Device authentication verifies the identity of an Internet of Things (IoT) device, ensuring that only legitimate devices can access the network by validating credentials such as digital certificates or cryptographic keys. Device authorization determines the level of access or permissions granted to an authenticated IoT device, controlling what resources or data the device can interact with based on predefined policies. Effective security in IoT relies on both authentication to prevent unauthorized devices from connecting and authorization to enforce granular access controls within the ecosystem.
Table of Comparison
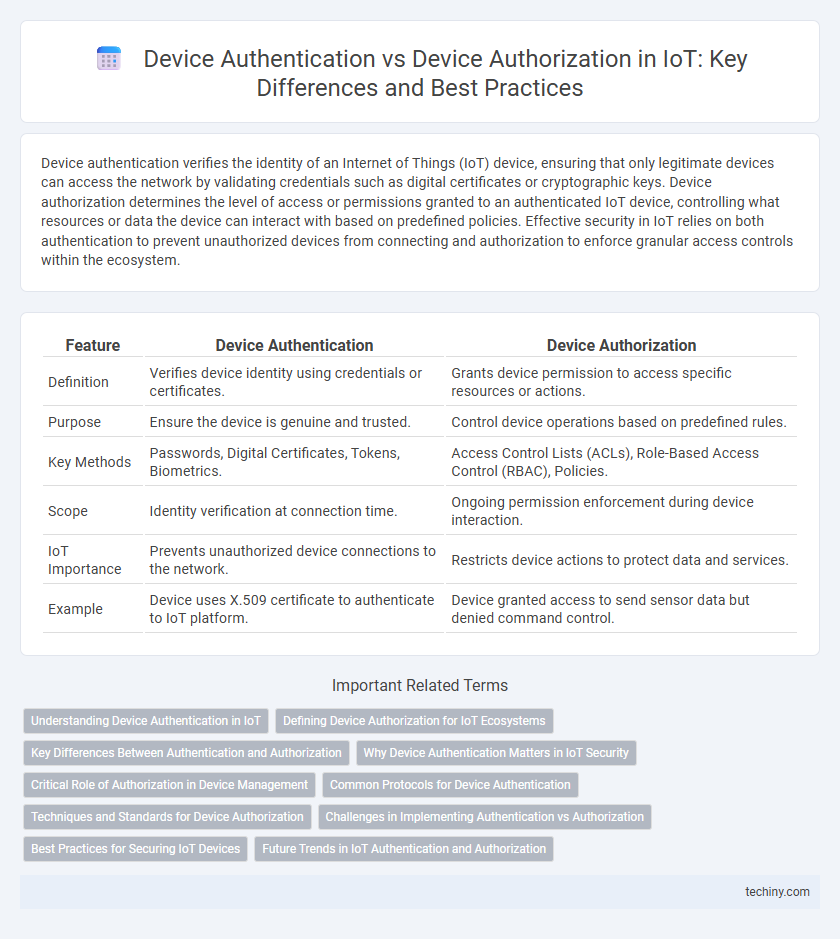
| Feature | Device Authentication | Device Authorization |
|---|---|---|
| Definition | Verifies device identity using credentials or certificates. | Grants device permission to access specific resources or actions. |
| Purpose | Ensure the device is genuine and trusted. | Control device operations based on predefined rules. |
| Key Methods | Passwords, Digital Certificates, Tokens, Biometrics. | Access Control Lists (ACLs), Role-Based Access Control (RBAC), Policies. |
| Scope | Identity verification at connection time. | Ongoing permission enforcement during device interaction. |
| IoT Importance | Prevents unauthorized device connections to the network. | Restricts device actions to protect data and services. |
| Example | Device uses X.509 certificate to authenticate to IoT platform. | Device granted access to send sensor data but denied command control. |
Understanding Device Authentication in IoT
Device authentication in IoT establishes the identity of a device using methods such as digital certificates, cryptographic keys, or biometric data to ensure that only legitimate devices connect to the network. It plays a crucial role in preventing unauthorized access by verifying device credentials before granting network entry. Unlike device authorization, which controls the permissions and actions a device can perform after authentication, authentication serves as the initial security gate in IoT ecosystems.
