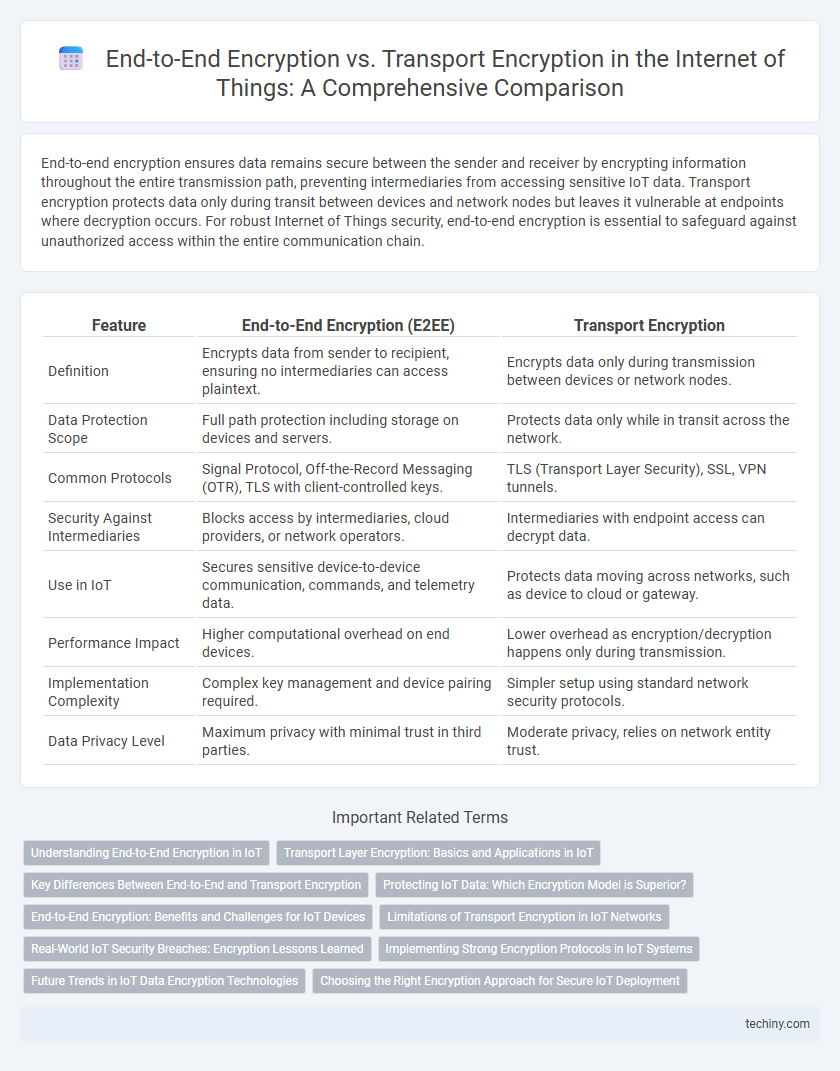
End-to-end encryption ensures data remains secure between the sender and receiver by encrypting information throughout the entire transmission path, preventing intermediaries from accessing sensitive IoT data. Transport encryption protects data only during transit between devices and network nodes but leaves it vulnerable at endpoints where decryption occurs. For robust Internet of Things security, end-to-end encryption is essential to safeguard against unauthorized access within the entire communication chain.
Table of Comparison
| Feature | End-to-End Encryption (E2EE) | Transport Encryption |
|---|---|---|
| Definition | Encrypts data from sender to recipient, ensuring no intermediaries can access plaintext. | Encrypts data only during transmission between devices or network nodes. |
| Data Protection Scope | Full path protection including storage on devices and servers. | Protects data only while in transit across the network. |
| Common Protocols | Signal Protocol, Off-the-Record Messaging (OTR), TLS with client-controlled keys. | TLS (Transport Layer Security), SSL, VPN tunnels. |
| Security Against Intermediaries | Blocks access by intermediaries, cloud providers, or network operators. | Intermediaries with endpoint access can decrypt data. |
| Use in IoT | Secures sensitive device-to-device communication, commands, and telemetry data. | Protects data moving across networks, such as device to cloud or gateway. |
| Performance Impact | Higher computational overhead on end devices. | Lower overhead as encryption/decryption happens only during transmission. |
| Implementation Complexity | Complex key management and device pairing required. | Simpler setup using standard network security protocols. |
| Data Privacy Level | Maximum privacy with minimal trust in third parties. | Moderate privacy, relies on network entity trust. |
Understanding End-to-End Encryption in IoT
End-to-end encryption (E2EE) in IoT ensures data confidentiality by encrypting information directly on the device and decrypting it only at the intended recipient's end, preventing intermediaries from accessing sensitive data. This method contrasts with transport encryption, which secures data only during transmission but allows potential exposure on intermediate nodes or servers. E2EE is critical for protecting IoT ecosystems, including smart home devices and industrial sensors, from interception and unauthorized access throughout the entire communication path.
