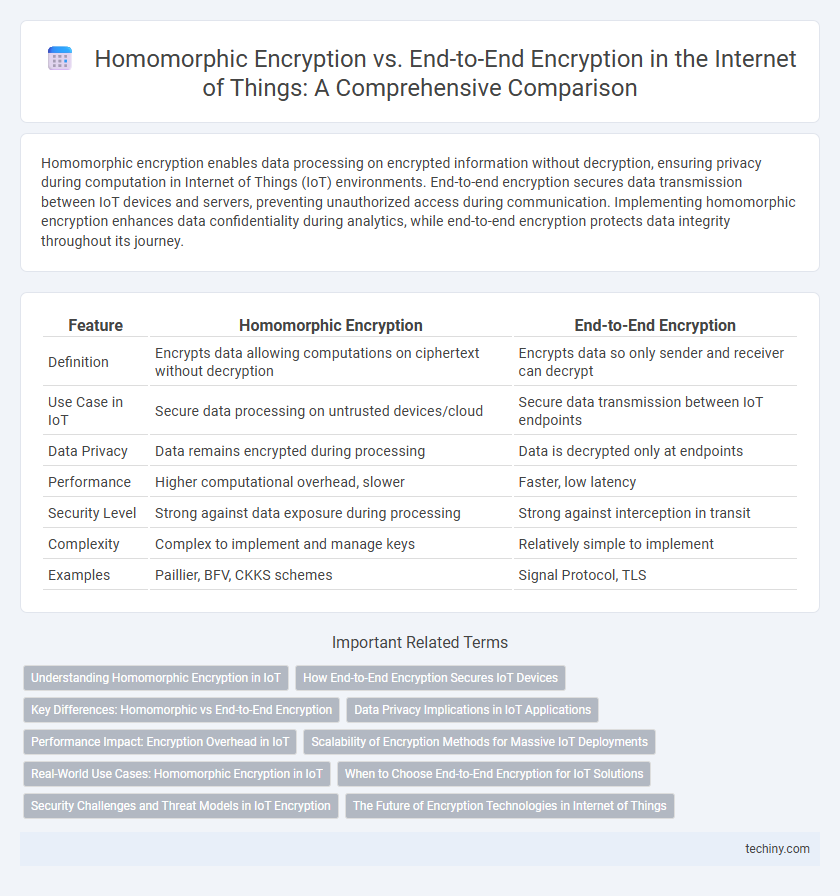
Homomorphic encryption enables data processing on encrypted information without decryption, ensuring privacy during computation in Internet of Things (IoT) environments. End-to-end encryption secures data transmission between IoT devices and servers, preventing unauthorized access during communication. Implementing homomorphic encryption enhances data confidentiality during analytics, while end-to-end encryption protects data integrity throughout its journey.
Table of Comparison
| Feature | Homomorphic Encryption | End-to-End Encryption |
|---|---|---|
| Definition | Encrypts data allowing computations on ciphertext without decryption | Encrypts data so only sender and receiver can decrypt |
| Use Case in IoT | Secure data processing on untrusted devices/cloud | Secure data transmission between IoT endpoints |
| Data Privacy | Data remains encrypted during processing | Data is decrypted only at endpoints |
| Performance | Higher computational overhead, slower | Faster, low latency |
| Security Level | Strong against data exposure during processing | Strong against interception in transit |
| Complexity | Complex to implement and manage keys | Relatively simple to implement |
| Examples | Paillier, BFV, CKKS schemes | Signal Protocol, TLS |
Understanding Homomorphic Encryption in IoT
Homomorphic encryption enables IoT devices to perform computations directly on encrypted data without needing to decrypt it, preserving privacy and security throughout data processing. This approach contrasts with end-to-end encryption, which secures data only during transmission but requires decryption for processing at endpoints, potentially exposing sensitive information. Implementing homomorphic encryption in IoT enhances secure data analytics and real-time decision-making while mitigating risks associated with data exposure.
