Device authentication in the Internet of Things (IoT) ensures that connected devices securely identify themselves to the network, preventing unauthorized access and potential cyberattacks. User authentication, on the other hand, verifies the identity of individuals accessing IoT systems, enabling personalized and secure interactions with smart devices. Effective IoT security requires a combination of both device and user authentication to maintain data integrity and protect against breaches.
Table of Comparison
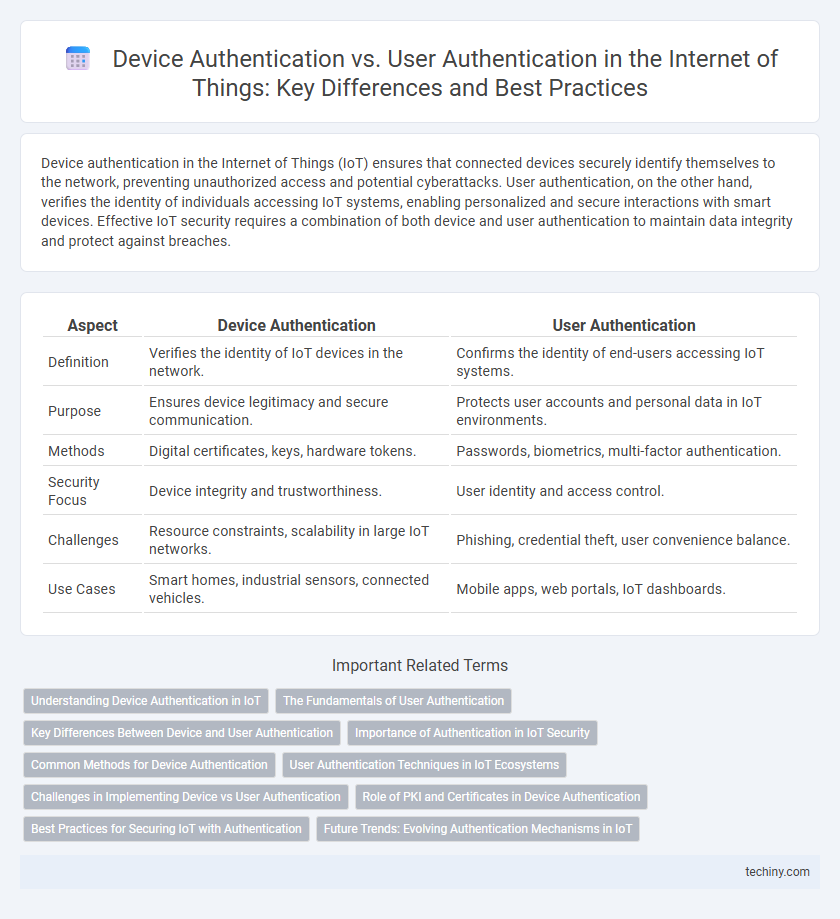
| Aspect | Device Authentication | User Authentication |
|---|---|---|
| Definition | Verifies the identity of IoT devices in the network. | Confirms the identity of end-users accessing IoT systems. |
| Purpose | Ensures device legitimacy and secure communication. | Protects user accounts and personal data in IoT environments. |
| Methods | Digital certificates, keys, hardware tokens. | Passwords, biometrics, multi-factor authentication. |
| Security Focus | Device integrity and trustworthiness. | User identity and access control. |
| Challenges | Resource constraints, scalability in large IoT networks. | Phishing, credential theft, user convenience balance. |
| Use Cases | Smart homes, industrial sensors, connected vehicles. | Mobile apps, web portals, IoT dashboards. |
Understanding Device Authentication in IoT
Device authentication in IoT ensures that only authorized devices can access the network, preventing unauthorized hardware from connecting and compromising data integrity. It involves the use of cryptographic techniques such as digital certificates, hardware security modules, and secure key storage to verify device identities before granting access. Strong device authentication protocols safeguard IoT ecosystems by enabling secure communication among millions of interconnected sensors and appliances, distinct from user authentication which validates individual human access rights.
