IoT devices face distinct challenges in both physical security and cybersecurity, as physical tampering can lead to unauthorized access, while cyber threats exploit vulnerabilities in device software or communication protocols. Ensuring robust encryption, secure authentication, and tamper-resistant hardware is critical to protect sensitive data and maintain device integrity. Balancing these security measures helps mitigate risks from both physical breaches and cyberattacks in interconnected IoT environments.
Table of Comparison
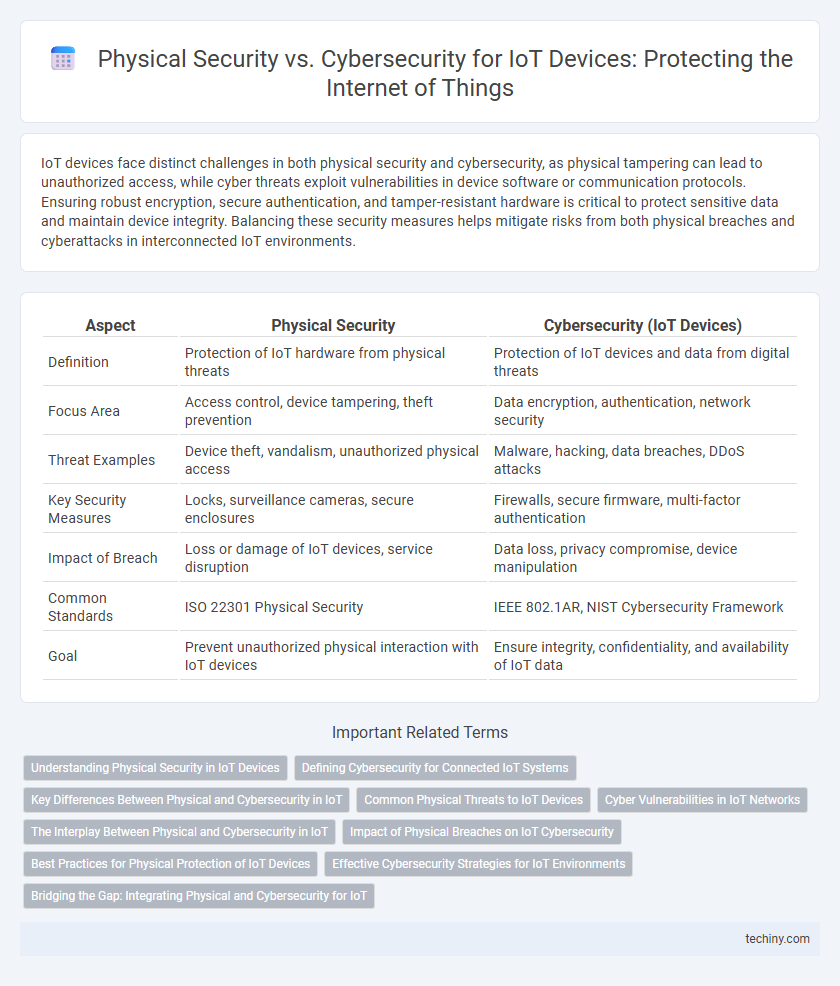
| Aspect | Physical Security | Cybersecurity (IoT Devices) |
|---|---|---|
| Definition | Protection of IoT hardware from physical threats | Protection of IoT devices and data from digital threats |
| Focus Area | Access control, device tampering, theft prevention | Data encryption, authentication, network security |
| Threat Examples | Device theft, vandalism, unauthorized physical access | Malware, hacking, data breaches, DDoS attacks |
| Key Security Measures | Locks, surveillance cameras, secure enclosures | Firewalls, secure firmware, multi-factor authentication |
| Impact of Breach | Loss or damage of IoT devices, service disruption | Data loss, privacy compromise, device manipulation |
| Common Standards | ISO 22301 Physical Security | IEEE 802.1AR, NIST Cybersecurity Framework |
| Goal | Prevent unauthorized physical interaction with IoT devices | Ensure integrity, confidentiality, and availability of IoT data |
Understanding Physical Security in IoT Devices
Physical security in IoT devices involves protecting hardware components from theft, tampering, or environmental damage that could compromise device functionality and data integrity. Implementing tamper-evident seals, secure enclosures, and access controls prevents unauthorized physical access and potential hardware manipulation. Understanding these measures is crucial for maintaining comprehensive security within IoT ecosystems, where physical vulnerabilities can lead to significant cybersecurity risks.
