MAC filtering enhances network security by allowing only devices with specific MAC addresses to connect, effectively blocking unauthorized devices. Port security, on the other hand, restricts access at the switch port level by limiting the number of MAC addresses learned, preventing MAC flooding attacks. Both techniques complement each other in securing network environments by controlling device access and mitigating potential threats.
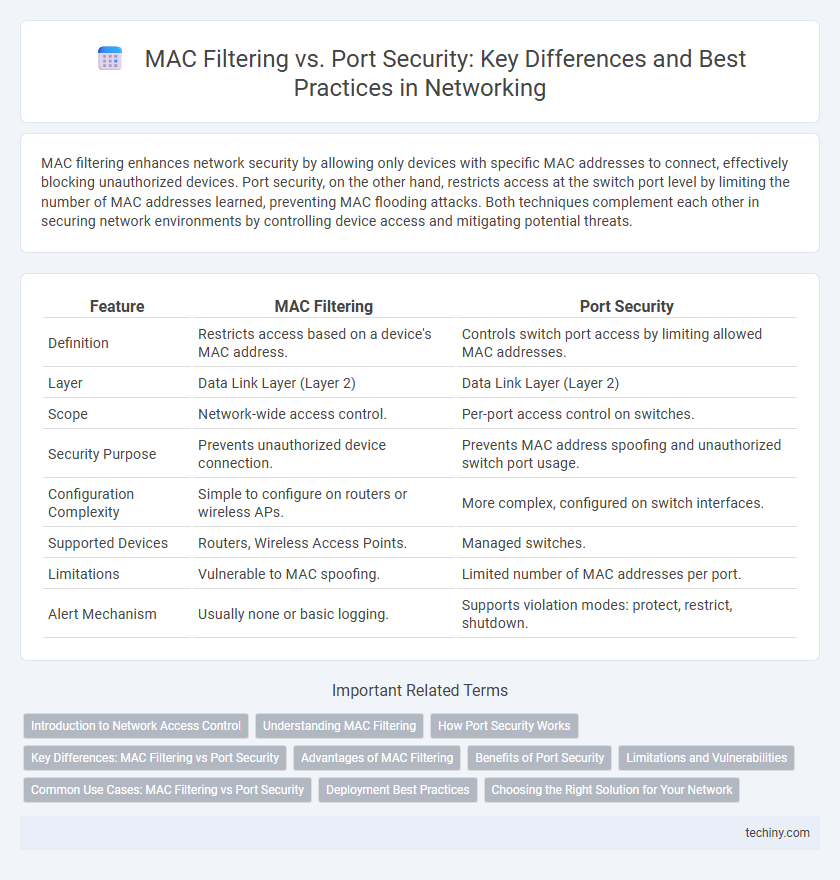
Table of Comparison
| Feature | MAC Filtering | Port Security |
|---|---|---|
| Definition | Restricts access based on a device's MAC address. | Controls switch port access by limiting allowed MAC addresses. |
| Layer | Data Link Layer (Layer 2) | Data Link Layer (Layer 2) |
| Scope | Network-wide access control. | Per-port access control on switches. |
| Security Purpose | Prevents unauthorized device connection. | Prevents MAC address spoofing and unauthorized switch port usage. |
| Configuration Complexity | Simple to configure on routers or wireless APs. | More complex, configured on switch interfaces. |
| Supported Devices | Routers, Wireless Access Points. | Managed switches. |
| Limitations | Vulnerable to MAC spoofing. | Limited number of MAC addresses per port. |
| Alert Mechanism | Usually none or basic logging. | Supports violation modes: protect, restrict, shutdown. |
Introduction to Network Access Control
MAC filtering and port security are critical components of network access control designed to restrict unauthorized devices from connecting to a network. MAC filtering enforces access by allowing or denying devices based on their unique MAC addresses, providing a straightforward but less dynamic method. Port security enhances this by limiting the number of devices that can connect to a network port and can dynamically learn MAC addresses, offering stronger protection against unauthorized access and MAC spoofing.
