A DMZ (Demilitarized Zone) acts as a buffer zone between an internal network and untrusted external networks, typically hosting public-facing services to isolate them from the secure internal network. Firewalls enforce security policies by filtering incoming and outgoing traffic based on predefined rules, controlling access to and from the network. While a DMZ provides segmented exposure to the internet, a firewall serves as the main barrier protecting the internal network from unauthorized access.
Table of Comparison
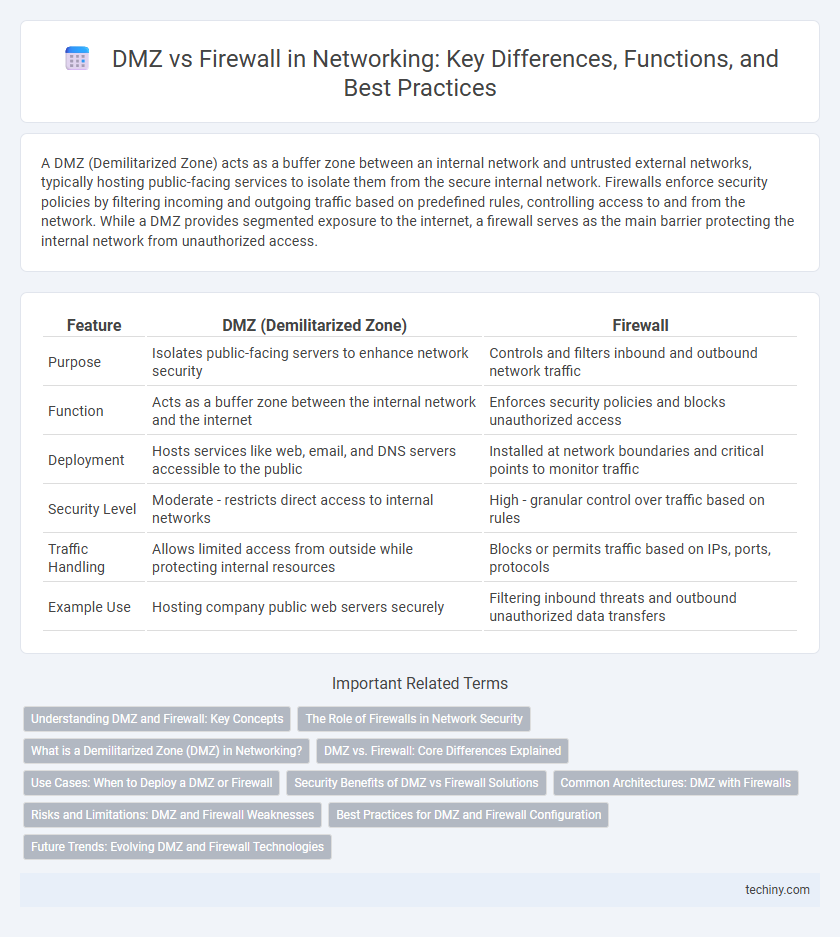
| Feature | DMZ (Demilitarized Zone) | Firewall |
|---|---|---|
| Purpose | Isolates public-facing servers to enhance network security | Controls and filters inbound and outbound network traffic |
| Function | Acts as a buffer zone between the internal network and the internet | Enforces security policies and blocks unauthorized access |
| Deployment | Hosts services like web, email, and DNS servers accessible to the public | Installed at network boundaries and critical points to monitor traffic |
| Security Level | Moderate - restricts direct access to internal networks | High - granular control over traffic based on rules |
| Traffic Handling | Allows limited access from outside while protecting internal resources | Blocks or permits traffic based on IPs, ports, protocols |
| Example Use | Hosting company public web servers securely | Filtering inbound threats and outbound unauthorized data transfers |
Understanding DMZ and Firewall: Key Concepts
A DMZ (Demilitarized Zone) is a physical or logical subnetwork that separates an internal local area network (LAN) from untrusted networks, typically the internet, providing an additional layer of security by isolating external-facing services. Firewalls are security devices or software that enforce network policies by filtering incoming and outgoing traffic based on predefined rules, controlling access between different network segments. Understanding the complementary roles of DMZs and firewalls is crucial for designing robust network architectures that minimize attack surfaces while ensuring controlled access to critical resources.