Defining Cybersecurity for Connected IoT Systems
Cybersecurity for connected IoT systems involves protecting data, devices, and networks from unauthorized access and attacks that exploit vulnerabilities inherent to interconnected devices. It encompasses encryption, authentication protocols, and continuous monitoring to ensure data integrity and confidentiality across diverse IoT endpoints. Prioritizing cybersecurity over physical security is crucial as cyber attacks can remotely compromise IoT devices, leading to broader systemic risks beyond physical tampering.
Key Differences Between Physical and Cybersecurity in IoT
Physical security in IoT focuses on safeguarding devices and infrastructure from tangible threats such as theft, tampering, and environmental damage, including secure enclosures and access controls. Cybersecurity in IoT addresses protection against digital threats like hacking, malware, and data breaches, emphasizing encryption, authentication protocols, and real-time network monitoring. Key differences include the nature of threats--physical versus digital--and the distinct mitigation strategies required for device integrity and data confidentiality within interconnected IoT ecosystems.
Common Physical Threats to IoT Devices
IoT devices face common physical threats such as tampering, theft, and environmental damage, which can disrupt device functionality and compromise data integrity. Physical access allows attackers to manipulate hardware components or introduce malicious code directly. Securing IoT devices requires resilient enclosures, tamper-evident mechanisms, and strategic placement to mitigate risks from unauthorized physical interference.
Cyber Vulnerabilities in IoT Networks
Cyber vulnerabilities in IoT networks often arise from weak authentication protocols, outdated firmware, and insecure communication channels, exposing devices to unauthorized access and data breaches. Exploitation of these weaknesses can lead to large-scale botnet attacks, data manipulation, and disruption of critical infrastructure. Securing IoT devices requires robust encryption, continuous monitoring, and timely patch management to mitigate cybersecurity risks inherent in interconnected systems.
The Interplay Between Physical and Cybersecurity in IoT
The interplay between physical security and cybersecurity in IoT devices is critical for comprehensive risk management, as physical tampering can enable cyber attacks while cyber vulnerabilities can compromise physical systems. Securing IoT devices requires integrated strategies that address hardware protections, such as tamper-resistant casings and secure boot protocols, alongside strong network encryption and intrusion detection. Understanding the convergence of these domains helps prevent breaches that exploit weaknesses in either physical access or software defenses, enhancing overall IoT system resilience.
Impact of Physical Breaches on IoT Cybersecurity
Physical breaches of IoT devices can lead to unauthorized access, firmware tampering, and device hijacking, significantly compromising overall cybersecurity. These intrusions often bypass traditional network defenses by exploiting hardware vulnerabilities, making it easier for attackers to implant malware or extract sensitive data. The intersection of physical security and cybersecurity highlights the critical need for tamper-resistant designs and secure hardware components to safeguard IoT ecosystems.
Best Practices for Physical Protection of IoT Devices
Securing IoT devices physically involves deploying tamper-resistant enclosures, restricting physical access using locked cabinets or secure mounting, and monitoring device environments with surveillance cameras or sensors. Best practices include regularly inspecting devices for signs of physical interference and employing hardware-based authentication methods such as Trusted Platform Modules (TPMs) to enhance device integrity. Implementing these measures mitigates risks from theft, vandalism, or unauthorized manipulation, complementing cybersecurity protocols to ensure comprehensive IoT device protection.
Effective Cybersecurity Strategies for IoT Environments
Effective cybersecurity strategies for IoT environments prioritize device authentication, encryption, and continuous monitoring to prevent unauthorized access and data breaches. Implementing network segmentation and regular firmware updates enhances protection against cyberattacks targeting interconnected devices. Leveraging AI-driven threat detection and response systems strengthens resilience against evolving IoT vulnerabilities and emerging cyber threats.
Bridging the Gap: Integrating Physical and Cybersecurity for IoT
Bridging the gap between physical security and cybersecurity is critical for protecting IoT devices from evolving threats that exploit both digital vulnerabilities and physical access points. Integrating biometric authentication, hardware encryption, and real-time intrusion detection systems ensures comprehensive protection across the entire IoT ecosystem. Implementing unified security frameworks enhances device resilience, minimizes attack surfaces, and safeguards sensitive data from cyber-physical exploitation.
Physical security vs Cybersecurity (IoT devices) Infographic
 techiny.com
techiny.com