AAA (Authentication, Authorization, and Accounting) is a framework that manages user identity and access privileges while tracking network usage for security and auditing. NAC (Network Access Control) enforces security policies by controlling device access based on compliance with pre-defined rules before granting network entry. While AAA focuses on user validation and activity logging, NAC emphasizes endpoint security and dynamic network enforcement to prevent unauthorized devices from connecting.
Table of Comparison
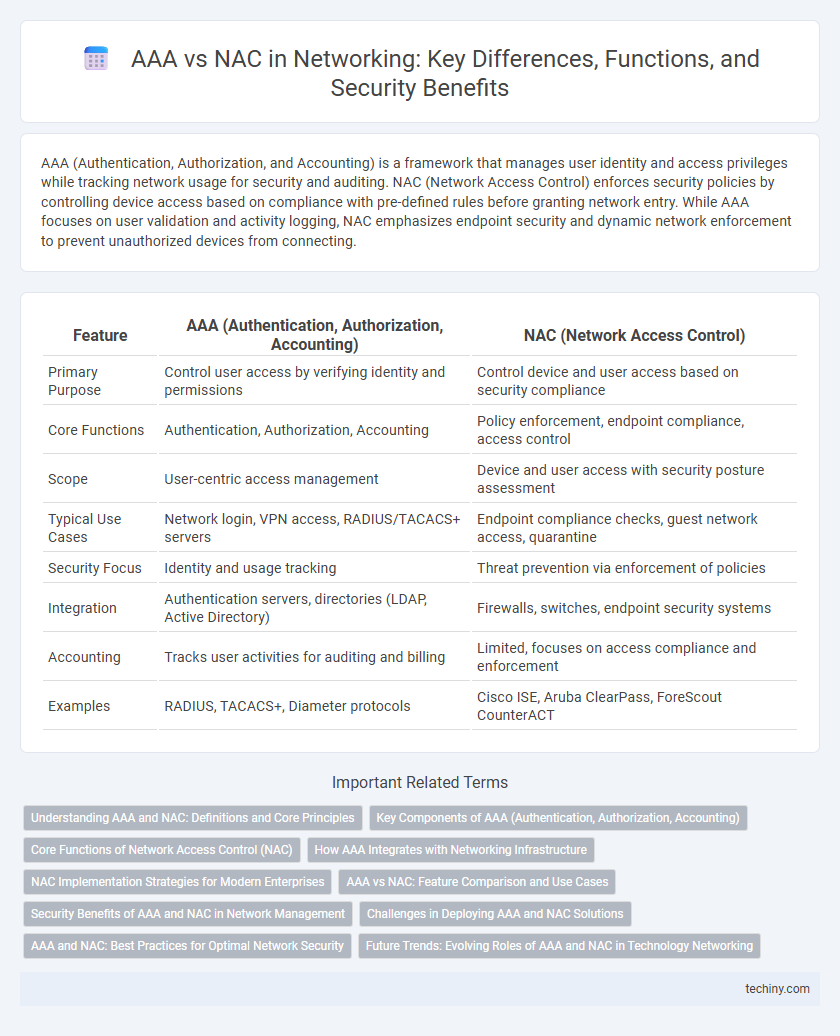
| Feature | AAA (Authentication, Authorization, Accounting) | NAC (Network Access Control) |
|---|---|---|
| Primary Purpose | Control user access by verifying identity and permissions | Control device and user access based on security compliance |
| Core Functions | Authentication, Authorization, Accounting | Policy enforcement, endpoint compliance, access control |
| Scope | User-centric access management | Device and user access with security posture assessment |
| Typical Use Cases | Network login, VPN access, RADIUS/TACACS+ servers | Endpoint compliance checks, guest network access, quarantine |
| Security Focus | Identity and usage tracking | Threat prevention via enforcement of policies |
| Integration | Authentication servers, directories (LDAP, Active Directory) | Firewalls, switches, endpoint security systems |
| Accounting | Tracks user activities for auditing and billing | Limited, focuses on access compliance and enforcement |
| Examples | RADIUS, TACACS+, Diameter protocols | Cisco ISE, Aruba ClearPass, ForeScout CounterACT |
Understanding AAA and NAC: Definitions and Core Principles
AAA (Authentication, Authorization, and Accounting) focuses on verifying user identities, granting appropriate access rights, and tracking user activities to enhance network security. NAC (Network Access Control) enforces security policies by controlling device access based on compliance status, ensuring that only authorized and compliant devices connect to the network. Both AAA and NAC are critical in establishing secure network environments, but AAA manages user credentials and permissions while NAC governs endpoint device behavior and network entry conditions.
