Device discovery in the Internet of Things (IoT) involves identifying and locating devices within a network to enable communication and data exchange. Device authentication ensures that only authorized devices gain access, protecting the network from unauthorized intrusions and data breaches. Together, these processes maintain secure and efficient IoT environments by balancing connectivity with robust security protocols.
Table of Comparison
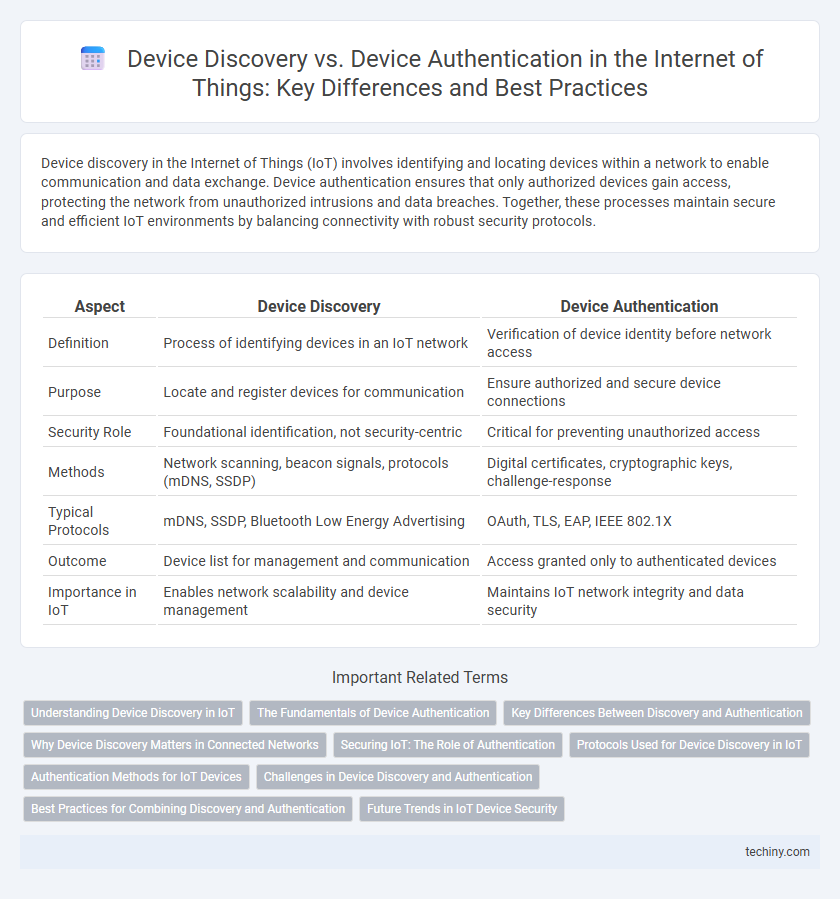
| Aspect | Device Discovery | Device Authentication |
|---|---|---|
| Definition | Process of identifying devices in an IoT network | Verification of device identity before network access |
| Purpose | Locate and register devices for communication | Ensure authorized and secure device connections |
| Security Role | Foundational identification, not security-centric | Critical for preventing unauthorized access |
| Methods | Network scanning, beacon signals, protocols (mDNS, SSDP) | Digital certificates, cryptographic keys, challenge-response |
| Typical Protocols | mDNS, SSDP, Bluetooth Low Energy Advertising | OAuth, TLS, EAP, IEEE 802.1X |
| Outcome | Device list for management and communication | Access granted only to authenticated devices |
| Importance in IoT | Enables network scalability and device management | Maintains IoT network integrity and data security |
Understanding Device Discovery in IoT
Device discovery in IoT is the process by which a network identifies and locates devices to enable communication and data exchange, using protocols such as mDNS, SSDP, or Bluetooth Low Energy. This phase focuses on recognizing devices' presence without verifying their identity, allowing seamless integration and scalability in dynamic environments. Understanding device discovery is crucial for efficient network management, ensuring devices can be detected promptly before proceeding to the secure step of device authentication.