Defining Device Authorization for IoT Ecosystems
Device authorization in IoT ecosystems involves granting specific permissions and access rights to authenticated devices based on predefined policies and roles. Unlike device authentication, which verifies the identity of devices trying to connect to the network, device authorization controls what actions those authenticated devices can perform within the system. Effective device authorization ensures secure interaction between devices, preventing unauthorized access to sensitive data and critical infrastructure.
Key Differences Between Authentication and Authorization
Device authentication in the Internet of Things verifies the identity of a device by validating credentials such as digital certificates or cryptographic keys. Device authorization determines the level of access or permissions granted to an authenticated device within an IoT network, regulating which resources or services it can interact with. Authentication is the initial security checkpoint ensuring only trusted devices connect, while authorization controls the scope of actions permitted post-authentication.
Why Device Authentication Matters in IoT Security
Device authentication ensures that each connected IoT device is verified as legitimate before gaining network access, preventing unauthorized devices from infiltrating the system. This critical security measure protects sensitive data and maintains network integrity by mitigating risks like identity spoofing and unauthorized control. Without robust device authentication, IoT ecosystems become vulnerable to attacks, leading to potential data breaches and operational disruptions.
Critical Role of Authorization in Device Management
Device authentication verifies the identity of IoT devices to ensure legitimate network access, while device authorization determines the specific actions and resources each authenticated device is permitted to use. Authorization plays a critical role in device management by enforcing granular access controls, minimizing security risks, and preventing unauthorized operations that could compromise the IoT ecosystem. Implementing robust authorization frameworks enables scalable, secure management of diverse connected devices in complex IoT environments.
Common Protocols for Device Authentication
Device authentication in the Internet of Things (IoT) ensures that a device's identity is verified before granting access, using common protocols such as OAuth 2.0, MQTT with TLS, and DTLS. These protocols facilitate secure exchanges through cryptographic techniques, preventing unauthorized device entry and ensuring data integrity. In contrast, device authorization determines the specific resources or services an authenticated device can access, often relying on Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) after authentication.
Techniques and Standards for Device Authorization
Device authorization in the Internet of Things (IoT) involves granting specific permissions to authenticated devices, using standards like OAuth 2.0 and User-Managed Access (UMA) to manage access rights securely. Techniques such as token-based authorization and attribute-based access control (ABAC) ensure devices operate within defined scopes, minimizing unauthorized interactions. Implementing these methods strengthens security frameworks by enforcing granular control over device capabilities and data exchange.
Challenges in Implementing Authentication vs Authorization
Implementing device authentication in the Internet of Things (IoT) faces challenges like managing diverse device identities and ensuring secure key distribution across constrained devices. Device authorization encounters difficulties in enforcing fine-grained access control and dynamically adapting permissions in large, heterogeneous IoT ecosystems. Both processes require scalable, interoperable frameworks to maintain security without hindering device performance or user experience.
Best Practices for Securing IoT Devices
Device authentication verifies the identity of IoT devices using methods such as digital certificates, biometrics, or cryptographic keys to prevent unauthorized access. Device authorization controls the level of access granted to authenticated devices, ensuring they perform only permitted actions within the IoT network. Best practices for securing IoT devices include implementing multi-factor authentication, using role-based access control, regularly updating firmware, and employing end-to-end encryption to safeguard data integrity and confidentiality.
Future Trends in IoT Authentication and Authorization
Future trends in IoT authentication emphasize decentralized approaches, leveraging blockchain technology to enhance device authentication by providing tamper-proof identity verification. Device authorization is evolving through adaptive, context-aware policies that dynamically manage permissions based on real-time user behavior and environmental factors. Integrating AI-driven risk assessment enables proactive detection of anomalous device activities, strengthening both authentication and authorization frameworks in large-scale IoT deployments.
Device authentication vs Device authorization Infographic
 techiny.com
techiny.com