Zero-day vulnerabilities are security flaws unknown to software vendors, leaving systems exposed without available patches. Known vulnerabilities have identified weaknesses with established fixes, allowing organizations to mitigate risks effectively. Prioritizing the detection and remediation of zero-day exploits is crucial to strengthening overall cybersecurity defenses.
Table of Comparison
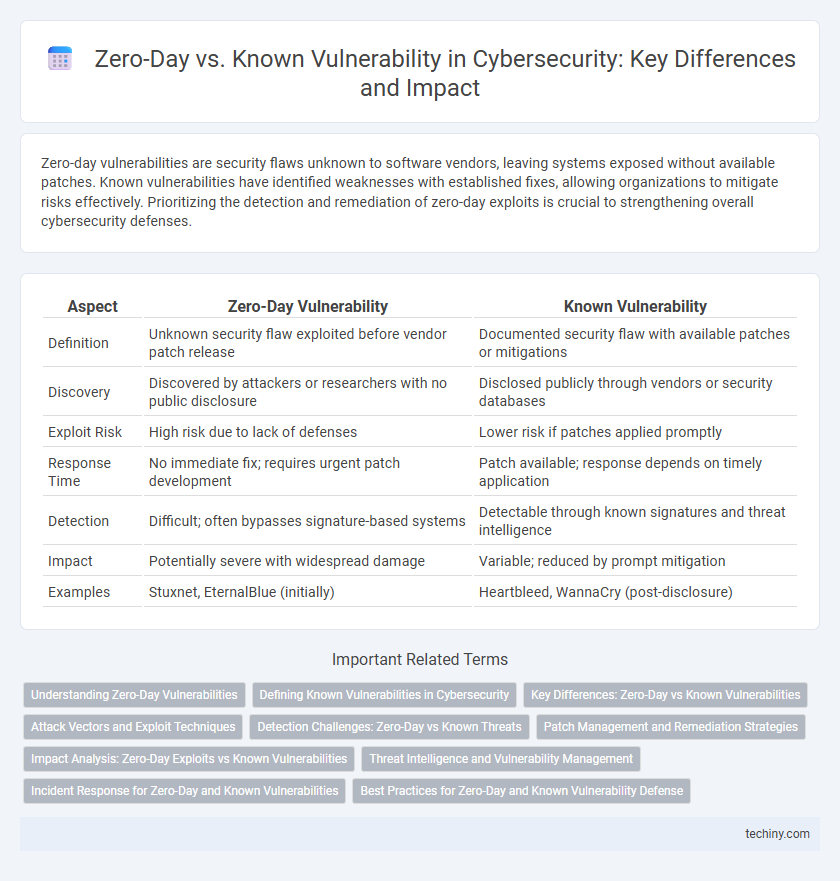
| Aspect | Zero-Day Vulnerability | Known Vulnerability |
|---|---|---|
| Definition | Unknown security flaw exploited before vendor patch release | Documented security flaw with available patches or mitigations |
| Discovery | Discovered by attackers or researchers with no public disclosure | Disclosed publicly through vendors or security databases |
| Exploit Risk | High risk due to lack of defenses | Lower risk if patches applied promptly |
| Response Time | No immediate fix; requires urgent patch development | Patch available; response depends on timely application |
| Detection | Difficult; often bypasses signature-based systems | Detectable through known signatures and threat intelligence |
| Impact | Potentially severe with widespread damage | Variable; reduced by prompt mitigation |
| Examples | Stuxnet, EternalBlue (initially) | Heartbleed, WannaCry (post-disclosure) |
Understanding Zero-Day Vulnerabilities
Zero-day vulnerabilities are security flaws unknown to software vendors and lack official patches, making them highly exploitable by attackers. Unlike known vulnerabilities, which have documented fixes and detection methods, zero-days pose a greater risk due to the absence of immediate defense mechanisms. Effective cybersecurity strategies prioritize continuous monitoring and threat intelligence to detect and mitigate zero-day exploits before they cause significant damage.