Key Components of AAA (Authentication, Authorization, Accounting)
Authentication verifies user identities to ensure secure network access, while Authorization determines user permissions based on predefined policies. Accounting tracks user activities and resource usage for auditing and compliance. These core components of AAA provide a structured approach to managing and monitoring network security effectively.
Core Functions of Network Access Control (NAC)
Network Access Control (NAC) primarily enforces policies for device authentication, authorization, and endpoint compliance before granting network access, ensuring that only compliant and trusted devices connect. NAC systems provide real-time visibility into connected devices, enabling dynamic access control based on device posture, user identity, and network conditions. Unlike traditional AAA frameworks that focus solely on user credential validation, NAC integrates broader security policies including device health checks and remediation requirements to enhance network security.
How AAA Integrates with Networking Infrastructure
AAA (Authentication, Authorization, and Accounting) integrates with networking infrastructure by providing centralized user verification, access control, and activity monitoring within network devices such as switches, routers, and firewalls. Network Access Control (NAC) complements AAA by enforcing endpoint compliance policies before granting network access, ensuring only authenticated and authorized devices connect. Together, AAA protocols like RADIUS and TACACS+ work seamlessly with NAC systems to enhance network security and streamline access management across diverse network environments.
NAC Implementation Strategies for Modern Enterprises
Network Access Control (NAC) implementation strategies for modern enterprises emphasize integrating identity-based authentication, device compliance checks, and real-time threat intelligence to enforce dynamic access policies. Unlike traditional AAA (Authentication, Authorization, and Accounting) frameworks that focus primarily on user credentials, NAC solutions incorporate endpoint security posture and contextual information to enhance network visibility and automated remediation. Leveraging segmentation, continuous monitoring, and endpoint profiling, NAC helps safeguard enterprise networks against unauthorized access and evolving cyber threats.
AAA vs NAC: Feature Comparison and Use Cases
AAA (Authentication, Authorization, and Accounting) primarily manages user access control, ensuring secure authentication and tracking user activity in network environments, while NAC (Network Access Control) enforces security policies by assessing device compliance before granting network access. AAA excels in user identity verification and access management across various network devices and services, making it ideal for user-centric environments; NAC focuses on endpoint security, assessing device posture, and enforcing policies to prevent unauthorized or non-compliant devices from connecting. Use cases for AAA include remote access VPN authentication and enterprise network login, whereas NAC is best suited for enforcing endpoint compliance, guest network control, and mitigating threats from potentially compromised devices.
Security Benefits of AAA and NAC in Network Management
AAA (Authentication, Authorization, and Accounting) enhances network security by ensuring only verified users access resources, enforcing permissions based on roles, and maintaining detailed access logs for audit trails. NAC (Network Access Control) strengthens protection by dynamically assessing device compliance with security policies before granting network access, preventing unauthorized or vulnerable devices from connecting. Together, AAA and NAC create a robust security framework that mitigates risks, enforces access policies, and ensures network integrity through continuous monitoring and control.
Challenges in Deploying AAA and NAC Solutions
Deploying AAA (Authentication, Authorization, and Accounting) and NAC (Network Access Control) solutions presents challenges such as integrating diverse network devices, ensuring scalability across large enterprise environments, and managing complex policy enforcement without impacting user experience. Both systems require robust infrastructure to handle real-time authentication and authorization decisions while maintaining network performance and security compliance. Compatibility issues with legacy systems and evolving cyber threats further complicate deployment and ongoing management of AAA and NAC frameworks.
AAA and NAC: Best Practices for Optimal Network Security
AAA (Authentication, Authorization, and Accounting) and NAC (Network Access Control) are essential components for robust network security, where AAA manages user identity verification and access rights, while NAC enforces policy compliance before granting network access. Implementing AAA with strong multi-factor authentication and comprehensive logging enhances accountability and traceability, while integrating NAC ensures endpoint compliance and real-time threat detection. Combining AAA protocols such as RADIUS or TACACS+ with NAC solutions that support device posture assessment and dynamic remediation optimizes access control and minimizes security risks.
Future Trends: Evolving Roles of AAA and NAC in Technology Networking
Future trends in networking show AAA (Authentication, Authorization, and Accounting) evolving with enhanced integration of AI-driven analytics for real-time security monitoring. NAC (Network Access Control) is advancing through adaptive access policies that utilize machine learning to assess device behavior and risk dynamically. The convergence of AAA and NAC technologies will drive more intelligent, context-aware network access management, improving scalability and threat response in increasingly complex network environments.
AAA vs NAC Infographic
 techiny.com
techiny.com