Access Control Lists (ACLs) filter network traffic based on IP addresses, protocols, and ports, providing basic, rule-based security at the router or switch level. Firewall rules offer more advanced filtering options, including stateful inspection, application-layer filtering, and the ability to block or allow traffic based on user identity or behavior. Both ACLs and firewall rules play crucial roles in network security, but firewalls provide deeper inspection and more granular control compared to the simpler, static filtering of ACLs.
Table of Comparison
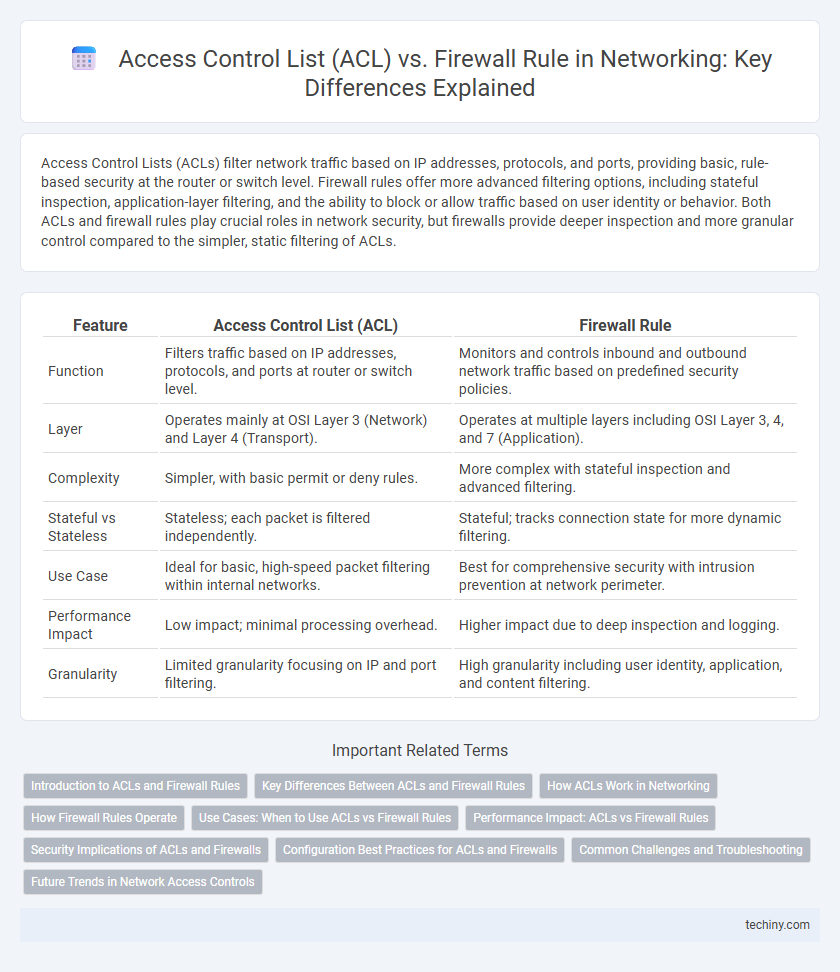
| Feature | Access Control List (ACL) | Firewall Rule |
|---|---|---|
| Function | Filters traffic based on IP addresses, protocols, and ports at router or switch level. | Monitors and controls inbound and outbound network traffic based on predefined security policies. |
| Layer | Operates mainly at OSI Layer 3 (Network) and Layer 4 (Transport). | Operates at multiple layers including OSI Layer 3, 4, and 7 (Application). |
| Complexity | Simpler, with basic permit or deny rules. | More complex with stateful inspection and advanced filtering. |
| Stateful vs Stateless | Stateless; each packet is filtered independently. | Stateful; tracks connection state for more dynamic filtering. |
| Use Case | Ideal for basic, high-speed packet filtering within internal networks. | Best for comprehensive security with intrusion prevention at network perimeter. |
| Performance Impact | Low impact; minimal processing overhead. | Higher impact due to deep inspection and logging. |
| Granularity | Limited granularity focusing on IP and port filtering. | High granularity including user identity, application, and content filtering. |
Introduction to ACLs and Firewall Rules
Access Control Lists (ACLs) are network layer security tools that filter traffic by permitting or denying packets based on IP addresses, protocols, and ports, primarily applied on routers and switches. Firewall rules provide more granular control over inbound and outbound traffic by inspecting packet headers and, in advanced cases, application layer data, allowing for stateful or stateless filtering. Both ACLs and firewall rules are fundamental for enforcing network security policies, with ACLs often used for basic filtering and firewalls offering comprehensive protection including intrusion prevention and traffic monitoring.