Understanding MAC Filtering
MAC filtering enhances network security by allowing or denying devices based on their unique Media Access Control (MAC) addresses, effectively controlling access at the data link layer. This method prevents unauthorized devices from connecting to a network by maintaining a whitelist or blacklist of MAC addresses. Unlike port security, which limits device connections on individual switch ports, MAC filtering provides a broader approach to device authentication in wireless and wired environments.
How Port Security Works
Port security works by limiting access to a physical switch port based on MAC addresses, allowing network administrators to specify which devices are permitted to connect. When an unauthorized device attempts to access the port, the switch can take actions such as shutting down the port, dropping packets, or logging the event. This mechanism enhances network security by preventing unauthorized devices from communicating on the LAN, effectively controlling access at the hardware level.
Key Differences: MAC Filtering vs Port Security
MAC Filtering controls network access by allowing or blocking devices based on their unique MAC addresses, typically implemented on wireless routers or switches to restrict unauthorized devices. Port Security operates on switch ports to limit the number of MAC addresses or specify which MAC addresses can send frames through a port, helping prevent MAC flooding attacks and unauthorized access. While MAC Filtering focuses on device identification, Port Security enhances protection by enforcing connection policies at the physical switch port level.
Advantages of MAC Filtering
MAC filtering enhances network security by allowing administrators to specify which devices can access the network based on their unique MAC addresses, effectively preventing unauthorized connections. It simplifies network management by providing a straightforward method to control device access without requiring complex configurations. This technique is particularly advantageous in small to medium-sized networks where device identity verification is critical for maintaining a secure environment.
Benefits of Port Security
Port Security enhances network protection by restricting device access based on MAC addresses, preventing unauthorized entry and mitigating MAC flooding attacks. It allows granular control over switch ports, enabling administrators to specify a maximum number of permissible devices, thus reducing the risk of network breaches. Compared to MAC Filtering, Port Security provides dynamic, real-time enforcement and automated responses to security violations, improving overall network integrity.
Limitations and Vulnerabilities
MAC filtering is limited by its reliance on hardware addresses, which can be easily spoofed by attackers, reducing its effectiveness in preventing unauthorized access. Port security, while more robust by restricting the number of valid MAC addresses on a switch port, can be vulnerable to MAC flooding attacks that exhaust the MAC address table, causing legitimate devices to be denied access. Both techniques lack dynamic adaptability to sophisticated intrusions and require ongoing management to maintain network security integrity.
Common Use Cases: MAC Filtering vs Port Security
MAC filtering is commonly used in wireless networks to restrict access based on device MAC addresses, enhancing control over which devices can connect to the network. Port security, primarily implemented on switches, prevents unauthorized access by limiting the number of MAC addresses per port and can dynamically learn or statically assign allowed addresses. Typical use cases for MAC filtering involve small-scale access control in home or small office networks, while port security is favored in enterprise environments to protect network infrastructure from unauthorized devices and reduce the risk of MAC flooding attacks.
Deployment Best Practices
MAC filtering is best deployed on smaller networks or guest Wi-Fi environments where ease of management is critical, limiting access based on device MAC addresses. Port security, optimized for enterprise switches, enforces stricter policies by locking specific ports to known MAC addresses and dynamically preventing unauthorized devices, effectively reducing spoofing risks. Combining MAC filtering with port security enhances overall network defense by providing layered access control tailored to both device identification and physical connection points.
Choosing the Right Solution for Your Network
MAC filtering offers a straightforward method to control network access by allowing or blocking devices based on their MAC addresses, making it suitable for smaller networks with limited device variability. Port security enhances protection by enabling dynamic or static locking of specific switch ports, restricting connections to authorized MAC addresses and preventing unauthorized device access in complex or enterprise environments. Network administrators should evaluate factors like scalability, management complexity, and security requirements to select the optimal solution that balances control and operational efficiency.
MAC Filtering vs Port Security Infographic
 techiny.com
techiny.com