How End-to-End Encryption Secures IoT Devices
End-to-end encryption secures IoT devices by ensuring that data transmitted between devices and servers remains encrypted throughout the communication process, preventing unauthorized access or interception. This method encrypts the data at the source device and only decrypts it at the intended recipient, safeguarding sensitive information from cyberattacks and eavesdropping. Compared to homomorphic encryption, which allows computation on encrypted data but is computationally intensive, end-to-end encryption offers efficient, robust protection tailored for the real-time, resource-constrained nature of IoT ecosystems.
Key Differences: Homomorphic vs End-to-End Encryption
Homomorphic encryption enables data processing and analysis on encrypted information without decrypting it, preserving privacy in IoT devices by allowing computations on ciphertext. End-to-end encryption secures data transmission by encrypting information on the sender's device and decrypting only on the receiver's device, ensuring confidentiality across the communication channel. The key difference lies in homomorphic encryption's capability to perform secure data operations on encrypted data, while end-to-end encryption primarily protects data in transit from interception.
Data Privacy Implications in IoT Applications
Homomorphic encryption enables computation on encrypted IoT data without decryption, preserving data confidentiality throughout processing and reducing exposure to cyber threats. End-to-end encryption secures data during transmission between IoT devices and servers, preventing interception but requires decryption for processing, potentially exposing sensitive information. The choice between these encryption methods impacts IoT data privacy by balancing operational efficiency, security risks, and compliance with data protection regulations.
Performance Impact: Encryption Overhead in IoT
Homomorphic encryption introduces significant computational overhead in IoT devices due to its complex mathematical operations, often leading to latency and increased energy consumption unsuitable for resource-constrained environments. End-to-end encryption, by contrast, offers more efficient performance with lower processing demands, enabling faster data transmission and reduced energy usage across IoT networks. Evaluating encryption overhead is critical for optimizing security implementation while maintaining device responsiveness and battery life in Internet of Things applications.
Scalability of Encryption Methods for Massive IoT Deployments
Homomorphic encryption enables secure data processing on encrypted information without decryption, offering scalability for massive IoT deployments by minimizing data exposure risks and reducing the need for constant data decryption at edge devices. End-to-end encryption ensures data confidentiality between IoT nodes and central servers but can introduce latency and computational overhead that hampers scalability in large-scale networks with numerous devices. Efficient key management and lightweight cryptographic algorithms remain critical for maintaining scalability and performance in extensive IoT ecosystems using either encryption method.
Real-World Use Cases: Homomorphic Encryption in IoT
Homomorphic encryption enables IoT devices to perform computations on encrypted data without decrypting it, preserving user privacy in sensitive applications like healthcare monitoring and smart grids. Unlike end-to-end encryption, which secures data during transmission, homomorphic encryption allows cloud-based analytics and machine learning on encrypted sensor data without exposing raw information. Real-world use cases include predictive maintenance in industrial IoT and secure data aggregation in connected vehicles, where data confidentiality and operational efficiency are critical.
When to Choose End-to-End Encryption for IoT Solutions
End-to-end encryption is ideal for IoT solutions requiring secure communication between devices and users without intermediary decryption, ensuring data privacy even across untrusted networks. This method suits scenarios where real-time data integrity and confidentiality are critical, such as in healthcare monitoring or smart home systems. Choosing end-to-end encryption protects sensitive IoT data from interception during transmission, reducing the risk of breaches in distributed device environments.
Security Challenges and Threat Models in IoT Encryption
Homomorphic encryption enables secure computation on encrypted IoT data without decryption, mitigating risks from compromised intermediaries and insiders, but it faces challenges such as high computational overhead and limited algorithm support. End-to-end encryption ensures data confidentiality between IoT devices and endpoints, protecting against eavesdropping and man-in-the-middle attacks, yet it struggles with key management complexity and vulnerability in resource-constrained environments. Both encryption methods must address evolving threat models including side-channel attacks, compromised nodes, and scalability issues to maintain robust IoT security frameworks.
The Future of Encryption Technologies in Internet of Things
Homomorphic encryption enables processing of encrypted IoT data without decryption, preserving privacy while supporting advanced analytics in smart environments. End-to-end encryption ensures secure communication channels between IoT devices and servers, protecting data integrity during transmission. Combining these technologies promises a future where IoT systems achieve robust security, seamless data utility, and resilience against emerging cyber threats.
Homomorphic encryption vs End-to-end encryption Infographic
 techiny.com
techiny.com