VLANs segment local networks by tagging Ethernet frames to separate traffic within a single Layer 2 domain, ideal for small to medium-sized environments. VXLAN extends VLAN functionality over Layer 3 networks by encapsulating Ethernet frames within UDP packets, enabling scalable, multi-tenant data center networking and efficient network virtualization. VXLAN overcomes VLAN limitations by providing a larger address space and traffic isolation across geographically dispersed sites.
Table of Comparison
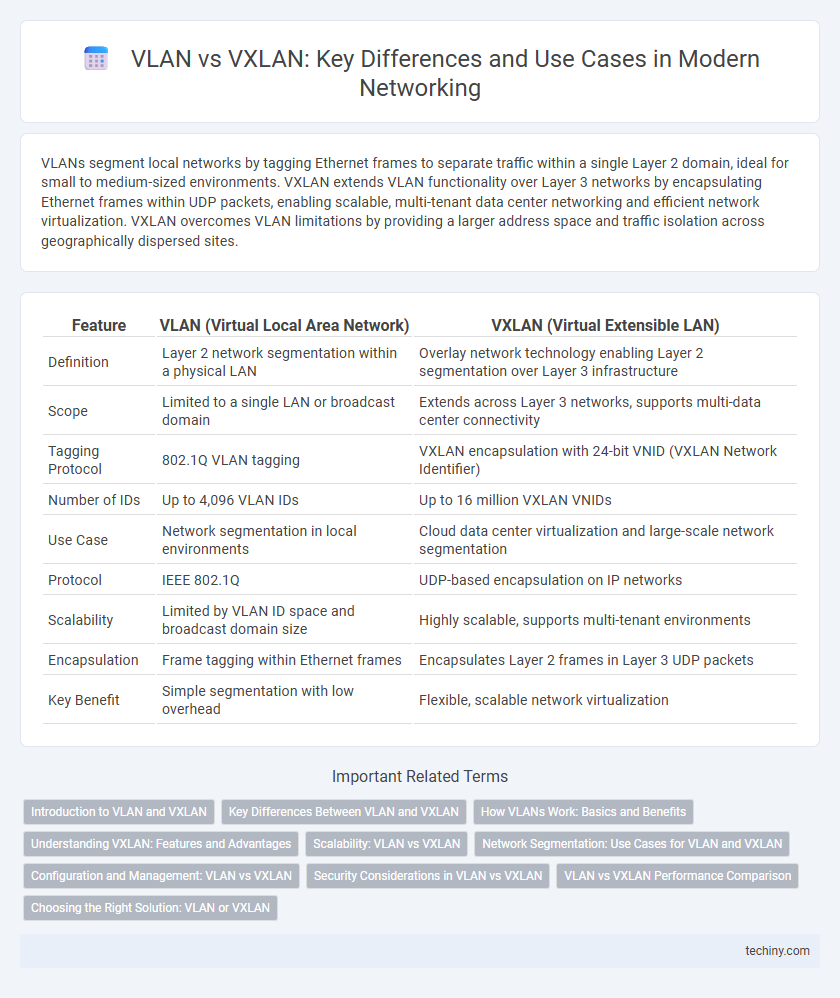
| Feature | VLAN (Virtual Local Area Network) | VXLAN (Virtual Extensible LAN) |
|---|---|---|
| Definition | Layer 2 network segmentation within a physical LAN | Overlay network technology enabling Layer 2 segmentation over Layer 3 infrastructure |
| Scope | Limited to a single LAN or broadcast domain | Extends across Layer 3 networks, supports multi-data center connectivity |
| Tagging Protocol | 802.1Q VLAN tagging | VXLAN encapsulation with 24-bit VNID (VXLAN Network Identifier) |
| Number of IDs | Up to 4,096 VLAN IDs | Up to 16 million VXLAN VNIDs |
| Use Case | Network segmentation in local environments | Cloud data center virtualization and large-scale network segmentation |
| Protocol | IEEE 802.1Q | UDP-based encapsulation on IP networks |
| Scalability | Limited by VLAN ID space and broadcast domain size | Highly scalable, supports multi-tenant environments |
| Encapsulation | Frame tagging within Ethernet frames | Encapsulates Layer 2 frames in Layer 3 UDP packets |
| Key Benefit | Simple segmentation with low overhead | Flexible, scalable network virtualization |
Introduction to VLAN and VXLAN
VLAN (Virtual Local Area Network) segments a physical network into multiple logical networks to improve traffic management and security within Layer 2 domains. VXLAN (Virtual Extensible LAN) extends VLAN capabilities by encapsulating Layer 2 frames within Layer 3 packets, enabling scalable network virtualization across large data centers and cloud environments. Both technologies facilitate network segmentation, with VLANs limited by 4096 IDs and VXLAN supporting up to 16 million unique identifiers.