Defining Known Vulnerabilities in Cybersecurity
Known vulnerabilities in cybersecurity are security flaws that have been identified, documented, and cataloged in public databases such as the Common Vulnerabilities and Exposures (CVE) system. These vulnerabilities come with available patches or mitigation strategies that organizations can deploy to protect systems and networks from exploitation. Timely detection and remediation of known vulnerabilities are crucial for reducing attack surfaces and preventing unauthorized access or data breaches.
Key Differences: Zero-Day vs Known Vulnerabilities
Zero-day vulnerabilities are security flaws unknown to software vendors and lack available patches, making them highly exploitable by attackers. Known vulnerabilities, conversely, have been identified and documented, with vendors typically issuing updates or patches to mitigate risks. The key difference lies in the time window for defense: zero-days expose systems before protection is available, whereas known vulnerabilities can be proactively addressed through timely patch management.
Attack Vectors and Exploit Techniques
Zero-day vulnerabilities exploit unknown software flaws that lack existing patches, enabling attackers to employ sophisticated techniques like remote code execution and privilege escalation before detection. Known vulnerabilities rely on publicly available information and are typically targeted through automated scanning tools and exploit kits designed to capitalize on unpatched systems. Attack vectors for zero-day attacks often include spear-phishing and supply chain infiltration, while known vulnerabilities are frequently exploited via widespread malware campaigns and network intrusions.
Detection Challenges: Zero-Day vs Known Threats
Zero-day vulnerabilities lack publicly available signatures, making them difficult for traditional security tools to detect compared to known threats with established detection patterns. Behavioral analysis and heuristic-based approaches offer better detection capabilities for zero-day exploits by identifying anomalous activities rather than relying on signature databases. Organizations face greater challenges in response time and mitigation for zero-day attacks due to the absence of prior knowledge and limited threat intelligence.
Patch Management and Remediation Strategies
Zero-day vulnerabilities pose significant challenges in cybersecurity because they are unknown to software vendors and lack existing patches, necessitating proactive threat detection and rapid response measures. In contrast, known vulnerabilities have established patches that can be deployed through effective patch management systems, reducing exploit risks when timely updates are applied. Implementing automated patching workflows and continuous monitoring enhances remediation strategies by minimizing exposure windows and preventing exploitation of both zero-day and known vulnerabilities.
Impact Analysis: Zero-Day Exploits vs Known Vulnerabilities
Zero-day exploits pose a significantly higher risk in impact analysis due to the absence of available patches or detection signatures, allowing attackers to compromise systems undetected. Known vulnerabilities, while potentially severe, benefit from existing security measures such as updates, patches, and intrusion detection systems that mitigate exploitation likelihood and severity. The critical difference in impact lies in the response time and preparedness, with zero-day vulnerabilities demanding accelerated threat intelligence and proactive defense strategies to minimize damage.
Threat Intelligence and Vulnerability Management
Zero-day vulnerabilities represent unpatched security flaws unknown to vendors and threat intelligence sources, posing significant challenges for vulnerability management due to the absence of available fixes or detection signatures. Known vulnerabilities benefit from comprehensive threat intelligence, enabling organizations to prioritize patches and deploy mitigations based on exploit data and risk assessments. Effective vulnerability management integrates continuous threat intelligence feeds to identify emerging zero-day exploits while systematically addressing known vulnerabilities to reduce the attack surface.
Incident Response for Zero-Day and Known Vulnerabilities
Incident response to zero-day vulnerabilities requires rapid identification and containment measures due to the absence of existing patches or signatures, emphasizing heuristic analysis and threat intelligence integration. Known vulnerability incidents benefit from predefined remediation steps and patch deployment, allowing quicker mitigation and system recovery. Effective incident response frameworks leverage continuous monitoring and automated alerting to reduce dwell time for both zero-day and known exploits.
Best Practices for Zero-Day and Known Vulnerability Defense
Implementing a multi-layered security approach, including advanced threat detection systems and real-time monitoring, is crucial for defending against zero-day exploits and known vulnerabilities. Regular patch management combined with behavioral analysis helps mitigate risks by promptly addressing known vulnerabilities while detecting anomalous activities indicative of zero-day attacks. Employing threat intelligence sharing and automated response protocols further enhances resilience by enabling rapid identification and containment of emerging threats.
zero-day vs known vulnerability Infographic
 techiny.com
techiny.com