The Role of Firewalls in Network Security
Firewalls serve as a critical security barrier that monitors and controls incoming and outgoing network traffic based on predetermined security rules, effectively preventing unauthorized access to internal networks. In contrast, a DMZ (Demilitarized Zone) acts as a separate network segment that hosts public-facing services, providing an additional layer of defense by isolating these services from the internal network. By enforcing strict traffic filtering and protocol inspections, firewalls ensure that only legitimate and safe communications traverse between the DMZ, the internal network, and external sources, thereby enhancing overall network security posture.
What is a Demilitarized Zone (DMZ) in Networking?
A Demilitarized Zone (DMZ) in networking is a physical or logical subnet that separates an internal local area network (LAN) from untrusted external networks, typically the internet. It adds an additional layer of security by isolating public-facing services such as web servers, mail servers, and DNS servers, minimizing the risk of external attacks reaching the internal network. Unlike a firewall, which controls and filters incoming and outgoing traffic, a DMZ acts as a buffer zone that limits exposure and contains potential threats outside the secure internal network.
DMZ vs. Firewall: Core Differences Explained
A DMZ (Demilitarized Zone) is a physical or logical subnet that separates an internal local area network (LAN) from untrusted external networks, typically the internet, providing an additional layer of security by isolating public-facing services. A firewall is a security device or software that monitors and controls incoming and outgoing network traffic based on predetermined security rules, acting as a gatekeeper between networks. The core difference lies in their function: the DMZ serves as a buffer zone hosting external-facing servers, while the firewall enforces security policies and traffic filtering between the DMZ, internal network, and the internet.
Use Cases: When to Deploy a DMZ or Firewall
Deploy a DMZ is ideal for hosting public-facing services such as web servers, email servers, and DNS servers, providing an additional layer of security by isolating these services from the internal network. Firewalls are essential for regulating inbound and outbound traffic based on predefined security rules, protecting the internal network from unauthorized access and cyber threats. Use a DMZ when separating external services from sensitive internal resources is critical, and deploy firewalls to control and monitor network traffic at various entry and exit points.
Security Benefits of DMZ vs Firewall Solutions
A DMZ (Demilitarized Zone) creates a buffer zone between an internal network and untrusted external networks, enhancing security by isolating public-facing services and reducing the attack surface. Firewalls primarily enforce access control policies by filtering traffic based on predetermined rules, protecting the internal network from unauthorized access. Combining DMZ and firewall solutions offers layered security, with the DMZ handling external-facing resources and firewalls managing inbound and outbound traffic, thereby strengthening threat containment and minimizing lateral movement risks.
Common Architectures: DMZ with Firewalls
A common network architecture places the DMZ between two firewalls, creating an additional layer of security by isolating external-facing services from the internal network. The external firewall filters incoming traffic from the internet to the DMZ, while the internal firewall restricts traffic between the DMZ and internal systems, preventing lateral movement in case of compromise. This dual-firewall setup enhances protection for web servers, email servers, and other public-facing applications by tightly controlling access and minimizing attack surfaces.
Risks and Limitations: DMZ and Firewall Weaknesses
DMZs expose internal networks to external threats by hosting public-facing servers, increasing the risk of unauthorized access if improperly configured. Firewalls can have vulnerabilities such as misconfigured rules or outdated firmware, which attackers exploit to bypass security controls. Both DMZ and firewall structures require continuous monitoring and updates to mitigate risks and prevent potential breaches.
Best Practices for DMZ and Firewall Configuration
Optimal DMZ and firewall configuration requires isolating public-facing servers within the DMZ to limit exposure to internal networks while enforcing strict access controls through firewalls. Implement network segmentation by deploying firewalls at both the perimeter and between the DMZ and internal network, applying rules that minimize allowed traffic based on the principle of least privilege. Regularly update firewall policies and monitor DMZ traffic to detect anomalies and prevent unauthorized access, ensuring robust protection for sensitive internal resources.
Future Trends: Evolving DMZ and Firewall Technologies
Future trends in networking emphasize the convergence of DMZ and firewall technologies through advanced AI-driven threat detection and automated response systems, enhancing perimeter security. Zero Trust Network Access (ZTNA) frameworks are increasingly integrated within DMZ architectures to minimize lateral movement and enforce granular access controls. Innovations in cloud-native firewalls and micro-segmentation simplify complex hybrid environments, optimizing security posture against evolving cyber threats.
DMZ vs Firewall Infographic
 techiny.com
techiny.com