The Fundamentals of User Authentication
User authentication in the Internet of Things (IoT) establishes the identity of individuals accessing devices or services, ensuring secure interactions and data protection. It relies on methods such as passwords, biometrics, and multi-factor authentication to verify users before granting access. Unlike device authentication, which verifies the device itself, user authentication prioritizes validating human users to prevent unauthorized control and data breaches.
Key Differences Between Device and User Authentication
Device authentication in the Internet of Things (IoT) primarily verifies the identity and integrity of connected devices using cryptographic keys, certificates, or hardware-based security modules to ensure secure communication. User authentication focuses on validating individual users through passwords, biometrics, or multi-factor authentication to control access to IoT applications and data. A key difference lies in device authentication enabling automated, scalable security for numerous endpoints, whereas user authentication centers on verifying identity for personalized access and activity tracking.
Importance of Authentication in IoT Security
Device authentication in IoT ensures that only authorized hardware can access the network, preventing counterfeit or compromised devices from infiltrating the system. User authentication protects sensitive data by verifying the identity of individuals interacting with IoT devices, mitigating the risk of unauthorized access and data breaches. Robust authentication mechanisms are vital in maintaining the integrity, confidentiality, and availability of IoT ecosystems, thereby enhancing overall security posture.
Common Methods for Device Authentication
Common methods for device authentication in the Internet of Things (IoT) include digital certificates, pre-shared keys (PSK), and hardware-based security modules such as Trusted Platform Modules (TPM). Digital certificates leverage Public Key Infrastructure (PKI) to ensure device identity verification through cryptographic keys, enabling secure communication between devices and servers. These methods provide robust protection by preventing unauthorized device access, enhancing overall IoT network security.
User Authentication Techniques in IoT Ecosystems
User authentication techniques in IoT ecosystems leverage multi-factor authentication, biometric verification, and behavior-based authentication to ensure secure access to connected devices and data. These methods utilize contextual data such as device location, usage patterns, and biometric traits to enhance identity verification beyond traditional passwords. Implementing adaptive authentication mechanisms reduces unauthorized access risks and strengthens overall IoT security frameworks.
Challenges in Implementing Device vs User Authentication
Implementing device authentication in the Internet of Things (IoT) faces challenges such as limited device computational power, diverse communication protocols, and the need for scalable key management systems. User authentication struggles with ensuring secure yet user-friendly methods across multiple devices, often complicated by varying user behaviors and privacy concerns. Both approaches require robust security frameworks to prevent unauthorized access and maintain data integrity in complex IoT ecosystems.
Role of PKI and Certificates in Device Authentication
Public Key Infrastructure (PKI) plays a critical role in device authentication within the Internet of Things (IoT) by enabling secure issuance and management of digital certificates that uniquely identify devices. Certificates serve as cryptographic credentials that validate the authenticity of devices, preventing unauthorized access and ensuring secure communication in an IoT ecosystem. Unlike user authentication, which verifies human identities, device authentication relies on PKI to establish trust between machines by leveraging asymmetric encryption and certificate authorities.
Best Practices for Securing IoT with Authentication
Device authentication in IoT ensures that each connected device is verified using unique cryptographic credentials like X.509 certificates or hardware-based secure elements, preventing unauthorized devices from accessing the network. User authentication complements this by enforcing multi-factor authentication (MFA), biometric verification, or OAuth protocols to confirm the identity of users managing or interacting with IoT devices. Implementing mutual authentication between users and devices, combined with continuous monitoring and secure key management, establishes a robust security posture essential for protecting IoT ecosystems against unauthorized access and cyber threats.
Future Trends: Evolving Authentication Mechanisms in IoT
Emerging trends in IoT emphasize the integration of device authentication with advanced cryptographic techniques, such as blockchain and decentralized identifiers, to enhance security and scalability. User authentication is evolving towards multi-factor and biometric solutions, leveraging AI-driven behavioral analytics for continuous verification. Future IoT environments will prioritize adaptive, context-aware authentication mechanisms that dynamically respond to risk levels and user-device interactions.
Device Authentication vs User Authentication Infographic
 techiny.com
techiny.com