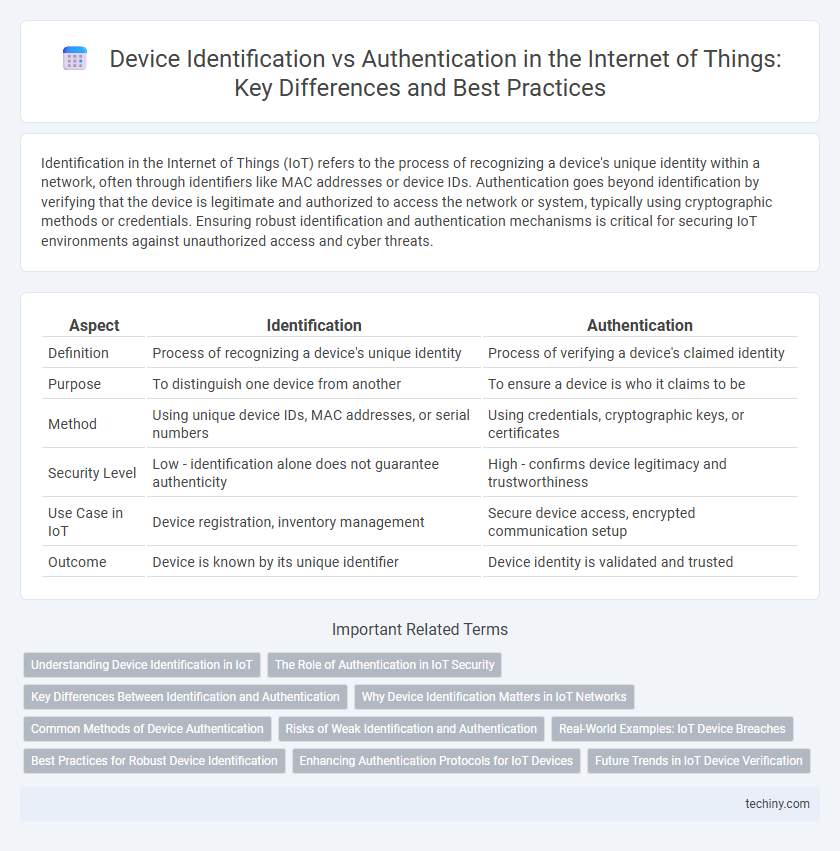
Identification in the Internet of Things (IoT) refers to the process of recognizing a device's unique identity within a network, often through identifiers like MAC addresses or device IDs. Authentication goes beyond identification by verifying that the device is legitimate and authorized to access the network or system, typically using cryptographic methods or credentials. Ensuring robust identification and authentication mechanisms is critical for securing IoT environments against unauthorized access and cyber threats.
Table of Comparison
| Aspect | Identification | Authentication |
|---|---|---|
| Definition | Process of recognizing a device's unique identity | Process of verifying a device's claimed identity |
| Purpose | To distinguish one device from another | To ensure a device is who it claims to be |
| Method | Using unique device IDs, MAC addresses, or serial numbers | Using credentials, cryptographic keys, or certificates |
| Security Level | Low - identification alone does not guarantee authenticity | High - confirms device legitimacy and trustworthiness |
| Use Case in IoT | Device registration, inventory management | Secure device access, encrypted communication setup |
| Outcome | Device is known by its unique identifier | Device identity is validated and trusted |
Understanding Device Identification in IoT
Device identification in IoT involves uniquely recognizing each device within a network using identifiers such as MAC addresses, IP addresses, or device fingerprints, enabling accurate device management and communication. This process ensures that devices are correctly cataloged and tracked but does not verify the legitimacy or trustworthiness of the device. Effective identification is crucial for enabling subsequent authentication protocols that confirm device authenticity and secure IoT ecosystems against unauthorized access.
