced threat detection, behavior analysis, and rapid incident response to minimize potential damage.
What Are Known Exploits?
Known exploits are vulnerabilities in software or hardware that have been identified, documented, and often patched by developers, making them easier to detect and defend against. These exploits are cataloged in databases such as the CVE (Common Vulnerabilities and Exposures) system, which cybersecurity professionals use to implement targeted defenses and update security protocols. Unlike zero-day exploits, known exploits rely on previously discovered weaknesses, allowing businesses and security teams to mitigate risks by applying security patches and updates promptly.
Key Differences Between Zero-Day and Known Exploits
Zero-day exploits target previously unknown vulnerabilities, leaving no time for developers to create patches, whereas known exploits leverage publicly disclosed weaknesses with existing security updates. Zero-day attacks pose a higher risk due to the absence of available defenses, while known exploits can be mitigated by timely software updates and vulnerability management. Understanding these differences is crucial for implementing proactive cybersecurity measures and prioritizing threat detection and response strategies.
Detection Challenges: Zero-Day vs Known Exploits
Zero-day exploits present significant detection challenges due to their unknown nature, lacking signatures or behavioral patterns in threat databases, which makes traditional signature-based antivirus tools ineffective. Known exploits benefit from established detection mechanisms utilizing updated signature-based defenses, heuristic analysis, and threat intelligence feeds, allowing security systems to quickly identify and mitigate these threats. Advanced detection solutions employing machine learning and anomaly detection are crucial in addressing zero-day vulnerabilities by identifying irregular system behaviors without relying on prior knowledge of the exploits.
Real-World Examples of Zero-Day Attacks
Zero-day attacks exploit previously unknown vulnerabilities, making detection and prevention extremely challenging for cybersecurity defenses. Real-world examples include the Stuxnet worm, which targeted Iranian nuclear facilities, and the WannaCry ransomware, which leveraged a zero-day Windows exploit to infect hundreds of thousands of computers globally. Organizations must implement proactive threat intelligence and rapid patch management to mitigate the risks posed by zero-day vulnerabilities compared to known exploits.
How Threat Actors Leverage Known Exploits
Threat actors frequently leverage known exploits by targeting unpatched systems and software vulnerabilities to maximize attack success rates. These exploits are easier to weaponize due to publicly available information, enabling automated attack tools to rapidly propagate malware and gain unauthorized access. Continuous vulnerability scanning and timely patch management are critical defenses against such attacks.
Defense Strategies Against Zero-Day Vulnerabilities
Zero-day vulnerabilities are unknown to software vendors and lack patches, making them highly dangerous compared to known exploits with available fixes. Defense strategies against zero-day attacks emphasize proactive threat intelligence, behavior-based anomaly detection, and multi-layered endpoint protection to identify and mitigate suspicious activities before exploitation. Regular software updates, network segmentation, and employee cybersecurity training further strengthen resilience against zero-day threats by minimizing attack surfaces and enhancing detection capabilities.
Patch Management for Known Exploits
Patch management is crucial for mitigating known exploits by promptly applying security updates that address identified vulnerabilities in software. Implementing automated patching systems reduces the window of exposure by ensuring timely deployment of vendor-released fixes. Regular patch audits and vulnerability assessments help maintain a resilient cybersecurity posture against threats exploiting documented weaknesses.
The Role of Threat Intelligence in Identifying Exploits
Threat intelligence plays a critical role in distinguishing zero-day exploits from known vulnerabilities by aggregating real-time data from diverse sources to detect emerging threats. By continuously analyzing attack patterns and indicators of compromise, security teams can identify unusual behaviors indicative of zero-day attacks before signatures exist. Integrating threat intelligence with automated detection tools enhances the speed and accuracy of exploit identification, significantly reducing the window of vulnerability.
Future Trends in Zero-Day and Known Exploit Prevention
Zero-Day vulnerabilities remain a critical threat due to their undisclosed nature, pushing advancements in AI-driven threat detection and behavior-based analytics to identify anomalous activities before exploitation. Known exploits benefit from automated patch management systems and threat intelligence sharing platforms, enhancing rapid response and mitigation strategies across organizations. Future trends emphasize integrating real-time monitoring with predictive analytics and zero-trust architectures to fortify defenses against both zero-day and known exploit attacks.
Zero-Day vs Known Exploit Infographic
 techiny.com
techiny.com