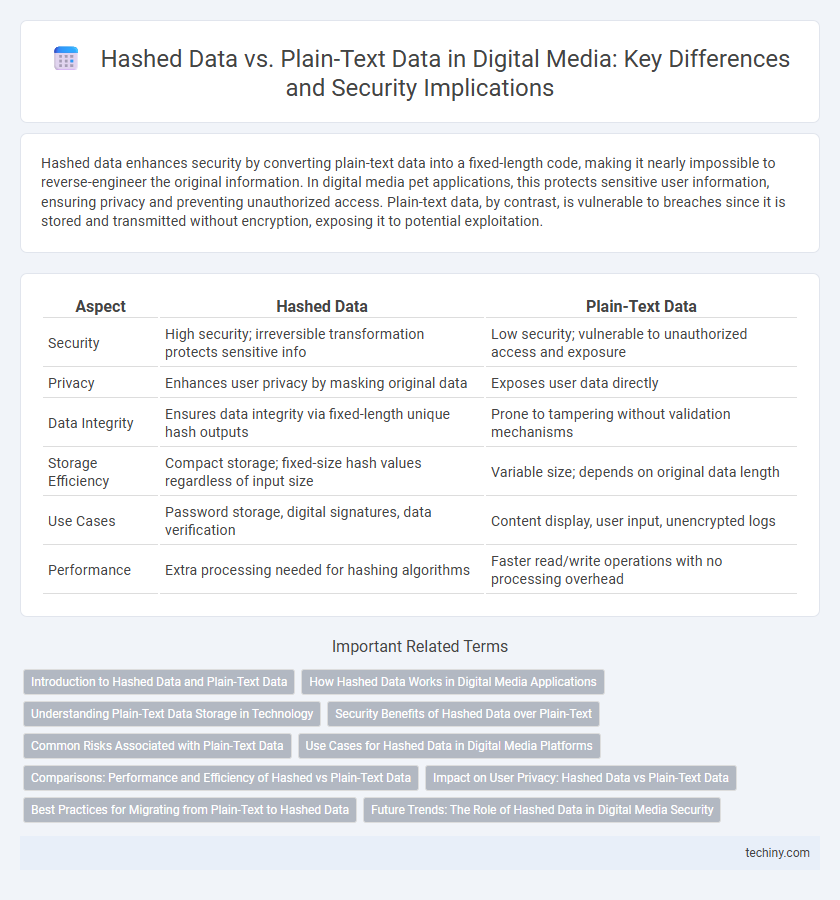
Hashed data enhances security by converting plain-text data into a fixed-length code, making it nearly impossible to reverse-engineer the original information. In digital media pet applications, this protects sensitive user information, ensuring privacy and preventing unauthorized access. Plain-text data, by contrast, is vulnerable to breaches since it is stored and transmitted without encryption, exposing it to potential exploitation.
Table of Comparison
| Aspect | Hashed Data | Plain-Text Data |
|---|---|---|
| Security | High security; irreversible transformation protects sensitive info | Low security; vulnerable to unauthorized access and exposure |
| Privacy | Enhances user privacy by masking original data | Exposes user data directly |
| Data Integrity | Ensures data integrity via fixed-length unique hash outputs | Prone to tampering without validation mechanisms |
| Storage Efficiency | Compact storage; fixed-size hash values regardless of input size | Variable size; depends on original data length |
| Use Cases | Password storage, digital signatures, data verification | Content display, user input, unencrypted logs |
| Performance | Extra processing needed for hashing algorithms | Faster read/write operations with no processing overhead |
Introduction to Hashed Data and Plain-Text Data
Hashed data transforms plain-text information into a fixed-length string of characters using cryptographic algorithms, enhancing security by making it computationally infeasible to revert to the original data. Plain-text data refers to readable and unencrypted information that is vulnerable to unauthorized access and data breaches. Understanding the distinction between hashed and plain-text data is crucial for protecting sensitive digital media content in databases and transmission.