Key Differences Between ACLs and Firewall Rules
Access Control Lists (ACLs) operate primarily at the IP address and port level to filter traffic within routers or switches, focusing on permit or deny decisions based on predefined criteria. Firewall rules provide a more comprehensive security layer, inspecting traffic at multiple layers including application level, allowing for advanced filtering based on protocol, user identity, and content. While ACLs excel in high-speed, low-complexity filtering inside networks, firewall rules offer granular control and logging capabilities essential for perimeter defense and threat management.
How ACLs Work in Networking
Access Control Lists (ACLs) operate by filtering network traffic based on specified criteria such as IP addresses, protocols, and ports, enabling granular control over data packets entering or leaving a network interface. ACLs are implemented at routers or switches to enforce security policies by permitting or denying traffic flows according to predefined access rules. Unlike firewall rules, ACLs primarily function at Layer 3 and Layer 4 of the OSI model, providing efficient traffic filtering with lower overhead in high-speed networks.
How Firewall Rules Operate
Firewall rules operate by inspecting network traffic based on predefined criteria such as IP addresses, ports, protocols, and connection states to allow or deny data packets. These rules are applied at various layers of the OSI model, primarily focusing on packet filtering, stateful inspection, and application-layer filtering for enhanced security. The flexibility of firewall rules enables granular control over network traffic, enabling organizations to enforce security policies and prevent unauthorized access effectively.
Use Cases: When to Use ACLs vs Firewall Rules
Access Control Lists (ACLs) are ideal for filtering traffic within internal networks or on network devices like routers and switches, enabling precise control over packet forwarding based on IP addresses and protocols. Firewall rules are better suited for perimeter security, inspecting traffic at different OSI layers and enforcing more complex policies such as user authentication and stateful inspection. Use ACLs for lightweight, high-speed filtering on trusted networks and firewall rules for comprehensive threat prevention and policy enforcement at network boundaries.
Performance Impact: ACLs vs Firewall Rules
Access Control Lists (ACLs) typically offer faster packet filtering due to their placement on routers and switches with minimal processing overhead, optimizing network traffic handling. Firewall rules, implemented on dedicated devices with deeper inspection capabilities, introduce higher latency as they perform stateful inspection and apply complex security policies. Network performance can be impacted more significantly by firewall rules because of their comprehensive analysis compared to the generally stateless and streamlined processing of ACLs.
Security Implications of ACLs and Firewalls
Access Control Lists (ACLs) enforce security by filtering traffic based on IP addresses, protocols, and ports, providing granular control at the router or switch level but lacking deep packet inspection capabilities. Firewalls offer enhanced security through stateful inspection, application-layer filtering, and intrusion prevention, effectively detecting and blocking complex threats. ACLs serve as efficient first-line defenses primarily for traffic segregation, while firewalls deliver comprehensive threat mitigation to protect network integrity.
Configuration Best Practices for ACLs and Firewalls
Configuring Access Control Lists (ACLs) and firewall rules requires precise definition of traffic parameters such as IP addresses, protocols, and port numbers to enforce granular network access control. Best practices include ordering rules from most specific to least specific, minimizing rule overlap to reduce processing overhead, and regularly auditing policies to eliminate redundant or obsolete entries. Leveraging centralized management tools and consistent naming conventions enhances maintainability and ensures policies align with organizational security frameworks.
Common Challenges and Troubleshooting
Access Control Lists (ACLs) and Firewall Rules often present common challenges such as overlapping rules causing unintended traffic blocks or permit, and difficulty in rule order management leading to inconsistent security enforcement. Troubleshooting involves meticulous rule auditing and monitoring traffic logs to identify rule conflicts or gaps, with ACLs typically requiring command-line verification while firewall rules benefit from graphical interface tools for easier diagnostics. Ensuring synchronized policy updates and clear documentation helps prevent misconfigurations, which are frequent sources of network access issues in both ACLs and firewall implementations.
Future Trends in Network Access Controls
Future trends in network access controls emphasize AI-driven Access Control Lists (ACLs) and dynamic firewall rules that adapt in real-time to emerging threats. The integration of machine learning algorithms enhances predictive security measures by analyzing traffic patterns and automating rule updates. Cloud-native firewall solutions combined with zero-trust models are set to redefine ACL and firewall rule management for scalable, granular access control across hybrid environments.
Access Control List (ACL) vs Firewall Rule Infographic
 techiny.com
techiny.com