The Fundamentals of Device Authentication
Device authentication is a critical security process in the Internet of Things (IoT) that verifies the identity of devices before granting network access. Unlike device discovery, which identifies devices available for connection, authentication ensures that only trusted devices can communicate, protecting IoT ecosystems from unauthorized access and potential cyber threats. Effective device authentication mechanisms include cryptographic protocols, digital certificates, and secure key exchanges to maintain data integrity and confidentiality across connected devices.
Key Differences Between Discovery and Authentication
Device discovery in the Internet of Things (IoT) refers to the process of identifying and locating devices within a network, enabling communication initiation. Device authentication, on the other hand, verifies the identity of devices to ensure secure access and prevent unauthorized connections. The key difference lies in discovery enabling device recognition and network integration, while authentication enforces security protocols to protect data integrity and privacy.
Why Device Discovery Matters in Connected Networks
Device discovery in connected IoT networks enables seamless identification and integration of new devices, ensuring efficient communication and resource allocation. Without accurate device discovery, networks risk inefficiencies, increased latency, and security vulnerabilities due to unidentified or rogue devices. Effective device discovery lays the foundation for robust device authentication, safeguarding network integrity and enabling scalable IoT deployments.
Securing IoT: The Role of Authentication
Device discovery in IoT involves identifying and locating devices within a network, enabling communication and data exchange, while device authentication ensures that these devices are verified and trusted before granting access to sensitive systems. Securing IoT heavily relies on robust authentication mechanisms such as digital certificates, biometrics, or token-based systems to prevent unauthorized access and mitigate security risks associated with device impersonation. Effective device authentication establishes a trusted environment, safeguarding IoT networks from cyber threats and enhancing overall system integrity.
Protocols Used for Device Discovery in IoT
Device discovery in IoT commonly utilizes protocols such as mDNS, SSDP, and CoAP for efficient identification and communication setup between devices. These protocols enable automatic detection and address resolution within local networks, facilitating seamless integration without prior manual configuration. Device authentication, by contrast, involves security-focused protocols like OAuth, DTLS, and TLS, which ensure that discovered devices are verified and authorized before exchanging data.
Authentication Methods for IoT Devices
Device authentication in IoT relies on methods such as mutual authentication, token-based access, and public key infrastructure (PKI) to ensure secure communication between devices. Device discovery protocols identify and register new devices on the network but do not verify their identities, making authentication crucial to prevent unauthorized access. Robust authentication methods, including biometrics, certificate-based verification, and lightweight cryptographic algorithms, enhance security and trust in IoT ecosystems.
Challenges in Device Discovery and Authentication
Device discovery in the Internet of Things faces challenges such as scalability issues due to the exponential growth of connected devices, heterogeneous protocols causing interoperability problems, and latency constraints impacting real-time identification. Device authentication struggles with securing diverse device types that often have limited computational power, making it difficult to implement robust cryptographic methods while ensuring low energy consumption. Both processes require advanced solutions to balance security, privacy, and performance across vast, dynamic IoT networks.
Best Practices for Combining Discovery and Authentication
Effective integration of device discovery and device authentication is crucial for secure Internet of Things (IoT) deployments, ensuring unauthorized devices are identified and blocked promptly. Best practices include leveraging mutual authentication protocols during the discovery phase to validate device identities before network access, and employing lightweight cryptographic methods to accommodate resource-constrained IoT devices. Implementing continuous authentication mechanisms alongside discovery processes enhances security posture by dynamically verifying device trustworthiness throughout its lifecycle.
Future Trends in IoT Device Security
Future trends in IoT device security emphasize advanced device discovery methods utilizing AI-driven network mapping to identify and categorize devices in real-time, enhancing visibility and reducing unauthorized access risks. Device authentication is increasingly adopting decentralized approaches such as blockchain-based identity management and zero-trust architectures to ensure robust, scalable, and tamper-resistant verification. The integration of machine learning algorithms for anomaly detection further strengthens IoT security by continuously validating device behavior post-authentication, creating adaptive defenses against emerging cyber threats.
Device discovery vs Device authentication Infographic
 techiny.com
techiny.com