How Hashed Data Works in Digital Media Applications
Hashed data in digital media applications transforms original content into fixed-length strings using cryptographic hash functions, ensuring data integrity and authenticity. This process prevents unauthorized alterations by generating unique hash values for media files, which can be verified easily during transmission or storage. By comparing hash values, digital platforms efficiently detect tampering or corruption without exposing the original plain-text data, enhancing security and trust in digital content distribution.
Understanding Plain-Text Data Storage in Technology
Plain-text data storage in technology involves saving information exactly as it is, without any encryption or obfuscation, making it easily readable by both humans and machines. This method poses significant security risks, as unauthorized access can lead to data breaches and exposure of sensitive information. Proper understanding of plain-text storage highlights the importance of implementing hashed data techniques to enhance data security and integrity in digital media systems.
Security Benefits of Hashed Data over Plain-Text
Hashed data enhances security by transforming plain-text information into a fixed-length string of characters, making it nearly impossible to reverse-engineer the original content. Unlike plain-text data, which is vulnerable to direct exposure during breaches, hashed data ensures sensitive information such as passwords or personal details remains protected even if accessed by unauthorized parties. This cryptographic process significantly reduces the risk of data theft and unauthorized access in digital media applications.
Common Risks Associated with Plain-Text Data
Plain-text data in digital media is highly vulnerable to interception, unauthorized access, and data breaches due to its unencrypted nature. Common risks include identity theft, exposure of sensitive information, and exploitation by cybercriminals through phishing or man-in-the-middle attacks. Without hashing, plain-text data lacks integrity verification, increasing susceptibility to tampering and unauthorized modifications.
Use Cases for Hashed Data in Digital Media Platforms
Hashed data enhances security in digital media platforms by protecting user credentials and sensitive information from breaches, ensuring safer authentication processes. Content verification and digital rights management rely on hashing algorithms to validate integrity and prevent unauthorized alterations or piracy. Hashing also enables efficient caching and deduplication by generating unique signatures for media files, optimizing storage and delivery across streaming services.
Comparisons: Performance and Efficiency of Hashed vs Plain-Text Data
Hashed data significantly enhances performance and efficiency in digital media by enabling faster data retrieval and secure verification processes compared to plain-text data, which requires more processing power for encryption and decryption. Hashing reduces storage requirements and accelerates database indexing, facilitating quicker search operations in large media libraries. In contrast, plain-text data increases vulnerability to breaches, demanding additional computational resources for maintaining confidentiality and integrity.
Impact on User Privacy: Hashed Data vs Plain-Text Data
Hashed data significantly enhances user privacy by transforming sensitive information into irreversible, encrypted strings, minimizing the risk of data breaches and unauthorized access compared to plain-text data, which remains vulnerable and easily readable. The use of hashing algorithms, such as SHA-256 or bcrypt, ensures that even if data is intercepted, it cannot be reverse-engineered to reveal original user details. Consequently, platforms handling digital media content prioritize hashed storage of credentials and personal identifiers to comply with strict data protection regulations and safeguard user anonymity.
Best Practices for Migrating from Plain-Text to Hashed Data
Migrating from plain-text to hashed data requires implementing strong cryptographic hash functions such as SHA-256 or bcrypt to ensure data integrity and security. It is essential to apply salting techniques to protect against rainbow table attacks and maintain confidentiality of sensitive digital media assets. Regularly updating hashing algorithms and conducting thorough testing during migration can prevent data corruption and support compliance with data protection regulations.
Future Trends: The Role of Hashed Data in Digital Media Security
Hashed data enhances digital media security by transforming sensitive information into fixed-length codes that prevent unauthorized access and ensure data integrity. Future trends indicate increased adoption of advanced hashing algorithms combined with blockchain technology to verify content authenticity and combat digital piracy. As cyber threats evolve, hashed data will be pivotal for secure content distribution, user authentication, and safeguarding intellectual property in digital ecosystems.
hashed data vs plain-text data Infographic
 techiny.com
techiny.com