Transport Layer Encryption: Basics and Applications in IoT
Transport layer encryption, primarily implemented through protocols like TLS, secures data in transit between IoT devices and servers by encrypting communication channels. This encryption method ensures confidentiality and integrity against eavesdropping and tampering during data transmission across networks. In IoT applications, transport encryption is critical for protecting sensitive information such as sensor readings and control commands, especially over public or untrusted networks.
Key Differences Between End-to-End and Transport Encryption
End-to-end encryption (E2EE) secures data from the sender to the recipient, ensuring that only the communicating parties can decrypt the information, while transport encryption protects data only during transmission between network nodes, typically using TLS or SSL protocols. E2EE prevents intermediaries, including service providers, from accessing plaintext data, whereas transport encryption leaves data exposed at endpoints where it is decrypted and processed. Consequently, E2EE offers a higher level of confidentiality essential for sensitive IoT communications, while transport encryption focuses primarily on safeguarding data in transit.
Protecting IoT Data: Which Encryption Model is Superior?
End-to-end encryption (E2EE) ensures data is encrypted on the IoT device and decrypted only by the intended recipient, providing robust protection against interception and unauthorized access across the entire communication path. Transport encryption, such as TLS, secures data during transmission between IoT devices and servers but leaves data vulnerable to exposure at the endpoints. For safeguarding sensitive IoT data, end-to-end encryption is superior, minimizing risks inherent in centralized data processing and enhancing overall security in connected environments.
End-to-End Encryption: Benefits and Challenges for IoT Devices
End-to-end encryption (E2EE) in IoT devices ensures data confidentiality by encrypting information directly on the source device and decrypting only on the recipient device, preventing intermediaries from accessing sensitive data. This approach enhances security against interception and tampering but poses challenges such as increased computational demands, potential latency, and key management complexities in resource-constrained IoT environments. Implementing E2EE necessitates careful balancing between robust security measures and the limited processing, memory, and power capabilities of IoT devices.
Limitations of Transport Encryption in IoT Networks
Transport encryption secures data in transit between devices and servers but leaves endpoints vulnerable in IoT networks, exposing sensitive information to potential breaches. This limitation allows attackers to intercept or manipulate data once it reaches the device or cloud, undermining overall security. End-to-end encryption addresses this by ensuring data remains encrypted from the source device to the destination, preventing unauthorized access even within compromised transit channels.
Real-World IoT Security Breaches: Encryption Lessons Learned
Real-world IoT security breaches highlight critical differences between end-to-end encryption (E2EE) and transport encryption in protecting data integrity. While transport encryption secures data in transit between devices and servers, E2EE ensures data remains encrypted throughout its entire journey, preventing interception even by intermediary network nodes. Lessons learned reveal that solely relying on transport encryption leaves IoT systems vulnerable to insider attacks and upstream tampering, emphasizing the necessity of implementing robust end-to-end encryption protocols for comprehensive security.
Implementing Strong Encryption Protocols in IoT Systems
Implementing strong encryption protocols in IoT systems requires analyzing the differences between end-to-end encryption (E2EE) and transport encryption. E2EE ensures data remains encrypted from the source device to the destination, minimizing the risk of interception within intermediate nodes, while transport encryption secures data only during transmission between devices and gateways. Prioritizing E2EE in IoT deployments enhances data confidentiality and integrity across diverse network layers, critical for safeguarding sensitive information in interconnected smart environments.
Future Trends in IoT Data Encryption Technologies
End-to-end encryption (E2EE) ensures data remains encrypted from the source device to the final recipient, preventing unauthorized access at any intermediate point, a critical feature for securing IoT ecosystems with diverse interconnected devices. Transport encryption, typically using protocols like TLS, secures data only during transmission between nodes but leaves it vulnerable at endpoints, highlighting limitations in protecting IoT data confidentiality. Future trends in IoT data encryption emphasize hybrid models combining E2EE with lightweight cryptographic algorithms, enabling robust security without compromising the resource constraints of IoT devices, alongside advancements in quantum-resistant encryption to future-proof data integrity against emerging cyber threats.
Choosing the Right Encryption Approach for Secure IoT Deployment
End-to-end encryption (E2EE) ensures data remains encrypted from the IoT device to the final recipient, preventing interception at any intermediate node, which is critical for sensitive IoT applications like healthcare and industrial automation. Transport encryption, such as TLS, secures data only during transmission between points but exposes data at endpoints, posing risks in environments with vulnerable devices. Selecting the right encryption approach depends on the IoT deployment's security requirements, device capabilities, and network architecture to balance robust protection with performance constraints.
End-to-end encryption vs Transport encryption Infographic
 techiny.com
techiny.com