The Role of Authentication in IoT Security
Authentication in IoT security verifies the identity of devices, ensuring only authorized entities access the network, which protects against unauthorized intrusion and data breaches. Unlike identification, which simply recognizes a device, authentication involves robust techniques such as cryptographic keys, biometrics, or multi-factor methods to validate legitimacy. Effective authentication mechanisms are critical to safeguarding sensitive data, maintaining system integrity, and preventing malicious attacks in IoT ecosystems.
Key Differences Between Identification and Authentication
Identification in the Internet of Things (IoT) involves recognizing a device by its unique identifier, such as a device ID or MAC address, to distinguish it from other devices within a network. Authentication confirms the legitimacy of the device by verifying credentials like digital certificates, cryptographic keys, or tokens to ensure authorized access. The key difference lies in identification being a recognition process, whereas authentication is a security measure that validates the device's identity before granting network resources.
Why Device Identification Matters in IoT Networks
Device identification in IoT networks is crucial for ensuring proper device management and security by uniquely recognizing each connected device to prevent unauthorized access and cyber threats. Accurate identification enables efficient network monitoring, asset tracking, and seamless device interoperability across diverse IoT ecosystems. Without reliable device identification, authentication processes become vulnerable, increasing risks of data breaches and operational disruptions.
Common Methods of Device Authentication
Device authentication in the Internet of Things (IoT) commonly relies on techniques like digital certificates, pre-shared keys, and OAuth protocols to verify device identities securely. Public Key Infrastructure (PKI) enables robust authentication by using asymmetric cryptography and certificate authorities, while lightweight methods like symmetric keys are favored for resource-constrained devices. Biometric-based and hardware security modules (HSM) also enhance authentication by providing tamper-resistant identity verification.
Risks of Weak Identification and Authentication
Weak identification and authentication in Internet of Things (IoT) devices create significant security vulnerabilities, exposing networks to unauthorized access and potential data breaches. Attackers can exploit insufficient identity verification to impersonate devices, leading to unauthorized control, data manipulation, or denial of service attacks. Implementing robust multi-factor authentication and unique device identifiers mitigates risks associated with identity spoofing and enhances overall IoT ecosystem security.
Real-World Examples: IoT Device Breaches
IoT device breaches often occur due to weak identification or authentication protocols, such as default or easily guessable credentials in smart home devices like cameras and thermostats. For example, the Mirai botnet exploited insecure IoT devices by identifying them through open ports and authenticating using factory default usernames and passwords. Strengthening unique device identification and implementing robust multi-factor authentication significantly mitigates risks of unauthorized access and large-scale IoT network compromises.
Best Practices for Robust Device Identification
Robust device identification in the Internet of Things (IoT) relies on unique, immutable identifiers such as MAC addresses or hardware-based IDs to ensure precise device recognition. Implementing multi-factor authentication protocols alongside digital certificates strengthens security by validating the device's legitimacy beyond mere identification. Employing secure element hardware and regularly updating firmware mitigates risks related to spoofing and unauthorized access, establishing a reliable foundation for device trustworthiness in IoT ecosystems.
Enhancing Authentication Protocols for IoT Devices
Enhancing authentication protocols for IoT devices involves implementing multi-factor and biometric methods to verify device identities beyond simple identification. Utilizing cryptographic techniques such as public-key infrastructure (PKI) and blockchain-based authentication strengthens security against unauthorized access. Continuous monitoring and adaptive authentication frameworks help detect anomalies and ensure only legitimate devices communicate within IoT networks.
Future Trends in IoT Device Verification
Future trends in IoT device verification emphasize the integration of decentralized identification methods, such as blockchain-based digital identities, to enhance device provenance and trustworthiness. Advanced authentication techniques leverage biometric data and AI-driven behavioral analysis to provide dynamic, context-aware security that adapts to evolving threats. The convergence of these innovations aims to establish robust, scalable verification frameworks essential for the growing complexity of interconnected IoT ecosystems.
Identification vs Authentication (of devices) Infographic
 techiny.com
techiny.com