Watermarking embeds visible or invisible marks in digital media to verify ownership and protect intellectual property, ensuring authenticity without significantly altering the original content. Steganography conceals hidden messages within media files, maintaining secrecy by embedding data in ways undetectable to the naked eye. Both techniques enhance digital media security but serve different purposes: watermarking for copyright protection and steganography for covert communication.
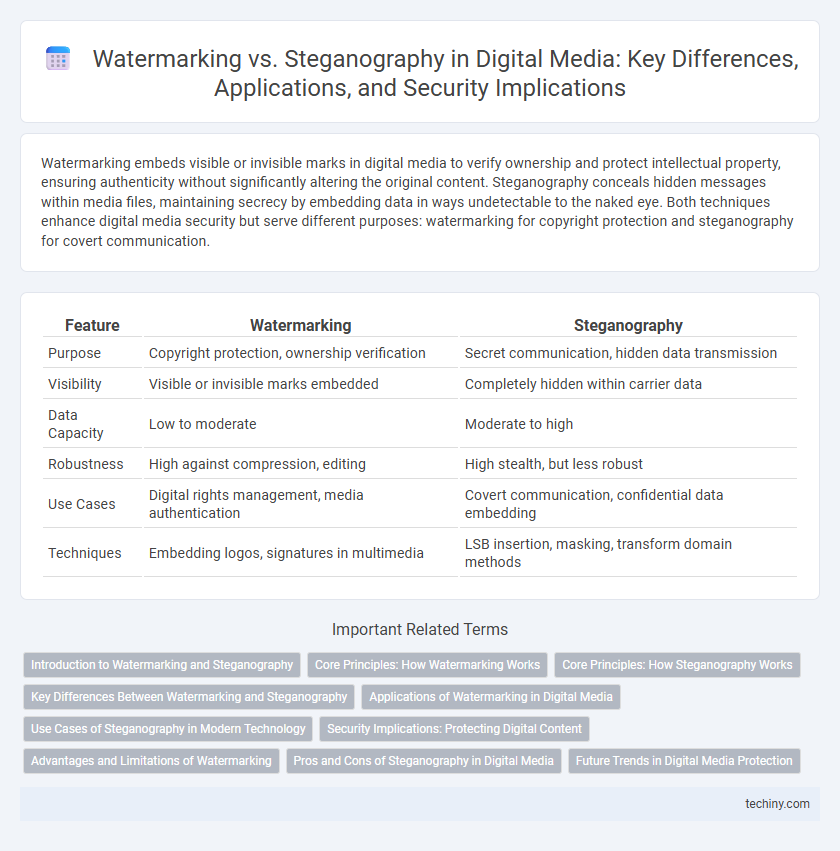
Table of Comparison
| Feature | Watermarking | Steganography |
|---|---|---|
| Purpose | Copyright protection, ownership verification | Secret communication, hidden data transmission |
| Visibility | Visible or invisible marks embedded | Completely hidden within carrier data |
| Data Capacity | Low to moderate | Moderate to high |
| Robustness | High against compression, editing | High stealth, but less robust |
| Use Cases | Digital rights management, media authentication | Covert communication, confidential data embedding |
| Techniques | Embedding logos, signatures in multimedia | LSB insertion, masking, transform domain methods |
Introduction to Watermarking and Steganography
Watermarking embeds visible or invisible identifiable patterns into digital media to assert copyright and authenticity, while steganography conceals information within digital files to ensure covert communication. Watermarking primarily safeguards intellectual property by embedding robust marks resistant to tampering or removal. Steganography enhances security by hiding messages without altering the perceived content, supporting secret data transmission in images, audio, and video files.
Core Principles: How Watermarking Works
Watermarking embeds visible or invisible marks into digital media to assert ownership and protect copyright, using techniques such as frequency domain alteration or spatial domain modification. This process ensures that the watermark remains robust against common attacks like compression, cropping, or noise addition, preserving the integrity of the original content. Unlike steganography, watermarking emphasizes traceability and authenticity rather than concealment of information.
Core Principles: How Steganography Works
Steganography operates by embedding hidden information within digital media files, such as images, audio, or video, without noticeably altering the file's appearance or quality. It leverages techniques like least significant bit (LSB) modification to conceal data within the carrier file, ensuring the concealed message remains undetectable to casual observers. The core principle relies on the imperceptibility of changes while maintaining underlying communication secrecy and data integrity.
Key Differences Between Watermarking and Steganography
Watermarking embeds visible or invisible marks into digital media to assert copyright ownership and authenticity, while steganography conceals secret information within digital files to ensure covert communication. Watermarking prioritizes robustness against tampering and is often detectable for verification, whereas steganography emphasizes imperceptibility and secrecy, aiming to avoid detection altogether. The key distinction lies in watermarking's role in intellectual property protection versus steganography's use in secure data transmission.
Applications of Watermarking in Digital Media
Watermarking in digital media is primarily used for copyright protection, enabling content creators to embed visible or invisible marks that assert ownership and prevent unauthorized use. It also plays a crucial role in content authentication, helping verify the integrity and source of digital images, videos, and audio files. Furthermore, watermarking supports digital rights management (DRM) by controlling access and distribution channels, especially in streaming platforms and online publishing.
Use Cases of Steganography in Modern Technology
Steganography in modern technology is primarily used for secure communication, enabling hidden messages within images, audio, or video files to prevent unauthorized access. It supports digital rights management by embedding copyright information without altering the original media's appearance. Emerging applications include enhanced cybersecurity measures in IoT devices and covert data transmission in defense systems, maximizing privacy and data integrity.
Security Implications: Protecting Digital Content
Watermarking embeds visible or invisible marks into digital media to assert ownership and deter unauthorized use, providing traceable evidence in legal disputes. Steganography conceals information within the media, enhancing covert communication but posing risks if exploited for malicious data transmission. Both techniques offer unique security implications; watermarking ensures content authentication and copyright protection, while steganography demands careful management to prevent misuse and maintain integrity.
Advantages and Limitations of Watermarking
Watermarking offers robust copyright protection by embedding visible or invisible marks directly into digital media, ensuring authentic ownership verification without degrading the content quality. Its advantage lies in resilience against common attacks such as compression and cropping, but it may be susceptible to removal through advanced signal processing techniques. Limitations include reduced effectiveness in highly compressed files and potential visibility of watermarks that can distract users or alter aesthetic value.
Pros and Cons of Steganography in Digital Media
Steganography in digital media offers the advantage of concealing information within multimedia files, such as images, audio, or video, making it difficult for unauthorized users to detect the presence of hidden data. Key benefits include enhanced privacy and covert communication, along with the ability to embed data without significantly altering the original content's quality. However, steganography faces limitations like vulnerability to compression and format conversion, which can degrade or eliminate embedded information, and the complexity of implementation compared to visible watermarking techniques.
Future Trends in Digital Media Protection
Watermarking and steganography are evolving with advancements in AI and blockchain to enhance digital media protection by enabling more secure and tamper-proof content authentication. Emerging techniques focus on invisible, robust watermarking integrated with machine learning algorithms for real-time detection and verification of digital assets. Future trends emphasize seamless incorporation of these technologies within digital rights management systems to prevent unauthorized distribution and ensure content integrity across decentralized platforms.
Watermarking vs Steganography Infographic
 techiny.com
techiny.com