Key Differences Between VLAN and VXLAN
VLAN (Virtual Local Area Network) operates at the Layer 2 level, segmenting network traffic within a single physical network using 12-bit VLAN IDs, limiting the number of unique VLANs to 4096. VXLAN (Virtual Extensible LAN) extends Layer 2 networks over Layer 3 infrastructure by encapsulating Ethernet frames within UDP packets and uses a 24-bit VNID, allowing up to 16 million unique segments, ideal for large-scale data centers and cloud environments. Key differences include VLAN's limited scalability and reliance on physical switches versus VXLAN's support for greater scalability, multi-tenancy, and seamless Layer 2 extension across geographically dispersed networks.
How VLANs Work: Basics and Benefits
VLANs (Virtual Local Area Networks) segment a physical network into multiple logical networks by tagging Ethernet frames with VLAN IDs, enabling isolation and enhanced security within the same switch infrastructure. Each VLAN operates as an independent broadcast domain, reducing network congestion and improving traffic management. VLANs simplify network administration by allowing flexible device grouping regardless of physical location, making them ideal for separating departments or user groups within an enterprise.
Understanding VXLAN: Features and Advantages
VXLAN (Virtual Extensible LAN) extends traditional VLAN limitations by supporting up to 16 million logical networks compared to VLAN's 4,096, enabling scalable multi-tenant environments in data centers. It encapsulates Layer 2 frames within Layer 3 UDP packets, facilitating seamless network segmentation over IP-based networks and improving network flexibility and VM mobility. VXLAN's overlay architecture enhances network isolation and simplifies the deployment of virtualized infrastructures, making it ideal for cloud and large-scale enterprise networks.
Scalability: VLAN vs VXLAN
VLAN scalability is limited by the 12-bit VLAN ID field, supporting up to 4096 unique VLANs, which constrains large-scale enterprise networks. VXLAN uses a 24-bit segment ID called VNI, enabling up to 16 million unique segments, making it ideal for massive data centers and cloud environments. This expanded scalability allows VXLAN to overcome VLAN's limitations in complex, multi-tenant network architectures.
Network Segmentation: Use Cases for VLAN and VXLAN
VLANs (Virtual Local Area Networks) provide efficient network segmentation within a single Layer 2 domain, ideal for small to medium-sized enterprise environments where simplicity and cost-effectiveness are priorities. VXLAN (Virtual Extensible LAN) extends segmentation capabilities across Layer 3 networks, supporting large-scale data center and cloud architectures by enabling millions of isolated tenant networks over IP-based infrastructure. Use cases for VLAN focus on segregating traffic on physical switches in LANs, while VXLAN is essential for scalable multi-tenant environments requiring seamless communication across distributed sites.
Configuration and Management: VLAN vs VXLAN
VLAN configuration uses simple tagging protocols such as IEEE 802.1Q, typically managed through traditional switches and centralized controllers, offering straightforward setup within local networks. VXLAN configuration involves encapsulating Layer 2 frames within UDP packets using a 24-bit segment ID, requiring overlay network controllers and increased orchestration for managing scalability across data centers. Management of VLANs remains limited to smaller domains, while VXLAN supports complex, multi-tenant environments with enhanced automation and integration capabilities via software-defined networking (SDN) tools.
Security Considerations in VLAN vs VXLAN
VLANs isolate network segments by using 802.1Q tagging, but their limited VLAN ID space and reliance on Layer 2 security make them vulnerable to VLAN hopping and MAC spoofing attacks. VXLAN provides enhanced security through encapsulation with a 24-bit segment ID, enabling greater scalability and segmentation, while supporting robust tunneling protocols that limit broadcast domain exposure. However, VXLAN requires proper encryption and authentication mechanisms like IPsec or MACsec to protect against threats such as unauthorized tunneling and data interception in multi-tenant environments.
VLAN vs VXLAN Performance Comparison
VLANs offer low-latency performance ideal for small to medium-sized networks but are limited by a 12-bit VLAN ID, restricting scalability to 4096 VLANs. VXLAN uses a 24-bit segment ID, enabling over 16 million isolated networks, which introduces additional encapsulation overhead and slightly higher latency compared to VLANs. In large-scale data centers requiring extensive segmentation and multi-tenant environments, VXLAN delivers superior scalability and flexibility despite its marginal performance trade-offs.
Choosing the Right Solution: VLAN or VXLAN
Choosing between VLAN and VXLAN depends on the scale and flexibility required in the network environment. VLANs offer simple, effective segmentation for smaller, traditional LANs with up to 4096 IDs, while VXLAN supports larger-scale, multi-tenant data centers by encapsulating Layer 2 traffic over Layer 3 networks using a 24-bit VXLAN Network Identifier (VNI) that allows up to 16 million segments. Network architects prioritize VXLAN for cloud, virtualized, and geographically dispersed environments where scalability and isolation are critical, whereas VLANs remain suitable for straightforward, flat network designs with limited segmentation needs.
VLAN vs VXLAN Infographic
 techiny.com
techiny.com